The Design of Electric Bicycle Self-Charging Station Systems.
Diunggah oleh
jcseukJudul Asli
Hak Cipta
Format Tersedia
Bagikan dokumen Ini
Apakah menurut Anda dokumen ini bermanfaat?
Apakah konten ini tidak pantas?
Laporkan Dokumen IniHak Cipta:
Format Tersedia
The Design of Electric Bicycle Self-Charging Station Systems.
Diunggah oleh
jcseukHak Cipta:
Format Tersedia
Journal of Computational Science and Engineering
www.jcseuk.com
2050-2311/Copyright 2012 IE Enterprises ltd All right reserved
Jour. of Comp. Sci. and Eng.
Vol. 1, Num.1, 00180027, 2012
The Design of Electric Bicycle Self-charging Station Systems
Jiajia Wanga, Yutao Sunb,b*
b
Anhui University of Finance and Economics, Literature and Media School, Bengbu 233000, China Anhui University of Finance and Economics, Management Science and Engineering School, Bengbu 233000, China
Abstract
In view of the current situation of scattered electric bicycle charging stations and their non-unified management, this paper analyzes the possibility and development prospects of establishing self-charging stations through the following aspects: weakness of current electric bikes charging mode, demands analysis of self-charging system, data analysis of the current system, technical support of the system design, design and application of self-charging system etc.
KeywordsElectric bikeCharging stationSystemSelf-help
1.Introduction
Nowadaysthere are many different kinds of self-charging stations on the market for electric bikes, for example: coin style stations, card swiping style stations etc. but all of these charging stations need to be managed by people, when organizations install stations in large amounts the operation becomes quite difficult to manage; therefore, establishing a database management system is a very prudent idea. In addition, if those charging stations were the same as Automatic Teller Machines people could recharge according to their needs and at the same time agents would be able to see the earnings on their computers via the database system and decide whether to keep or change the station locations, according to the earnings. [1]
* Corresponding author. Yutao Sun E-mail address: 27717686@qq.com
September 2012
Jiajia Wang et al / Journal of Computational Science and Engineering 1:1 (2012) 00180027
2. Business Outline
2.1. Introduction of traditional business process mode Electric bike charging stations are becoming increasingly popular in small and medium-sized cities, there are more and more locations installing the charging stations. Currently, many agents are using a fairly inefficient method for checking the stations takings, that is; to go to the locations and check the machines regularly, it goes without saying that the work load involved could potentially be massive if there are relatively large amounts of installations. For the consumers, the coin style charging stations can also present the awkward situation where by customers attempt to use the charging stations and then realize that they do not have sufficient coins. All of these issues have helped to identify the possibility for the application of the self-charging system[2][3]. 2.2. The application of self-charging system Self-help systems are used by people comprehensively every day, for example, systems such as ATMs and self-inquiry systems in customer service centres are now common place and we can obviously see the speed and effectiveness of these self-help systems. Introducing a self-charging system will greatly benefit the users of electric bicycles, achieving the integration from charging money to charging electricity. [5] At the same time, the system can provide a 24 hour service to the consumers. The system centralizes the scattered information into different classifications, achieves category management etc. through using computer technology. The system can achieve inquiry results, updates and save inquiry result functions efficiently and conveniently.
3. System Requirements
3.1. System overall requirements Some of the key targets that the self-charging system needs to achieve are: development of databases and advanced development platforms, use of existing software, configuring of certain required hardware, developing a management system which has an open system structure, easy expansion, easy maintainability with a good human-computer interactive interface, provide agents with accurate and efficient information in order to facilitate management to make the final decision. According to feasibility research and users requirements and based on the existing conditions and problems the system uses the C/S structure to facilitate the users and managers [4]. 3.2. System Function Requirement The system is equipped with: a landing module, charging station management module, administrator information management module, charging station information management module, user Information Management Module, rights management module, password change module seven parts. The main goal of this system is to achieve systematic, standardized and automated charging management. The purpose of the development of the system is to improve the administrators work efficiency, below are explanations of the main functions: (1) User landing module: Users can only enter the system main interface after selecting appropriate user name and inputting a correct password, and operating within the scope of privileges allowed. (2) Charging station management module: The main purpose of the charging station management module is to increase the number of charging stations, modifying the number values in the original charging station information table and entering the results into the charging station information table. (3) Administrator information management module: The main purpose of the administrator information management module is increasing, modifying and deleting administrator information, administrator information inquiry and report form generating (Output query results in tabular form). (4) Charging station information management module: increasing, editing, deleting and updating charging station information, charging station finding (using the charging station serial number as a means for location), report form generating (Output query results in tabular form).
Jiajia Wang et al / Journal of Computational Science and Engineering 1:1 (2012) 00180027
(5) User information management module: increasing, modifying and deleting user information, user information inquiry (find user information by user serial number or user name). (6) Right management module: managers can change the users permissions for using the system, which include: increasing, deleting and modifying the limits of authority of users. (7) Password changing module: the users should change the code of the system to protect the authority and data. 3.3. System Function Requirement In order to guarantee that the system can operate permanently, safely, stably and effectively, a self-charging management system should satisfy the following functional requirements: A. Data Confidentiality The system is operating under the unified management of the highest administrator, the highest administrator has the highest authority of the system management, can enter all the system operations, which include: increasing and deleting administrators and all levels. System managers are divided as guest, basic operators (many employees), lower-level managers (many), senior manager (one boss) four categories, to achieve the right control of the system. B. Data security Using relatively strict calibration for the user to enter the system, the highest system administrator is responsible for data maintenance and data backup. C. Accuracy and Punctuality Accuracy and punctuality of system processes must be considered by the system. In the process of system design and development, the maximum possible workload which the system bears currently and will bear in the future needs to be considered, in order to make sure that the system process capability and response time can satisfy users requirements. D. Easy use and easy maintenance The operators may not be very familiar with computer systems therefore the system must be very user friendly and easy to operate (human-computer interactive interface). To achieve this, it requires the system developers to use terminology which the users are familiar with and Chinese information expressions, in addition, it is essential to provide a detailed help file for the possible problems that may occur in the use, reducing the time which users need to master the system. E. Standard Capacity The systems involved in the design process of the computer hardware and software knowledge are required to comply with international, national and industry standards. This facilitates not only the exchange amongst different developers but also the system maintenance. 3.4. Other Requirement In order to ensure that the system can meet the various needs, the system should also meet the following performance requirements: A. Openness and scalability Scalability in the system should be fully taken into account, needs of users are changing along with the development of the times, thus requiring the system developers to adjust and expand the functions according to the users needs, to achieve the openness of system is a solution. An open system, as long as it meets certain specifications, can complete the expansion of the system through a simple add or change of the system module. It also can improve the existing system functions by configuring new hardware and updating software, eventually adapting to the needs of both the era and the users. B. Advanced Nature With the ongoing developments in computer technology the system should ensure that it is advanced enough to remain competitive for a long time or at least for as long as possible. This can be achieved through the openness and scalability of the system, constantly improving and updating the functionality of the system and using the most modern software, which has strong growth prospects but takes into account the consideration of cost. C. response speed The response speed of the system in day-to-day transaction processing should be seconds; in order to achieve real-time results in providing feedback information promptly, the system needs to ensure that speed problems do not affect the working efficiency.
Jiajia Wang et al / Journal of Computational Science and Engineering 1:1 (2012) 00180027
4 System data analysis and design
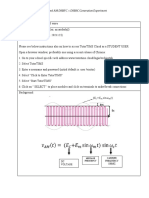
4.1. System data analysis In order to design the software effectively and conveniently, making the operation simple and efficient, the database must be designed to be relatively simple; a lot of operations are completed in a table with only a small degree of association between each table. Adding the database into the software development makes the operation quicker and more convenient, with the data analysis and the data process procedure determining the entities, characteristics and the connections between the entities in the system. The systems E-R chart is as follows:
PK id name identity address tel
Fig. 1. System E-R Chart
PK,FK1 id consumeStartTime consumeEndTime Value Cardid
PK Cardid residueValue totalValue userID
PK,FK1 Cardid address totalValue totaltime
FK2
4.2. System database design 4.2.1 The environmental configuration instruction of system database design. This system uses the SQL database, the edition is SQL Server2000. The pre-condition of the database design meets the three paradigm requirement, the data model is very simple, using data attributes of an entity only to describes this entity; Data non-redundant, each data attribute (except outside) only belongs to one entity; The data model is used flexibly to respond to future demand changes and not simply designed for today's development needs. The database design follows the integrity of the entity, data and user-defined, to guarantee safe input and modify of data. [6] The system uses Microsoft Visio2003n as the tool of database design. 4.2.2 Data table and its structure According to the requirements of the system E-R chart and system design, 4 data tables are required in the design for the self-charging management system database, they are: user information table, user card information table, card consuming record, charging station information table, [8] they are shown as following:
Table 1. User information table
Field id name identity address tel Table 2. User card information table Field Cardid
Category integer Char Char Char Char
Explanation
Note Primary Key
Name Identity Number Address Contact telephone no
Category integer
Explanation Serial Number
Note Primary Key
Jiajia Wang et al / Journal of Computational Science and Engineering 1:1 (2012) 00180027 residueValue totalValue userID Table 3. Card consuming record Field id consumeStartTime consumeEndTime Value Table 4. Charging station information table Field id address totalValue totaltime Category integer Char float Datetime Explanation Serial Number Address Total Amount Total Time Note Primary Key Category integer Datetime Datetime float Charging start time Charging finish time Charging amount Explanation Note Primary Key float float integer The residual amount Card total charged amount Holder Foreign Key
5. System function analysis and design
5.1. Structure analysis of system function
Fig. 2. Structure of system function
5.2. Analysis of system business process Administrators input the information of the administrator, charging station and users etc. into the selfcharging system, the system will feedback the information to the administrator, users using the system can make inquiries and generate reports. In the process of use, administrators can increase, delete and modify information according to the needs. In addition, the system also can generate user information reports, charging station information reports and administrator information reports etc. 5.3 Structure design of system application Firstly, the structure application is used to achieve the standardized technology of information system. This system adopts C/S structure but any system should reflect on the following 5 layers: a. Presentation layer: Performance of user input and output
Jiajia Wang et al / Journal of Computational Science and Engineering 1:1 (2012) 00180027
b. The presentation of logic layer: Process which must be carried out in order to generate performance c. The application of logic layer: All the logic and processes which are needed to support the real business applications and regulation. d. Data process layer: All the commands and logic which are needed to store and visit the data of connected database. e. Data layer: The data which is actually stored in the database. The Client/Server system is a type of distributed computing program, where the presentation layer, the presentation logic layer, application logic layer, data processing layer and data layer are distributing between the client PC and one or more servers, the clients computer can be any combination of personal computer, workstation, laptop, pocket PC [7]. 5.4 The achievement and description of the system function module Through the detailed investigation and analysis of the system, self-charging management system should possess a few system function modules with each respective module being independent. This system uses a modulated design, giving the whole system strong operability and easy scalability. In the achievement of the system function relatively independent modules connected to each other through the data stream reduce the degree of coupling between each module, improving the operating speed and security of the system. The system has a landing module, charging station management module, administrator information management module, charging station information management module, user information management module, right management module, password alter module and help information module 8 parts. A brief description of each module follows: 5.4.1 Landing module This module is the connector between the user entering and using the software, setting up different management permissions to different users, people who have different limits of authority can use different functions, the highest system administrator has all of the authorities, the system permission category is broadly divided into four categories: the highest system administrator, advanced administrator, basic operator, the default minimum permissions--tourist visit. The module mainly completes the login and logout of the system. Login is to match the selected username and password with the existing username and password in the authority table, if they match; the logged-on user is given the appropriate permissions. The highest administrator can increase, modify and delete the information in the authority table, but all of the users (except passing guest) in the authority table can modify their password to aid in data security but only the highest administrator can operate the permission setting of each user. Implementation method: uses the AD0 method to connect the login to the database, uses ADO Query and ADO Table components to achieve the matching job which is whether the input of user name in the authority table and the username and password match the relevant field in the authority table, thus completing the authority management to different user. 5.4.2 Charging station management module This module is to manage the charging station. Every time one piece of information is added, the number in the corresponding information table should change with the change of the number in the module, completing the number of additions and subtractions. 5.4.3 Administrator information management module Mainly completes the operation of basic information of the administrator, this includes the operations of increasing, deleting and modifications of administrator information. In addition, the administrator information management module also can complete the query and output of administrator information, which includes name queries and serial number queries. Selecting different methods can generate different query results, thus it is easier to find. Module functions also include; exporting query results by Excel form format, completing output and storage of different query results. In addition, it generates dynamic name lookup when inquiring for the administrators name, it can complete the corresponding inquiry by entering only the first letter or a few key letters and this can reduce the information inputting time greatly, simplifying the operation.
Jiajia Wang et al / Journal of Computational Science and Engineering 1:1 (2012) 00180027
5.4.4 Charging station information management module The settings of the charging station information management module mainly include the serial number and name of the charging station, including an update on the charging station informationincreasing, deleting and modifying etc. basic operations. And it also uses the dynamic simplified inquiry operation on the inquiry function of the charging station information-- lookup by name and by serial number, the charging station information management module can also export and store the query results, it is convenient to store the different query results by category. 5.4.5 User information management module The settings within user information mainly include: user serial number, name, telephone number, address and identity number. It can increase, delete and modify the users information, the user information management module also performs report generation. 5.4.6 Authority management module Authority management module is designed for the highest administrator, it divided the operation system as passing guest, basic operator, information manager etc operator identity, give different authorities to different managers, allow them to complete the operations which are relative to their own identity. The highest administrator can also alter the authority control of each administrator according to the needs, they can even increase or delete user and change the users password. 5.4.7 Password modify module Can change the login password of any users (except passing guests), on one hand, it is convenient for users, acting as a reminder, helping them to remember. On the other hand, it guarantees the security of its own login. 5.4.8 Help information module Help information module completes the helping file according to the users need; it can transfer the helping information at any time to complete the relevant operation when users have any query about the operation, it can find out the useful information by a single click on show through entering a few letters of the word which you want to find.
6. System instructions for use
6.1. System installation and configuration instructions 6.1.1 The system operating environment Firstly, it should select the development tools and environments. The selection of development environment: The Delphi7.0 which the Boland has developed is based on the development tool of the Windows application program; it is the development tool which is widely used and easy to learn. Delphi7.0 provided a great amount of control, these controls can be used in the design of a friendly interface and achieve the various functions, reducing the workload of programmers greatly, at the same time simplifies the design process of the interface. This could effectively improve the operational efficiency of the application program. Therefore, Delphi7.0 is a relative good choice to achieve this system. SQLServer2000 which is used by this system is a RDBMS based on C/S module, it has higher reliability and we are going to use SQL Server 2000 as the database management system [9] [10]. 6.1.2 System installation steps
The system installation is very easy, a simple statement of the installation steps are as follows: a. Install SQL Server2000 database. Selecting self-defined installation when installing, single click on
Jiajia Wang et al / Journal of Computational Science and Engineering 1:1 (2012) 00180027
Server and client tools option, clear default Checkbox in Instance name dialogue and input new named instance name, selecting Typical or Minimum option in installation type dialogue box, accept default setting in sever account dialogue box, input domain password, use the mixed mode in the Authentication Mode dialog box, for example, use sa as username, password is 123, it can be modified in practical application at any time. b. Install directly under the installation wizard .
6.1.3 System Configuration
a. Hardware environment requirements ProcessorIntel Celeron or Compatible machine1 GHz or higher; MemoryWindows XP requires 256 MB; Windows 2000 requires 128 MB; available disk spaceat least 20MB; b. Operation systemAny of the following Microsoft Windows operation system With Service Pack 4; Windows Server 2003 Enterprise Edition; Windows Server 2003 Standard Edition; With Service Pack 2s Windows XP Home Edition; c. Database management system Microsoft SQL Server 2000 Enterprise Edition or Standard Edition; Microsoft SQL Server 2000 Developer Edition or Personal Edition.
6.2. System Operating Instructions 6.2.1 Landing module The users open the software, first appears the landing module, users can only enter the main interface by correctly entering their username and inputting the corresponding password, and single clicking on the confirm button, if any correct password is inputted or the selected username and password are inconsistent the system will automatically give tips, then user can single click on cancel to re-input. (Default settings: username=guest, password=empty). Landing interface is shown as figure 3.
Fig. 3. User landing interface
Users identify their user identification through the landing module and are given different authorities according to the different identities, entering the main window after correct identification; the system can complete all the operations of corresponding identities [11]. 6.2.2 Charging station management module After entering the charging station information management module, users can select the page to be edited according to their needs, they can complete the inputting of a record by a single click on the new button, complete a deleting operation by a single click on the delete button, they can also single click on the amend option to enter the editing state of the record. Also the charging station management module includes query and report generation.
Jiajia Wang et al / Journal of Computational Science and Engineering 1:1 (2012) 00180027
6.2.3 Authority management module The authority management module is the module set for top administrators; it can be used to authorize the increase, deletion, password changes, and permission changes of users. It is shown as figure 4.
Fig. 4. Authority management
6.2.4 Password change module
The password change module is a secure login to protect users (in addition to passing guests), on one hand users can change their password according to their own needs and on another hand it can prevent password disclosure. The Password change module interface is shown in figure 5.
Fig. 5. Authority management
Firstly, it matches the original password and the authority table in the database, next it resets the password if it is correct, it also gives information tips if this does not match, gives information tips if two reset password are different. 6.2.5 Help information module The help information module can be seen as : providing simple inquiry help to users, helping users understand and become familiar with the system in a short time period and operating it in an effective way. Interface is shown as figure 6.
Fig. 6. Authority management
Jiajia Wang et al / Journal of Computational Science and Engineering 1:1 (2012) 00180027
Acknowledgments The work is supported by Anhui University of Finance and Economics Scientific Research Project, Project Serial No: ACKYQ1229
References:
[1]Yi FengPreliminary study of an intelligent charging system[J]BeijingChina Agricultural University20004 [2]Jianhua Ying, Yabei Yang, Yueming Ding. Design of electric bike fast charging station [J]. 2011,(05) [3]Ku Wang, Yi Feng. Discussion of Fast Charge Technology [J]. Journal of China Agricultural University,2001, 6( 2) :6267 [4]Jian Wang, Jiuchun Jiang. Design and implementation of information management system for electric vehicle charging station [J]. Micro-computer information,2006,22(5):16-17 [5]LifangGuoIntelligent charging device and its control technology.[J].Nanjing: Hohai University,2003,4 [6] Shixuan SA.Introduction of Database Systems [M].Higher Education Press.2004,3. [7] Jeffrey L.WhittenLonnie D.BentleyKevin C.Dittman.System analysis and design methods [M].Mechanical Industry Press, 2004.9 [8] YunhuaGu.SQL Server2000Practical Course [M]Electronic Industry Press,2003.1 [9] AqiZhengYunhuaGu.Delphi Practical Course [M]. Electronic Industry Press,2004.12 [10] Ke Wang.Database Development Delphi classic case analysis [M].Tsinghua University Press,2005.2 [11]Zhongzhong Wang,A design method which is facing interface program [J].Computer System Applications,2008,(3):109-111
Biography Yutao Sun, 1980, male, Masters degree, lecturer. Main research direction: Natural Language Process, Text Excavation etc.
Anda mungkin juga menyukai
- Template - Access Control Policy Eg1Dokumen2 halamanTemplate - Access Control Policy Eg1bedorlehackerBelum ada peringkat
- Student Information System ReportDokumen27 halamanStudent Information System ReportAnshu Vyas100% (12)
- Chapter 2: RequirementsDokumen9 halamanChapter 2: RequirementsAnisha DhawanBelum ada peringkat
- jPOS EE SDKDokumen41 halamanjPOS EE SDKkampretlueBelum ada peringkat
- Online Railway Ticketing SystemDokumen243 halamanOnline Railway Ticketing Systemsakthipet1100% (1)
- Cyber Cafe ManagementDokumen42 halamanCyber Cafe ManagementNiro Thakur100% (1)
- Wedding PlannerDokumen34 halamanWedding Plannerकुमार सौरभBelum ada peringkat
- Student Info SystemDokumen18 halamanStudent Info SystemAbby DukeworthBelum ada peringkat
- Online Job Portal Java Project DocumentDokumen92 halamanOnline Job Portal Java Project DocumentMamatha RYBelum ada peringkat
- Digital Control Engineering: Analysis and DesignDari EverandDigital Control Engineering: Analysis and DesignPenilaian: 3 dari 5 bintang3/5 (1)
- Manage coffee shop bills and customersDokumen44 halamanManage coffee shop bills and customersMuhammad AtiqueBelum ada peringkat
- Railway Management SystemDokumen30 halamanRailway Management Systemrkjrocks0% (2)
- Online Bank Management SystemDokumen9 halamanOnline Bank Management SystemJayshree AhirraoBelum ada peringkat
- Hotel Reservation System Project ProposalDokumen6 halamanHotel Reservation System Project ProposalMd Moazzem Hossain75% (4)
- E Learning SrsDokumen11 halamanE Learning SrsPriyank Joshi69% (13)
- DRAFT CIS Amazon Web Services Foundations Benchmark v1.1.0Dokumen145 halamanDRAFT CIS Amazon Web Services Foundations Benchmark v1.1.0Ackld2008Belum ada peringkat
- Hotel ManagementDokumen90 halamanHotel Managementranaindia2011100% (2)
- Online Hotel Management System-1Dokumen198 halamanOnline Hotel Management System-1Shilu kumariBelum ada peringkat
- JavaDokumen26 halamanJavaSuzan DahitBelum ada peringkat
- FinalDokumen25 halamanFinalashBelum ada peringkat
- CabDokumen65 halamanCabRamanna Aakasa67% (3)
- 1.1 Statement of The Project: Information Science & Engineering, SjcitDokumen26 halaman1.1 Statement of The Project: Information Science & Engineering, SjcitashBelum ada peringkat
- Toll Tax ManagementDokumen53 halamanToll Tax ManagementpavithraBelum ada peringkat
- Objective of Python Projects On Airline Reservation SystemDokumen43 halamanObjective of Python Projects On Airline Reservation SystemGokul KrishnanBelum ada peringkat
- Project NewDokumen18 halamanProject Newhemant1108aranghBelum ada peringkat
- Project Synopsis: Easy BussingDokumen5 halamanProject Synopsis: Easy BussingNiro ThakurBelum ada peringkat
- 1.1 Current System: 1.3 Problem DefinitionDokumen21 halaman1.1 Current System: 1.3 Problem DefinitionAakash JaiswalBelum ada peringkat
- SVCP Alumni Communicator Development PackageDokumen11 halamanSVCP Alumni Communicator Development PackagePanduRang BiradarBelum ada peringkat
- Workshop Management SystemDokumen19 halamanWorkshop Management Systemfeed my mindBelum ada peringkat
- Modern Agriculture DotnetDokumen52 halamanModern Agriculture DotnetramalanfaizalBelum ada peringkat
- Chapter 3: Second Deliverable For Object Oriented Approach: Systems SpecificationsDokumen2 halamanChapter 3: Second Deliverable For Object Oriented Approach: Systems SpecificationsSweetsoulUroojMalik100% (1)
- 1.1 Purpose The Main Purpose of The Project Is To Reduce The Complexity of Students in ViewingDokumen51 halaman1.1 Purpose The Main Purpose of The Project Is To Reduce The Complexity of Students in ViewingNelarapuMaheshBelum ada peringkat
- Software Requirement Specification: PurposeDokumen7 halamanSoftware Requirement Specification: PurposegauravchauBelum ada peringkat
- Electricity Billing SystemDokumen21 halamanElectricity Billing SystemlaneyelkinsBelum ada peringkat
- Online TC Generation DocumentationDokumen15 halamanOnline TC Generation Documentationravi kumar100% (1)
- Report: 4 System Requirements Specification (SRS) Project Title: CU Transport Management SystemDokumen12 halamanReport: 4 System Requirements Specification (SRS) Project Title: CU Transport Management SystemAparajita BDBelum ada peringkat
- Travel and Tourism Mankagement SystemDokumen16 halamanTravel and Tourism Mankagement Systemmaddie2706Belum ada peringkat
- HmsDokumen13 halamanHmsveerBelum ada peringkat
- Project System AnalysisDokumen10 halamanProject System Analysisanushka2121surwaseBelum ada peringkat
- Web Based Computer Maintenance Management SystemDokumen8 halamanWeb Based Computer Maintenance Management SystemJemal MustefaBelum ada peringkat
- SRS For Student Information Management SystemDokumen6 halamanSRS For Student Information Management System22bca083.adityaprasadjenaBelum ada peringkat
- DocumentDokumen116 halamanDocumentNEERAJ2919250% (6)
- 9th AnswerDokumen8 halaman9th AnswerstaronlineBelum ada peringkat
- 1.1 Objective: Knowledge Based Community Sharing SystemDokumen90 halaman1.1 Objective: Knowledge Based Community Sharing SystemSuresh DhamathotiBelum ada peringkat
- System AnalysisDokumen7 halamanSystem AnalysisPradeep BhadauriaBelum ada peringkat
- Raw Online Exam SystemDokumen26 halamanRaw Online Exam SystempranavpfBelum ada peringkat
- Synopsis On Coll MGMTDokumen27 halamanSynopsis On Coll MGMTJeffrey ShawBelum ada peringkat
- Baby Doc1Dokumen29 halamanBaby Doc1Santhu StràñgèrBelum ada peringkat
- ProjectDokumen13 halamanProjectPushkar SinghBelum ada peringkat
- Study of Billing SystemsDokumen14 halamanStudy of Billing SystemsPrarthana P WBelum ada peringkat
- Car Parking SystemDokumen86 halamanCar Parking SystemShivraj CyberBelum ada peringkat
- 1.1 An Overview: Chapter-IDokumen58 halaman1.1 An Overview: Chapter-IprabhuBelum ada peringkat
- Vishu Project DocumentationDokumen63 halamanVishu Project Documentationkomkar634Belum ada peringkat
- CPP Project ReportDokumen20 halamanCPP Project ReportMohit D MoreBelum ada peringkat
- JAVA Mini ProjectDokumen26 halamanJAVA Mini ProjectCBelum ada peringkat
- Thesis PresentationDokumen21 halamanThesis PresentationMaxamed SheekhBelum ada peringkat
- Mobile Recharge SystemDokumen5 halamanMobile Recharge SystemRoma Mehta0% (1)
- Ascms BB Final22Dokumen107 halamanAscms BB Final22Tanmaya SahooBelum ada peringkat
- 2.1 Identification of Need: System AnalysisDokumen29 halaman2.1 Identification of Need: System AnalysisPawan KumarBelum ada peringkat
- Employee Survey Feedback SystemDokumen32 halamanEmployee Survey Feedback SystemAbhijeet NigoskarBelum ada peringkat
- System AnalysisDokumen7 halamanSystem AnalysisPradeep BhadauriaBelum ada peringkat
- UntitledDokumen3 halamanUntitledMohamed RamadanBelum ada peringkat
- INTERNET BANKING (Mod)Dokumen23 halamanINTERNET BANKING (Mod)siddhu143Belum ada peringkat
- Computer Science Self Management: Fundamentals and ApplicationsDari EverandComputer Science Self Management: Fundamentals and ApplicationsBelum ada peringkat
- A New Monitoring System For Data Mining ResearchDokumen6 halamanA New Monitoring System For Data Mining ResearchjcseukBelum ada peringkat
- Personalized Literature Retrieval Recommendation System Framework Design.Dokumen4 halamanPersonalized Literature Retrieval Recommendation System Framework Design.jcseukBelum ada peringkat
- Study On The K-Anonymous Algorithm For Data Publishing Scenario.Dokumen4 halamanStudy On The K-Anonymous Algorithm For Data Publishing Scenario.jcseukBelum ada peringkat
- Algorithm ResearchDokumen5 halamanAlgorithm ResearchjcseukBelum ada peringkat
- A Survey On Privacy Preserving For Micro Data Releasing in Cloud Computing Scenario.Dokumen8 halamanA Survey On Privacy Preserving For Micro Data Releasing in Cloud Computing Scenario.jcseukBelum ada peringkat
- Budget Approval System (Synopsis)Dokumen13 halamanBudget Approval System (Synopsis)sanjaykumarguptaaBelum ada peringkat
- CLINIVIEW 11.9 Database Migration Instruction r4Dokumen13 halamanCLINIVIEW 11.9 Database Migration Instruction r4Hervé TschanzBelum ada peringkat
- Simulation Activity 1 DSBFC and DSBSCDokumen6 halamanSimulation Activity 1 DSBFC and DSBSCDennis ABelum ada peringkat
- Linux User AccountDokumen5 halamanLinux User Accountrabirm77Belum ada peringkat
- Training on Movable Collateral RegistryDokumen18 halamanTraining on Movable Collateral Registrykeno ayana50% (2)
- Software Requirements Specification For Library Management SystemDokumen12 halamanSoftware Requirements Specification For Library Management SystemsushiljaiswBelum ada peringkat
- Bhavik and ParthDokumen12 halamanBhavik and Parthvaje rohanBelum ada peringkat
- HP CVEVA InstallGuideDokumen78 halamanHP CVEVA InstallGuideWid SuBelum ada peringkat
- Installing and Configuring WhatsUp GoldDokumen31 halamanInstalling and Configuring WhatsUp GoldDenny Oktaviandono100% (1)
- ProgrammingDokumen622 halamanProgrammingwespinoaBelum ada peringkat
- Use Alter Statement To Modify The Authentication or Database Resource of A UserDokumen7 halamanUse Alter Statement To Modify The Authentication or Database Resource of A UserSai Anirudh DuggineniBelum ada peringkat
- Software Requirement Specification E-SEVADokumen17 halamanSoftware Requirement Specification E-SEVAMayank TiwariBelum ada peringkat
- Slotlogic PDFDokumen361 halamanSlotlogic PDFstrembarobertBelum ada peringkat
- OSS-RC 10.0 Core System AdministrationDokumen4 halamanOSS-RC 10.0 Core System Administrationedson27Belum ada peringkat
- Videoflix: Website Customer Usage ManualDokumen8 halamanVideoflix: Website Customer Usage ManualDtv OnlineBelum ada peringkat
- Error BIP ADSI SiebelDokumen2 halamanError BIP ADSI SiebelIvan Gutierrez AngelesBelum ada peringkat
- Sap Security TutorialDokumen19 halamanSap Security TutorialAnusha ReddyBelum ada peringkat
- Dokumen - Tips Apex Ebs Security and Responsibility Introduction Why Use Apex With EbsDokumen24 halamanDokumen - Tips Apex Ebs Security and Responsibility Introduction Why Use Apex With EbsJalal PaymaniBelum ada peringkat
- A Novel Approach For Measuring Security in Software Systems - CIAAANDokumen11 halamanA Novel Approach For Measuring Security in Software Systems - CIAAANJournal of ComputingBelum ada peringkat
- Administrator Guide Apeos IV C2270/3370Dokumen673 halamanAdministrator Guide Apeos IV C2270/3370Hendro NugrohoBelum ada peringkat
- Gen5 Getting Started Guide - 5321045 Rev GDokumen78 halamanGen5 Getting Started Guide - 5321045 Rev GpoyenBelum ada peringkat
- China Telecom's Wireless Broadband Client - User ManualDokumen11 halamanChina Telecom's Wireless Broadband Client - User ManualnthanhphanBelum ada peringkat
- Elemec3 Portal User ManualDokumen37 halamanElemec3 Portal User ManualRifki FathurrahmanBelum ada peringkat
- BSL Annual Report 2022 23finalDokumen124 halamanBSL Annual Report 2022 23finalrohitkug.p.s1999Belum ada peringkat