Mobile Communication Thesis
Diunggah oleh
Waseem AhmedDeskripsi Asli:
Hak Cipta
Format Tersedia
Bagikan dokumen Ini
Apakah menurut Anda dokumen ini bermanfaat?
Apakah konten ini tidak pantas?
Laporkan Dokumen IniHak Cipta:
Format Tersedia
Mobile Communication Thesis
Diunggah oleh
Waseem AhmedHak Cipta:
Format Tersedia
2012
PAF KIET Subimitted By:Madiha Zaib
[ SIM/USIM CLONNING IDENTIFICATION & PRIVILEGE]
This paper investigates the mobile cloning by cloned the Subscriber identity Module (SIM)/Universal Subscriber Identity Module (USIM) in GSM/Universal Mobile Telecommunication System (UMTS) technologies
ABSTRACT This paper investigates the mobile cloning by cloned the Subscriber identity Module (SIM)/Universal Subscriber Identity Module (USIM) in GSM/Universal Mobile Telecommunication System (UMTS) technologies. It could be happen by the cloning of SIM and access network through SIM authentication, in this paper, we will identify this type of cloning by the mobility management & call setup procedures.
INTRODUCTION Mobile telecommunications services have become very popular recently. Consider Taiwan as an example, the total number of mobile service subscribers has reached over 22 millions, with the penetration rate over 100 percent. As the penetration rate of mobile services significantly increase, fake usage has become a serious issue. At the mobile subscriber side, modern mobile services, such as GSM and Universal Mobile Telecommunication System (UMTS), are secured by the subscriber identity module (SIM). Without the SIM card, a mobile phone or mobile station (MS) cannot access mobile services (except for emergency calls). The SIM can be a smart card that usually has the size of a credit card, a smaller sized plug-in SIM, or a smart card that can be performed, which contains a plug-in SIM that can be broken out of it. A SIM contains the subscriber-related information including its identity, authentication key, and encryption key. The subscriber identity and authentication key are used to authorize mobile service access, and to avoid fraudulent access of a cloned MS. Through interaction between the SIM and the authentication center (AuC), GSM provides one-way authentication. In UMTS, mutual authentication is achieved by sharing a secret key between the SIM and the AuC. This procedure follows a challenge/response protocol identical to the GSM subscriber authentication and key establishment protocol combined with a sequence-number based onepass protocol for network authentication derived from ISO/ IEC 9798-4. The above authentication procedures assume that the SIM is securely kept by the corresponding legal mobile user. Unfortunately, we have observed the existence of cloned SIMs that also have the same identities and authentication keys as the legal SIMs. These cloned SIMs will result in fraudulent usage as well as misrouting of incoming calls to the legal users. In Taiwan, potential loss due to this problem can be up to several millions of US dollars per year. To our knowledge, this issue has not been addressed in the literature. In this paper, we investigate how fraudulent usage may occur when fraudulent usage may be detected by the existing UMTS/GSM mechanisms and how to reduce the possibility of fraudulent usage.
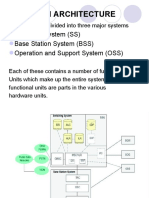
PROBLEM STATEMENT We use GSM/UMTS as an example to describe the operations in a mobile telecommunications network and show how fraudulent usage may occur. In GSM/UMTS, authentication is typically performed in the following events: registration (i.e., MS attach or location update), call origination (i.e., an outgoing call), and call termination (i.e., an incoming call). An illegal user gains access to the mobile network through registration and then enjoys free services through call originations. Such fraudulent usage may be detected by the GSM/UMTS network when the legal user performs the next registration or call origination. We briefly describe the registration and call setup procedures as follows Mobility management of mobile services involves two types of mobility databases: Home Location Register (HLR) and Visitor Location Register (VLR). When a user subscribes to the services of a mobile operator, a record is created in the operators HLR. The record stores services subscribed by the user (such as call waiting, call forwarding, voice mailbox, etc.). The location information (i.e., the address of the VLR visited by the MS) is also kept in the record. The service areas of mobile networks are partitioned into several location areas (LAs). One or more LAs are associated with a VLR. When a mobile user visits a LA, a temporary record for the mobile user is created in the corresponding VLR. The VLR typically collocates with a mobile switching center (MSC) that is responsible for call setup of MS. The VLR stores subscription information (replicated from the HLR) for the visiting subscribers so that they visited system can provide services. The VLR record also maintains the location information (i.e., the address of the LA where the MS resides). In other words, the VLR is the location register other than the HLR used to retrieve information for handling calls to or from a visiting mobile user. To track the location of an MS, the MS automatically reports its location (to the visited VLR and then to the HLR) when it moves to a new location. This procedure is called registration. Before the user accesses the VLR/HLR, authentication is performed between the user and the AuC (which may be collocated with HLR). To deliver a call to an MS, the network retrieves the location information stored in the HLR and the VLR, and the network sets up a trunk based on this location information. Like registration, authentication is required before call setup is performed. In this paper, we present the fraudulent usage problem due to cloned SIM. Suppose that the SIM card of a legal user u has been cloned by an illegal user u_. Consider the timing diagram in Fig. 1. In this example, u enters a location area LA1 at time _0, and moves to another location area LA2 at time _3. Then, following the standard GSM/UMTS mobility management procedure [17], u informs the network that it has moved into LA1 at _0, and informs that it has left LA1 and moved into LA2 at _3. Fig. 2 illustrates the registration procedure performed at _0. In this figure, the MS is first authenticated by the AuC. (Note that through network signaling optimization [1], [16], the MS may be authenticated by the VLR instead of the AuC.) Then, the MS registers to VLR1 and the HLR. After registration, the HLR record of u indicates that the MS is in VLR1, and the record in VLR1 indicates that the MS is in LA1. Suppose that u_ attempts to illegally access the mobile network at time _1 in the interval _0; _3_. This illegal user u_ either issues attach or a normal location area update action at _1. If u_ and u are in the same location area LA1, then this abnormal action will be detected; that is, the network notices that the same MS registers to the same location area twice. The network may suspend the services for u until the fraudulent usage issue is cleared. If u_ registers in a different location area LA3 (controlled by VLR2 in our example), then the network considers that u has moved from LA1 to LA3. As illustrated in Fig. 3, after the registration at _1, the HLR record indicates that u is in VLR2 and the VLR2 record indicates that u is in LA3. The VLR1 record for u is deleted through the location cancellation procedure. At this point, u_ gains mobile service access and fraudulent usage may occur. Such fraudulent usage can continue until either there is an outgoing call originated by u at time _2 or when u moves to
another location area LA3 and issues location update at time_3. Therefore, two cases are considered: Case 1. Suppose that after _1, the first outgoing call for u occurs before u moves to LA2 (i.e., _2 < _3). Then, at _2, u issues a call origination request to VLR1 as illustrated in Fig. 4. Since the us record at VLR1 has been erased or modified (in Fig. 4, the record has been erased), the network will detect that u has registered with location area LA3 but is issuing an outgoing call from location area LA1. At this point, the mobile service of u will be suspended until the network has resolved the fraudulent usage issue. Case 2. If _3 < _2, then after _1, the first event of u is a registration request due to movement from LA1 to LA2 (assume that both location areas are covered by VLR1). Similar to the situation in Case 1, when u issues the registration request to VLR1, VLR1 cannot identify the record for u, and the potential fraudulent usage situation is detected. In Fig. 1, let t1 _3 _ _1 and t2 _2 _ _1. Then, T mint1; t2 is the potential fraudulent usage period. During this period, u_ can illegally originate calls. Also, all incoming calls to u will be directed to u_ during T, i.e., these calls are misrouted as illustrated in Fig. 5. The calling parties of these misrouted calls may misleadingly think that the mobile operator accidentally routes the calls to wrong places. In the next section, we derive the expected potential fraudulent usage period ET_ and the probability PrN n_ that there are n misrouted calls during the potential fraudulent usage period.
Anda mungkin juga menyukai
- Network Switching Subsystem Functions and ComponentsDokumen5 halamanNetwork Switching Subsystem Functions and ComponentsMehboob AliBelum ada peringkat
- Third Generation CDMA Systems for Enhanced Data ServicesDari EverandThird Generation CDMA Systems for Enhanced Data ServicesPenilaian: 5 dari 5 bintang5/5 (1)
- Beginners Guide To Understanding Roaming Fraud in The Developing MarketDokumen9 halamanBeginners Guide To Understanding Roaming Fraud in The Developing Marketfraudmanagement86% (7)
- Summary of Andreas M. Antonopoulos, Olaoluwa Osuntokun & René Pickhardt's Mastering the Lightning NetworkDari EverandSummary of Andreas M. Antonopoulos, Olaoluwa Osuntokun & René Pickhardt's Mastering the Lightning NetworkBelum ada peringkat
- WINET Haas Lin 1998 09Dokumen8 halamanWINET Haas Lin 1998 09Chakravarthi ChittajalluBelum ada peringkat
- GSM Mobility ManagementDokumen6 halamanGSM Mobility ManagementRodjean SimballaBelum ada peringkat
- The Home Location RegisterDokumen2 halamanThe Home Location RegisterSamSameleviBelum ada peringkat
- Imsi CatcherDokumen28 halamanImsi Catchergame__overBelum ada peringkat
- Authentication Protocols in Wireless Communications ExaminedDokumen10 halamanAuthentication Protocols in Wireless Communications ExaminedShilpa MaratheBelum ada peringkat
- Taller Roaming PP Fraude EngDokumen0 halamanTaller Roaming PP Fraude Enghalcon2001Belum ada peringkat
- GSM Cell Site Forensics: T.. Olivier. MDokumen14 halamanGSM Cell Site Forensics: T.. Olivier. MHazem ElabedBelum ada peringkat
- Mobility and Roaming - T3.10Dokumen42 halamanMobility and Roaming - T3.10acajahuaringaBelum ada peringkat
- Experiences in Mobile Phone FraudDokumen11 halamanExperiences in Mobile Phone FraudSubhash DeshpandeBelum ada peringkat
- Sample PDP and HLRDokumen1 halamanSample PDP and HLRgegeBelum ada peringkat
- GSM Architecture: Switching System (SS) Base Station System (BSS) Operation and Support System (OSS)Dokumen19 halamanGSM Architecture: Switching System (SS) Base Station System (BSS) Operation and Support System (OSS)aimslifeBelum ada peringkat
- Classification Detection Prosecution of FraudDokumen6 halamanClassification Detection Prosecution of FraudmemorymaskBelum ada peringkat
- Call Set-Up in A GSM Network: Msisdn CC + NDC + SNDokumen7 halamanCall Set-Up in A GSM Network: Msisdn CC + NDC + SNgoutam4321Belum ada peringkat
- Learn SoRDokumen8 halamanLearn SoRRasheedKhouliBelum ada peringkat
- How To Determine The Location of A Mobile Subscriber: Sergey PuzankovDokumen3 halamanHow To Determine The Location of A Mobile Subscriber: Sergey PuzankovMisterAto MaisonBelum ada peringkat
- Forensics and The GSM Mobile Telephone System: International Journal of Digital Evidence Spring 2003, Volume 2, Issue 1Dokumen17 halamanForensics and The GSM Mobile Telephone System: International Journal of Digital Evidence Spring 2003, Volume 2, Issue 1BEALogicBelum ada peringkat
- Mobile: C2 - Safaricom InternalDokumen1 halamanMobile: C2 - Safaricom InternalJane MuliBelum ada peringkat
- Human - Computer Interaction ComputerDokumen18 halamanHuman - Computer Interaction ComputerVipul VeramBelum ada peringkat
- GSM 1Dokumen28 halamanGSM 1joydeep12Belum ada peringkat
- GSM Cellular Network: 1 Principles of GSM Mobile Communication TechnologyDokumen17 halamanGSM Cellular Network: 1 Principles of GSM Mobile Communication TechnologyTuan-Anh BuiBelum ada peringkat
- Traffic CasesDokumen30 halamanTraffic CasesNitin JainBelum ada peringkat
- Definition of Mobile Phone CloningDokumen22 halamanDefinition of Mobile Phone CloningPrabhat Sharma0% (1)
- Mobile Phone Fraud Seminar Report 12Dokumen10 halamanMobile Phone Fraud Seminar Report 12Jojin JoseBelum ada peringkat
- Procedures: UMTS System OverviewDokumen45 halamanProcedures: UMTS System OverviewRock DolphinBelum ada peringkat
- Manage subscriber data with HLR databaseDokumen2 halamanManage subscriber data with HLR databaseSamSameleviBelum ada peringkat
- Mobile Computing Assignment 5Dokumen17 halamanMobile Computing Assignment 5Hey BroBelum ada peringkat
- Introduction To GSM, The Global System For Mobile Communication 1. Introduction: The Evolution of Mobile Telephone SystemsDokumen9 halamanIntroduction To GSM, The Global System For Mobile Communication 1. Introduction: The Evolution of Mobile Telephone SystemsMaulin AminBelum ada peringkat
- CC CC CC: C CC CC CC CDokumen19 halamanCC CC CC: C CC CC CC Cpk_babuaBelum ada peringkat
- Location Leaks On The GSM Air InterfaceDokumen13 halamanLocation Leaks On The GSM Air InterfacessthakurBelum ada peringkat
- Operation and Maintenance CenterDokumen3 halamanOperation and Maintenance CenterRabia RindBelum ada peringkat
- Circuit FingerDokumen16 halamanCircuit FingerPatrick Howell O'NeillBelum ada peringkat
- GSM & GPRSDokumen19 halamanGSM & GPRSphantd_hcmBelum ada peringkat
- GSM Fundamentals: Prepared by Asem Mohammed ShamsDokumen38 halamanGSM Fundamentals: Prepared by Asem Mohammed ShamsMahmoud EL-BannaBelum ada peringkat
- Analysis and Detection of SIMbox Fraud in Mobility NetworksDokumen8 halamanAnalysis and Detection of SIMbox Fraud in Mobility NetworksRahul KumarBelum ada peringkat
- Network ArchitectureDokumen10 halamanNetwork ArchitectureTri NguyenBelum ada peringkat
- Mobile Cloning Seminar ReportDokumen35 halamanMobile Cloning Seminar ReportAbhiram TalluriBelum ada peringkat
- GSM LectureDokumen26 halamanGSM Lecturesamy gomaaBelum ada peringkat
- VLR Overflow 1 PDFDokumen9 halamanVLR Overflow 1 PDFpothiqueBelum ada peringkat
- An Approach Towards Locating A Subscriber in The Network: Shelly Gahlawat, Shreya ShivaniDokumen3 halamanAn Approach Towards Locating A Subscriber in The Network: Shelly Gahlawat, Shreya ShivaniinventionjournalsBelum ada peringkat
- Mobile Computing Q&ADokumen6 halamanMobile Computing Q&AAnonymous IJAAT2dqBBelum ada peringkat
- Call Flow GSM - CopieDokumen8 halamanCall Flow GSM - CopieStéphanie Océane NadjiBelum ada peringkat
- Analysis and Detection of Fraud in International Calls Using Decision TreeDokumen10 halamanAnalysis and Detection of Fraud in International Calls Using Decision TreeDilip ThummarBelum ada peringkat
- Various Handover Management Techniques in GSM Cellular SystemDokumen4 halamanVarious Handover Management Techniques in GSM Cellular SystembinjibrilBelum ada peringkat
- GSM Call FlowDokumen125 halamanGSM Call FlowHộp Thư Điện TửBelum ada peringkat
- 2.2.3 The Mobile Services Switching CentreDokumen4 halaman2.2.3 The Mobile Services Switching CentreTushar SaxenaBelum ada peringkat
- IMSI Catcher: Daehyun Strobel 13.juli 2007Dokumen22 halamanIMSI Catcher: Daehyun Strobel 13.juli 2007nam kiwBelum ada peringkat
- Communications 3Dokumen4 halamanCommunications 3jydee033Belum ada peringkat
- GSM Call FlowDokumen125 halamanGSM Call Flowkazitamjidali@gmail.comBelum ada peringkat
- CCCCC C CCCCC: Training Reports / ProjectsDokumen15 halamanCCCCC C CCCCC: Training Reports / Projectstiyas7Belum ada peringkat
- Analysis and Detection of Simbox Fraud in Mobility Networks: Proceedings - Ieee Infocom April 2014Dokumen9 halamanAnalysis and Detection of Simbox Fraud in Mobility Networks: Proceedings - Ieee Infocom April 2014Yassine LASRIBelum ada peringkat
- Mobile Communication ProblemsDokumen4 halamanMobile Communication ProblemsIshan DixitBelum ada peringkat
- The GSM System History: NextDokumen19 halamanThe GSM System History: NextJoseph DavisBelum ada peringkat
- Channels and Identities in GSM: Tanvir Singh, Amit Kumar, Dr. Yunfei LiuDokumen5 halamanChannels and Identities in GSM: Tanvir Singh, Amit Kumar, Dr. Yunfei Liukiranv_1Belum ada peringkat
- Modelman PDFDokumen72 halamanModelman PDFCarlos CamachoBelum ada peringkat
- Narrow Band Powerline Communication Module With Simple MAC User Narrow Band Powerline Communication Module With Simple MAC User Manual Narrow Band Powerline CommunicationDokumen8 halamanNarrow Band Powerline Communication Module With Simple MAC User Narrow Band Powerline Communication Module With Simple MAC User Manual Narrow Band Powerline CommunicationAle NqnBelum ada peringkat
- Authorization LetterDokumen4 halamanAuthorization LetterCherry Mae CarredoBelum ada peringkat
- I-Unit C#Dokumen20 halamanI-Unit C#Swapnil RathodBelum ada peringkat
- Cs Lesson PlanDokumen3 halamanCs Lesson Planapi-426721162Belum ada peringkat
- Schlinder Updated ContractDokumen10 halamanSchlinder Updated Contractapi-542351117Belum ada peringkat
- Ergonomic Analysis of Motor VehiclesDokumen14 halamanErgonomic Analysis of Motor VehiclesdeyeBelum ada peringkat
- FAQ's On BSNL Wings ServiceDokumen3 halamanFAQ's On BSNL Wings ServicePraveen Kumar ArjalaBelum ada peringkat
- Test NGDokumen35 halamanTest NGChinmay DeshpandeBelum ada peringkat
- ECE OLED TechnologyDokumen22 halamanECE OLED Technologygourav VermaBelum ada peringkat
- Business Model Canvas PlanningDokumen3 halamanBusiness Model Canvas PlanningjosliBelum ada peringkat
- GSM ParametersDokumen131 halamanGSM ParametersAjay ShuklaBelum ada peringkat
- Ecommerce WebsiteDokumen49 halamanEcommerce WebsiteMonsta X100% (1)
- Intelligent Systems in Big Data, Semantic Web and Machine LearningDokumen6 halamanIntelligent Systems in Big Data, Semantic Web and Machine LearningRachid BelfaqihBelum ada peringkat
- WDV Dep MethodDokumen24 halamanWDV Dep Methodsudershan9Belum ada peringkat
- Capstone SampleDokumen60 halamanCapstone SampleGaileyBelum ada peringkat
- Finite-Volume Compact Schemes On Staggered GridsDokumen42 halamanFinite-Volume Compact Schemes On Staggered GridsKian ChuanBelum ada peringkat
- AWS Simple-Icons v2.0Dokumen10 halamanAWS Simple-Icons v2.0jonbaerBelum ada peringkat
- Finite Element Methods: Lecture Module 1-1: IntroductionDokumen35 halamanFinite Element Methods: Lecture Module 1-1: IntroductionAhmad Faidhi100% (1)
- Manual Switch Admnistrable FL SWITCH SMCS 8TX PDFDokumen132 halamanManual Switch Admnistrable FL SWITCH SMCS 8TX PDFLuis AlbertoBelum ada peringkat
- Department of Computer ScienceDokumen2 halamanDepartment of Computer ScienceAnonymous XZZ6j8NOBelum ada peringkat
- Jura J9.3 Wiring DiagramDokumen4 halamanJura J9.3 Wiring DiagramGrom NeposedaBelum ada peringkat
- Top 5 sorting algorithms explained: Insertion, Selection, Bubble, Merge and Quick SortDokumen2 halamanTop 5 sorting algorithms explained: Insertion, Selection, Bubble, Merge and Quick SortCristine Joy JemillaBelum ada peringkat
- SAP Training SampleDokumen7 halamanSAP Training SampleMaria Patricia B. DequillaBelum ada peringkat
- RFP For Procurement of 2700 PBKsDokumen194 halamanRFP For Procurement of 2700 PBKsAbhik ChattopadhyayBelum ada peringkat
- 15 - 20 - Manual Pit & Pdit YakogawaDokumen61 halaman15 - 20 - Manual Pit & Pdit YakogawaWilmar Ortiz MoraBelum ada peringkat
- Dijkstra's, Kruskals and Floyd-Warshall AlgorithmsDokumen38 halamanDijkstra's, Kruskals and Floyd-Warshall AlgorithmsRajan JaiprakashBelum ada peringkat
- I. Electronic Commerce Act of 2000 (R.A. 8792)Dokumen3 halamanI. Electronic Commerce Act of 2000 (R.A. 8792)Lorelie SantosBelum ada peringkat
- SEEBURGER Business Integration Suite (BIS) Brochure - Solution Overview Brochure - EnglishDokumen8 halamanSEEBURGER Business Integration Suite (BIS) Brochure - Solution Overview Brochure - EnglishAshokBelum ada peringkat
- Identification of Significant Features and Data Mining Techniques in Predicting Heart Disease Telematics and InformaticsDokumen34 halamanIdentification of Significant Features and Data Mining Techniques in Predicting Heart Disease Telematics and InformaticsMahmood SyedBelum ada peringkat
- A Practical Guide Wireshark ForensicsDari EverandA Practical Guide Wireshark ForensicsPenilaian: 5 dari 5 bintang5/5 (4)
- CCNA: 3 in 1- Beginner's Guide+ Tips on Taking the Exam+ Simple and Effective Strategies to Learn About CCNA (Cisco Certified Network Associate) Routing And Switching CertificationDari EverandCCNA: 3 in 1- Beginner's Guide+ Tips on Taking the Exam+ Simple and Effective Strategies to Learn About CCNA (Cisco Certified Network Associate) Routing And Switching CertificationBelum ada peringkat
- Computer Networking: The Complete Beginner's Guide to Learning the Basics of Network Security, Computer Architecture, Wireless Technology and Communications Systems (Including Cisco, CCENT, and CCNA)Dari EverandComputer Networking: The Complete Beginner's Guide to Learning the Basics of Network Security, Computer Architecture, Wireless Technology and Communications Systems (Including Cisco, CCENT, and CCNA)Penilaian: 4 dari 5 bintang4/5 (4)
- Computer Systems and Networking Guide: A Complete Guide to the Basic Concepts in Computer Systems, Networking, IP Subnetting and Network SecurityDari EverandComputer Systems and Networking Guide: A Complete Guide to the Basic Concepts in Computer Systems, Networking, IP Subnetting and Network SecurityPenilaian: 4.5 dari 5 bintang4.5/5 (13)
- Evaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsDari EverandEvaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsBelum ada peringkat
- Hacking: A Beginners Guide To Your First Computer Hack; Learn To Crack A Wireless Network, Basic Security Penetration Made Easy and Step By Step Kali LinuxDari EverandHacking: A Beginners Guide To Your First Computer Hack; Learn To Crack A Wireless Network, Basic Security Penetration Made Easy and Step By Step Kali LinuxPenilaian: 4.5 dari 5 bintang4.5/5 (67)
- CEH Certified Ethical Hacker Practice Exams, Third EditionDari EverandCEH Certified Ethical Hacker Practice Exams, Third EditionBelum ada peringkat
- AWS Certified Cloud Practitioner Study Guide: CLF-C01 ExamDari EverandAWS Certified Cloud Practitioner Study Guide: CLF-C01 ExamPenilaian: 5 dari 5 bintang5/5 (1)
- AWS Certified Solutions Architect Study Guide: Associate SAA-C02 ExamDari EverandAWS Certified Solutions Architect Study Guide: Associate SAA-C02 ExamBelum ada peringkat
- The Compete Ccna 200-301 Study Guide: Network Engineering EditionDari EverandThe Compete Ccna 200-301 Study Guide: Network Engineering EditionPenilaian: 5 dari 5 bintang5/5 (4)
- The Ultimate Kali Linux Book - Second Edition: Perform advanced penetration testing using Nmap, Metasploit, Aircrack-ng, and EmpireDari EverandThe Ultimate Kali Linux Book - Second Edition: Perform advanced penetration testing using Nmap, Metasploit, Aircrack-ng, and EmpireBelum ada peringkat
- CCST Cisco Certified Support Technician Study Guide: Networking ExamDari EverandCCST Cisco Certified Support Technician Study Guide: Networking ExamBelum ada peringkat
- Cybersecurity: A Simple Beginner’s Guide to Cybersecurity, Computer Networks and Protecting Oneself from Hacking in the Form of Phishing, Malware, Ransomware, and Social EngineeringDari EverandCybersecurity: A Simple Beginner’s Guide to Cybersecurity, Computer Networks and Protecting Oneself from Hacking in the Form of Phishing, Malware, Ransomware, and Social EngineeringPenilaian: 5 dari 5 bintang5/5 (40)
- Networking Fundamentals: Develop the networking skills required to pass the Microsoft MTA Networking Fundamentals Exam 98-366Dari EverandNetworking Fundamentals: Develop the networking skills required to pass the Microsoft MTA Networking Fundamentals Exam 98-366Belum ada peringkat
- ITIL® 4 Direct, Plan and Improve (DPI): Your companion to the ITIL 4 Managing Professional and Strategic Leader DPI certificationDari EverandITIL® 4 Direct, Plan and Improve (DPI): Your companion to the ITIL 4 Managing Professional and Strategic Leader DPI certificationBelum ada peringkat
- Computer Networking: The Complete Guide to Understanding Wireless Technology, Network Security, Computer Architecture and Communications Systems (Including Cisco, CCNA and CCENT)Dari EverandComputer Networking: The Complete Guide to Understanding Wireless Technology, Network Security, Computer Architecture and Communications Systems (Including Cisco, CCNA and CCENT)Belum ada peringkat
- Advanced Antenna Systems for 5G Network Deployments: Bridging the Gap Between Theory and PracticeDari EverandAdvanced Antenna Systems for 5G Network Deployments: Bridging the Gap Between Theory and PracticePenilaian: 5 dari 5 bintang5/5 (1)
- IP Routing Protocols All-in-one: OSPF EIGRP IS-IS BGP Hands-on LabsDari EverandIP Routing Protocols All-in-one: OSPF EIGRP IS-IS BGP Hands-on LabsBelum ada peringkat
- Introduction to Cyber-Warfare: A Multidisciplinary ApproachDari EverandIntroduction to Cyber-Warfare: A Multidisciplinary ApproachPenilaian: 4.5 dari 5 bintang4.5/5 (3)
- FTTx Networks: Technology Implementation and OperationDari EverandFTTx Networks: Technology Implementation and OperationPenilaian: 5 dari 5 bintang5/5 (1)
- Microsoft Azure Infrastructure Services for Architects: Designing Cloud SolutionsDari EverandMicrosoft Azure Infrastructure Services for Architects: Designing Cloud SolutionsBelum ada peringkat
- The E-Commerce Book: Building the E-EmpireDari EverandThe E-Commerce Book: Building the E-EmpirePenilaian: 5 dari 5 bintang5/5 (1)