Business Security Procedures To Protect Assets and Employees
Diunggah oleh
gashraft61Deskripsi Asli:
Judul Asli
Hak Cipta
Format Tersedia
Bagikan dokumen Ini
Apakah menurut Anda dokumen ini bermanfaat?
Apakah konten ini tidak pantas?
Laporkan Dokumen IniHak Cipta:
Format Tersedia
Business Security Procedures To Protect Assets and Employees
Diunggah oleh
gashraft61Hak Cipta:
Format Tersedia
Business Security
Procedures to Protect
Assets and Employees
Includes six (6) modules:
1. Introduction and Table of
Contents
2. Guide to preparing a well
written manual
3. A Sample Security Manual
covering common
requirements and practices
4. 41 Policies and 29
corresponding forms
5. Violence in the Workplace
Supplement
6. Complete Index
Choose your delivery option:
Hard Cover Book plus
CD containing all documents
in editable Microsoft Word
format and instant download
or
Instant download only (no
shipping)
Have questions? Email:
sales@bizmanualz.com
How to Order:
Online: www.bizmanualz.com
By Phone: 3134-863-5079
800-466-9953
By Fax: 314-863-6571
Learn How to Protect and Control Your Physical Assets
The primary goals of any company are to be of service and to generate income. The
Security Department is responsible for developing, implementing and monitoring the
companys security plan and loss prevention program, by utilizing clear and thorough
security procedures. The Security Policies and Procedures Manual uses a scientific
model to help you understand the true scope of security & operations. By
understanding the cause and effect relationships between a companys policies and
procedures and the likelihood of error and exposure to crimes, you can implement a
comprehensive company-wide security plan that will significantly reduce your
companys risk.
41 Prewritten Policies and Procedures
1. Procedural security
2. Annual risk assessment and
evaluation
3. Ethics and employee conduct
4. Fingerprinting and photographing
of employees
5. Policy and criminal violations
6. Employee use of drugs or alcohol
7. Possession and carrying of
firearms
8. First aid and medical emergencies
9. Suspicious persons and activities
10. Identification procedures
11. Internal investigations
12. Court testimony by employees
13. Proprietary information
14. Guard program
15. Information security and the edp
center
16. Fire prevention and detection
17. Hazardous material
18. Inventory, delivery and receiving
controls
19. Security devices
20. Opening & closing cash-handling
facilities
21. Transportation of currency
22. Combinations
23. Key and access device control
24. Work station security
25. Employee assignments during
emergency responses
26. Emergency operating procedures:
all personnel
27. Robbery procedures: staff
personnel
28. Robbery procedures:
management personnel
29. Extortion procedures: staff
personnel
30. Extortion procedures:
management personnel
31. Bomb threat procedures: staff
personnel
32. Bomb threat procedures:
management personnel
33. Disaster response procedures:
staff personnel
34. Disaster response procedures:
management
35. Violence in the workplace
36. Personal protection and safety for
employees
37. Executive protection program
38. Testing and training requirements
39. Security training program
40. Documenting investigations
41. Media relations
Business Security
Procedures to Protect
Assets and Employees
30 Forms and Records
42. Alarm activation form
43. Bomb call warning form
44. Chronological log of events form
45. Combination control form
46. Combination number change form
47. Currency transportation form
48. Employee assignments form
49. Employee profile information form
50. Extortion phone call form
51. Incident tracking log
52. Key control form
53. Opening and closing form
54. Report of investigation: initial
report
55. Report of investigation:
continuation
56. Report of investigation - evidence
tag form report of investigation:
handwriting exemplar 1
57. Report of investigation:
handwriting exemplar - 2
58. Report of investigation:
investigator's checklist
59. Report of investigation: property
receipt
60. Report of investigation: follow up
61. Report of investigation: contact
log
62. Report of investigation: statement
continuation
63. Report of investigation: contact
notes
64. Report of investigation: statement
- s
65. Report of investigation: statement
v-w-i
66. Suspicious or threatening phone
call form
67. Suspicious activity report
68. Suspect description form
69. Security log form
70. Security education systems
annual projection
71. Security education systems 6
month expense forecast
Strategies & Tactics for Work & Home
The problem
Victims and losses
Identifying offenders
What employees can do
What employers can do
What supervisors can do
What security and law
enforcement can do
All personnel workplace
procedures
Bomb call warning form
Incident log form
Chronological log of events
Extortion telephone call form
Coping with crimes of violence
training
o Employee personal profile form
o Suspicious incident report form
o Suspicious or threatening
telephone call form
Training program: coping with
crimes of violence
Leaders guide: coping with crimes
of violence
Security Planning Policies, Procedures and Forms www.bizmanualz.com
Sample Procedure Page 3 of 4
Document ID
SEC 102
Title
ANNUAL RISK ASSESSMENT AND
EVALUATION
Print Date
mm/dd/yyyy
Revision
0.0
Prepared By
Date Prepared
mm/dd/yyyy
Effective Date
mm/dd/yyyy
Reviewed By
Date Reviewed
mm/dd/yyyy
Approved By
Date Approved
mm/dd/yyyy
Applicable Standard: None
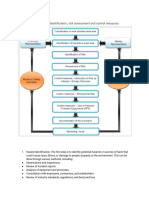
Policy: The Company will require an Annual Risk Assessment and written
evaluation.
Purpose: Define and describe the Security Programs annual evaluation and
updating process.
Scope: This assessment applies to all operating departments.
Definitions:
Responsibilities:
Unit Security Officer is responsible for conducting annual assessment and
submitting report.
Security Director is responsible for evaluating assessment and reports
findings and recommendations to Board of Directors.
Procedure:
1.0 RISK ASSESSMENT
1.1 All potential risks to the company shall be evaluated on at least an annual basis.
This annual assessment shall be conducted by each Unit Security Officer and the
written results and recommendations shall be forwarded to the Security Director.
1.2 Upon receipt of these written results and recommendations, the Security Director
shall also issue a report of findings to the board of directors. This report shall
include:
1. An overview of the status of each department regarding compliance with
policies and procedures.
2. A projection regarding any new equipment, personnel, policies or
procedures required for the next year, to meet the requirements of this
plan.
3. Any necessary change in current policies or procedures not addressed
elsewhere, and an accompanying rationale or explanation.
1.3 Any potential risk shall be identified, whether already addressed or newly
anticipated. If the identified risk has already been successfully addressed, no
Security Planning Policies, Procedures and Forms www.bizmanualz.com
Sample Procedure Page 4 of 4
further assessment or recommendations shall be required. Any newly-identified
risk shall be fully addressed.
1.4 Once potential risks have been identified and prioritized, the Security Director
shall:
1. Determine potential short and long range solutions.
2. Decide upon the most appropriate primary and secondary solutions.
3. Test and evaluate these solutions for effectiveness.
4. Include these solutions in the Disaster Management Plan, and related
testing and training programs.
2.0 RECORDS, POLICIES AND AGREEMENTS
2.1 All original records of the processes used to compile the information resulting in
these policies and procedures shall be retained by the Security Director. These
records shall include the names and positions of all appropriate persons involved
in the continued development of the Security Program.
2.2 All insurance policies, service and vendor agreements shall be reviewed at least
annually. If policies and agreements are satisfactory, existing agreements shall be
renewed. New vendors will be investigated to replace any unsatisfactory
agreements. The listing of these agreements, emergency services agencies, and
community resources shall be reviewed and updated at least annually.
2.3 The Security Director shall also be responsible for researching and developing a
listing of other product and service companies and individuals who may be
utilized on an interim basis. This listing shall be developed within each county, or
other appropriate geographic area serviced by the company, to provide primary or
backup services to supplement those offered by the Security Department. This
listing shall be reviewed and updated at least annually.
Revision History:
Revision Date Description of changes Requested By
0 mm/dd/yy Initial Release
Anda mungkin juga menyukai
- Mirdif Security & Safety Consultants Occupational Health and Safety ProgramDokumen8 halamanMirdif Security & Safety Consultants Occupational Health and Safety ProgramMohammed AtefBelum ada peringkat
- Construction Safety Policy GeneralDokumen57 halamanConstruction Safety Policy Generalayummy myra100% (3)
- Cyber Security Issues and ChallengesDokumen20 halamanCyber Security Issues and ChallengesRaghuram KrishnamurthyBelum ada peringkat
- ISO/ IEC 27001:2013 Lead Implementer Training Trainer: Trivesh Sharma, Oyuntugs BDokumen14 halamanISO/ IEC 27001:2013 Lead Implementer Training Trainer: Trivesh Sharma, Oyuntugs BTrivesh SharmaBelum ada peringkat
- Safety Risk Management ProcedureDokumen14 halamanSafety Risk Management ProcedureJolanda OnbekendBelum ada peringkat
- Safety Audit Report SampleDokumen24 halamanSafety Audit Report Samplekanakarao187% (15)
- Unisteel Technology HIRAC ProcedureDokumen9 halamanUnisteel Technology HIRAC Procedurenarenmaniam100% (2)
- Nebosh NotesDokumen32 halamanNebosh NotesVinod Sasidharan NairBelum ada peringkat
- Risk Assessment Policy and Procedures GuideDokumen15 halamanRisk Assessment Policy and Procedures Guidemike0011Belum ada peringkat
- Safety Officer Duty ResponsibilityDokumen6 halamanSafety Officer Duty ResponsibilityKannan NBelum ada peringkat
- Introduction To Cybersecurity: Nanodegree Program SyllabusDokumen15 halamanIntroduction To Cybersecurity: Nanodegree Program SyllabusaamirBelum ada peringkat
- Threat and Risk Assessment TemplateDokumen30 halamanThreat and Risk Assessment TemplateMarija PetkovicBelum ada peringkat
- Bizmanualz Security Procedures SampleDokumen6 halamanBizmanualz Security Procedures SampleHasanBelum ada peringkat
- ISO27k Awareness Presentation v2Dokumen41 halamanISO27k Awareness Presentation v2Amine RachedBelum ada peringkat
- Security Controls Evaluation, Testing, and Assessment HandbookDari EverandSecurity Controls Evaluation, Testing, and Assessment HandbookPenilaian: 5 dari 5 bintang5/5 (2)
- Element 4 Health & Safety Management Systems 3 - Planning PDFDokumen127 halamanElement 4 Health & Safety Management Systems 3 - Planning PDFrewmarineBelum ada peringkat
- Fundamentals of Safety Management1Dokumen17 halamanFundamentals of Safety Management1Arben MontellanoBelum ada peringkat
- Guidance of Risk AssessmentDokumen31 halamanGuidance of Risk AssessmentBagus Chandra KurniawanBelum ada peringkat
- NHK Spring Philippines Safety ManualDokumen62 halamanNHK Spring Philippines Safety ManualJea RodegerioBelum ada peringkat
- Hotel Security Checklist - SafetyCulture PDFDokumen19 halamanHotel Security Checklist - SafetyCulture PDFMohamed DawesBelum ada peringkat
- QuestionDokumen6 halamanQuestionAnosha AslamBelum ada peringkat
- Intertek GSV Final 2Dokumen44 halamanIntertek GSV Final 2Nguyễn Tá TriệuBelum ada peringkat
- Disaster Relief Operations Overseas: The Military ContributionDokumen122 halamanDisaster Relief Operations Overseas: The Military ContributionomerBelum ada peringkat
- Secure Controls Framework 2023 4Dokumen280 halamanSecure Controls Framework 2023 4ice1025Belum ada peringkat
- The Risk Management ProcessDokumen41 halamanThe Risk Management ProcessRichard Espanola Avena100% (1)
- Gulf Training Institute Safety Course Chapter on Developing an Effective Safety Management SystemDokumen7 halamanGulf Training Institute Safety Course Chapter on Developing an Effective Safety Management SystemRavikant Pandey100% (2)
- Certified Cybersecurity Compliance ProfessionalDari EverandCertified Cybersecurity Compliance ProfessionalPenilaian: 5 dari 5 bintang5/5 (5)
- Security Manual 2009Dokumen31 halamanSecurity Manual 2009Liviu LiviuBelum ada peringkat
- Leicester Medical Support: Health and Safety Policy Health - and - Safety - Policy - v1Dokumen7 halamanLeicester Medical Support: Health and Safety Policy Health - and - Safety - Policy - v1stephanieBelum ada peringkat
- RA Guidelines MOMDokumen38 halamanRA Guidelines MOMnautiyamaBelum ada peringkat
- Cyber ReportDokumen121 halamanCyber ReportÄl ÖÏvínBelum ada peringkat
- ISO17799 InfoSec Management GuideDokumen44 halamanISO17799 InfoSec Management Guidedeltafx1Belum ada peringkat
- Name: Chan Pui Pui Student ID: MEI 1343: 1. Risk Management Creates and Protects ValueDokumen5 halamanName: Chan Pui Pui Student ID: MEI 1343: 1. Risk Management Creates and Protects ValueAdwin Choo100% (1)
- The CRISC Job Practice Areas Reflect The Vital and Evolving Responsibilities of IT Risk and IS Control PractitionersDokumen3 halamanThe CRISC Job Practice Areas Reflect The Vital and Evolving Responsibilities of IT Risk and IS Control PractitionersAleAleBelum ada peringkat
- NEBOSH IGC 1 Questions and AnswersDokumen31 halamanNEBOSH IGC 1 Questions and Answersテレブリコ ジェファーソン100% (2)
- Workplace Security Playbook: The New Manager's Guide to Security RiskDari EverandWorkplace Security Playbook: The New Manager's Guide to Security RiskBelum ada peringkat
- Hotel Safety SystemsDokumen40 halamanHotel Safety SystemsPn FirdausBelum ada peringkat
- DownloadDokumen5 halamanDownloadali awanBelum ada peringkat
- Tajinder Singh: Sitxwhs003 Implement and Monitor Work Health and Safety PracticesDokumen20 halamanTajinder Singh: Sitxwhs003 Implement and Monitor Work Health and Safety PracticesHarkamal singhBelum ada peringkat
- DF 6Dokumen20 halamanDF 6THRISHA JINKALABelum ada peringkat
- An Introduction To Chemical Process SafetyDokumen10 halamanAn Introduction To Chemical Process Safetyhitesh bhoiBelum ada peringkat
- Risk Managementand Insurance PlanningDokumen6 halamanRisk Managementand Insurance PlanningtomshadesBelum ada peringkat
- Safety ElementsDokumen5 halamanSafety ElementsSethuBelum ada peringkat
- Hid Regulatory ModelDokumen7 halamanHid Regulatory ModelAyoun Ul HaqueBelum ada peringkat
- Code of Practice: Ref Cop Gra Issue 1, Dec 2003 Always Refer To Intranet For Latest Version 1Dokumen15 halamanCode of Practice: Ref Cop Gra Issue 1, Dec 2003 Always Refer To Intranet For Latest Version 1etaBelum ada peringkat
- The 7 Step Risk Management ProcessDokumen41 halamanThe 7 Step Risk Management ProcessThanveer MaBelum ada peringkat
- BSBRSK501 Learner Guide V4.0Dokumen69 halamanBSBRSK501 Learner Guide V4.0Hugo de Jesús Fernández MartínezBelum ada peringkat
- Safety MS SingaporeDokumen2 halamanSafety MS SingaporeRaymondGomezBlancoBelum ada peringkat
- Sms-What Is It?: Formal, Top-Down Business-Like Approach To Managing Safety Risk in The OperationDokumen36 halamanSms-What Is It?: Formal, Top-Down Business-Like Approach To Managing Safety Risk in The OperationAnonymous CmDManBelum ada peringkat
- 05 - Information Security PolicyDokumen3 halaman05 - Information Security PolicyCyber PunkBelum ada peringkat
- SMS of Aviation - A Guide To Your Aviation Safety Management System, The - Chuck WrightDokumen84 halamanSMS of Aviation - A Guide To Your Aviation Safety Management System, The - Chuck Wright2249354385Belum ada peringkat
- Reviewer DawDokumen13 halamanReviewer DawMark GBelum ada peringkat
- Lec2risk AssessmentADokumen21 halamanLec2risk AssessmentAAffan KhawajaBelum ada peringkat
- IR PlanningDokumen3 halamanIR PlanningShreenkhala BhattaraiBelum ada peringkat
- SITXWHS003-Implement and Monitor Work Health and Safety PracticesDokumen3 halamanSITXWHS003-Implement and Monitor Work Health and Safety Practicessandeep kesarBelum ada peringkat
- OSH Risk MGMT T1Dokumen19 halamanOSH Risk MGMT T1harteniBelum ada peringkat
- Techniques of Construction Safety ManagementDokumen9 halamanTechniques of Construction Safety Managementkhrizel lee tuazonBelum ada peringkat
- A Security RequirementDokumen7 halamanA Security Requirementwejdan alharbiBelum ada peringkat
- 3 Audit ScopeDokumen3 halaman3 Audit ScopemhuzaifaBelum ada peringkat
- SITXWHS002 - Identify Hazards, Assess and Control Safety Risks - Assessment 1Dokumen17 halamanSITXWHS002 - Identify Hazards, Assess and Control Safety Risks - Assessment 1saifabdulmoiz2Belum ada peringkat
- 559 Bamber StevensDokumen6 halaman559 Bamber StevensWaqas Ahmad KhanBelum ada peringkat
- Cosh TopicDokumen17 halamanCosh TopicJoseph Ryan ManandegBelum ada peringkat
- Developing, Implementing and Maintaining A Safety Management SystemDokumen12 halamanDeveloping, Implementing and Maintaining A Safety Management SystemyeomanshanBelum ada peringkat
- Safety FatDokumen22 halamanSafety FatAnvita tadepalliBelum ada peringkat
- Paramjit Kaur Student Id: S1339 Date:24-05-2021Dokumen6 halamanParamjit Kaur Student Id: S1339 Date:24-05-2021Harkamal singhBelum ada peringkat
- Robust Security Infrastructure - Short Duration Course_combined 1 (1)Dokumen75 halamanRobust Security Infrastructure - Short Duration Course_combined 1 (1)Rizky RahmanBelum ada peringkat
- Michigan Municipal Workers' Comp Safety ProgramDokumen3 halamanMichigan Municipal Workers' Comp Safety ProgramzulfactBelum ada peringkat
- Operational Guidance: Inspection Procedure (June 2018) : Enforcement Policy Statement Enforcement Management ModelDokumen8 halamanOperational Guidance: Inspection Procedure (June 2018) : Enforcement Policy Statement Enforcement Management ModelRinaldi ArazaquBelum ada peringkat
- CCTV Policy for Installation, Management, MaintenanceDokumen2 halamanCCTV Policy for Installation, Management, MaintenanceSurjeet Singh Saran100% (1)
- Cyber Security PPT Swati MaharjanDokumen21 halamanCyber Security PPT Swati MaharjanYunix SubodhBelum ada peringkat
- One-Time Pad Program in Python LanguageDokumen2 halamanOne-Time Pad Program in Python Languagebatch22ubitBelum ada peringkat
- Risk ITDokumen5 halamanRisk ITLuis MalaverBelum ada peringkat
- UoN Access Control Policy v3Dokumen8 halamanUoN Access Control Policy v3robbiewalker201Belum ada peringkat
- Domain 1 Task & Knowledge StatementsDokumen4 halamanDomain 1 Task & Knowledge StatementsJuan PerezBelum ada peringkat
- Disaster Risk Reduction and Management PlanDokumen2 halamanDisaster Risk Reduction and Management Planraikojones02Belum ada peringkat
- Keterlibatan Penyandang Disabilitas Penting dalam Penanggulangan BencanaDokumen10 halamanKeterlibatan Penyandang Disabilitas Penting dalam Penanggulangan BencanaUlfahmi azmawi ZainulBelum ada peringkat
- SECURITY or PHYSICAL SECURITY or RISK ASSESSMENTDokumen3 halamanSECURITY or PHYSICAL SECURITY or RISK ASSESSMENTapi-1216271390% (1)
- Finger Sensor Solar Locks With Camera - Smart LockDokumen10 halamanFinger Sensor Solar Locks With Camera - Smart LockShivaprasad NairBelum ada peringkat
- VU23217 Session-01Dokumen22 halamanVU23217 Session-01Ryan NguyenBelum ada peringkat
- 4th CISO Middle East Summit Feb12 WDokumen6 halaman4th CISO Middle East Summit Feb12 WParthasarathy P RamaswamiBelum ada peringkat
- Chapter 14: Key Management and DistributionDokumen6 halamanChapter 14: Key Management and DistributionyossraBelum ada peringkat
- TLS-450PLUS: Benefits of Upgrading To TheDokumen8 halamanTLS-450PLUS: Benefits of Upgrading To TheEl Menol Con FlowBelum ada peringkat
- Labour and Working Conditions Management PlanDokumen47 halamanLabour and Working Conditions Management PlanShahab KhanBelum ada peringkat
- PNP Operations & Patrol GuidelinesDokumen8 halamanPNP Operations & Patrol GuidelinesPrince Joshua Bumanglag BSCRIMBelum ada peringkat
- Certified Ethical Hacker v10Dokumen3 halamanCertified Ethical Hacker v10zonetwyn0% (1)
- Security+ Guide To Network Security Fundamentals, Fifth EditionDokumen52 halamanSecurity+ Guide To Network Security Fundamentals, Fifth EditionVitæ ÆgisBelum ada peringkat
- Quiz - Introduction To Cybersecurity - Attempt ReviewDokumen2 halamanQuiz - Introduction To Cybersecurity - Attempt ReviewPonceBelum ada peringkat
- Cyber Security Incident Response High-Level Maturity Assessment ToolDokumen10 halamanCyber Security Incident Response High-Level Maturity Assessment Toollalou4Belum ada peringkat