IPsec VPN Azure
Diunggah oleh
mhalmarazHak Cipta
Format Tersedia
Bagikan dokumen Ini
Apakah menurut Anda dokumen ini bermanfaat?
Apakah konten ini tidak pantas?
Laporkan Dokumen IniHak Cipta:
Format Tersedia
IPsec VPN Azure
Diunggah oleh
mhalmarazHak Cipta:
Format Tersedia
Configuring IPsec VPN between a FortiGate and
Microsoft Azure
The following recipe describes how to configure a site-to-site IPsec VPN tunnel. In this
example, one site is behind a FortiGate and another site is hosted on Microsoft Azure,
for which you will need a valid Microsoft Azure profile.
Using FortiOS 5.2, the example demonstrates how to configure the tunnel between each
site, avoiding overlapping subnets, so that a secure tunnel can be established with the
desired security profiles applied.
1. Configuring the Microsoft Azure virtual network
2. Creating the Microsoft Azure virtual network gateway
3. Configuring the FortiGate tunnel
4. Creating the FortiGate firewall addresses
5. Creating the FortiGate firewall policies
6. Results
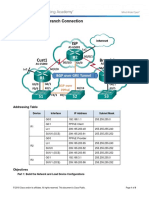
Site 1
FortiGate
LAN
Site 2
IPsec VPN
Internet
IPsec VPN
Azure
LAN
1. Configuring the Microsoft Azure
virtual network
Log into Microsoft Azure and click
New in the lower-left corner to add a
new service.
From the prompt, select Network
Services > Virtual Network >
Custom Create.
Under Virtual Network Details, enter
a Name for the VPN and a Location
where you want the VMs to reside,
then click the Next arrow.
Under DNS Servers and VPN
Connectivity, enable the Configure a
site-to-site VPN checkbox and enter
DNS server information if required.
Click the Next arrow.
Under Site-to-Site Connectivity,
enter a Name and IP Address for the
FortiGate device.
Under Address Space, include a
Starting IP and CIDR (Address
Count) for the tunnel, avoiding
overlapping subnets.
Click the Next arrow.
Under Virtual Network Address
Spaces, configure the desired
address space or accept the default
settings.
Select add gateway subnet to
configure a gateway IP and click the
Checkmark in the lower-right corner
to accept the configuration.
After accepting the configuration, you
will have to wait a short period of time
for the virtual network to be created,
but it shouldnt be long.
2. Creating the Microsoft Azure
virtual network gateway
On the networks home screen, click
the name of the virtual network you
just created.
Under this virtual network, go to the
Dashboard. You will notice that the
gateway has not yet been created.
You will create the gateway in this
step.
At the bottom of the screen, select
Create Gateway > Dynamic
Routing.
When prompted, select Yes.
The operation to create the virtual
network gateway will run. The process
takes a short amount of time.
Azure will indicate to you that the
gateway is being created. You may
wish to leave this running for a few
minutes as wait periods in excess of
10 minutes are common.
When the operation is complete, the
status changes and you are given a
Gateway IP Address.
The gateway will then attempt to
connect to the Local Network.
At the bottom of the screen, select
Manage Key.
The Manage Shared Key dialogue
appears. Copy the key that is shown.
You can select regenerate key if you
want to copy a different key.
Click the Checkmark when you are
confident that the key is copied.
You are now ready to configure the
FortiGate endpoint of the tunnel.
3. Configuring the FortiGate tunnel
Go to VPN > IPsec > Wizard and
select Custom VPN Tunnel (No
Template).
Enter a Name for the tunnel and click
Next.
Enter the desired parameters. Set
the Remote Gateway to Static IP
Address, and include the gateway
IP Address provided by Microsoft
Azure.
Set the Local Interface to wan1.
Under Authentication, enter the
Pre-shared Key provided by
Microsoft Azure.
Disable NAT Traversal and Dead
Peer Detection.
Under Authentication, ensure that
you enable IKEv2 and set DH Group
to 2.
Enable the encryption types shown
and set the Keylife to 56600
seconds.
Scroll down to Phase 2 Selectors
and set Local Address to the local
subnet and Remote Address to the
VPN tunnel endpoint subnet (found
under Virtual Network Address
Spaces in Microsoft Azure).
Enable the encryption types to match
Phase 1 and set the Keylife to 7200
seconds.
4. Creating the FortiGate firewall
addresses
Go to Policy & Objects >
Objects > Addresses and configure
a firewall address for the local
network.
Create another firewall object for the
Azure VPN tunnel subnet.
5. Creating the FortiGate firewall
policies
Go to Policy & Objects > Policy >
IPv4 and create a new policy for the
site-to-site connection that allows
outgoing traffic.
Set the Source Address and
Destination Address using the
firewall objects you just created.
When you are done, create another
policy for the same connection to
allow incoming traffic.
This time, invert the Source Address
and Destination Address.
6. Results
Go to VPN > Monitor > IPsec
Monitor. Right-click the tunnel you
created and select Bring Up to
activate the tunnel.
Go to Log & Report > Event Log >
VPN.
Select an entry to view more
information and verify the connection.
Return to the Microsoft Azure virtual
network Dashboard. The status of
the tunnel will show as Connected.
Data In and Data Out will indicate
that traffic is flowing.
Anda mungkin juga menyukai
- IPsec VPN To Microsoft AzureDokumen9 halamanIPsec VPN To Microsoft Azurejavier.reyesBelum ada peringkat
- CCDE FAQ v2Dokumen4 halamanCCDE FAQ v2Chandra Kumar MBelum ada peringkat
- VCN Deployment GuideDokumen22 halamanVCN Deployment GuideGiovanny ContrerasBelum ada peringkat
- Azure 104Dokumen11 halamanAzure 1048020 SakshiBelum ada peringkat
- Advanced Networking Best Practices With Azure ExpressRouteDokumen36 halamanAdvanced Networking Best Practices With Azure ExpressRoutetarunsood2009Belum ada peringkat
- 13) What Is Primary, Secondary, Stub & AD Integrated Zone?Dokumen4 halaman13) What Is Primary, Secondary, Stub & AD Integrated Zone?Siddu BalaganurBelum ada peringkat
- Implementing Virtual Routing and Forwarding VRF On Cisco Nexus Data CenterDokumen8 halamanImplementing Virtual Routing and Forwarding VRF On Cisco Nexus Data CenterzxcdBelum ada peringkat
- AZ-104 Course ContentDokumen7 halamanAZ-104 Course ContentIsmail SayyedBelum ada peringkat
- VMware Interview QuestionsDokumen9 halamanVMware Interview QuestionsSuman G100% (1)
- Masterng Network ProtocolDokumen8 halamanMasterng Network ProtocolsubhamayBelum ada peringkat
- LVM Resizing Guide - Howto Resize Logical Volumes in Linux - LVM, Resizing, Lvresize, Vgdisplay, LvdisplayDokumen7 halamanLVM Resizing Guide - Howto Resize Logical Volumes in Linux - LVM, Resizing, Lvresize, Vgdisplay, LvdisplayCrocodilicBelum ada peringkat
- 350 018 PDFDokumen530 halaman350 018 PDFamxyzBelum ada peringkat
- AWS Certified DevOps Engineer Professional QuestionsDokumen4 halamanAWS Certified DevOps Engineer Professional QuestionsSurendiran KaliyamoorthyBelum ada peringkat
- 400-101-1_formatted ExamDokumen986 halaman400-101-1_formatted ExamJoel Maxmillan RugarabamuBelum ada peringkat
- Weblogic Q & A - by Brahmaiah PDFDokumen45 halamanWeblogic Q & A - by Brahmaiah PDFvssprpvemuriBelum ada peringkat
- Lab Instructions and Answer Key: Configuring and Troubleshooting A Windows Server® 2008 Network InfrastructureDokumen297 halamanLab Instructions and Answer Key: Configuring and Troubleshooting A Windows Server® 2008 Network InfrastructureCarlos Ivan Chavez FuentesBelum ada peringkat
- Mcse NetwDokumen56 halamanMcse NetwHuỳnh NguyễnBelum ada peringkat
- Azure Interview Questions and Answers GuideDokumen7 halamanAzure Interview Questions and Answers Guidehanuman challisaBelum ada peringkat
- Lab - Configure A Branch ConnectionDokumen9 halamanLab - Configure A Branch Connectionratacle57% (7)
- Azure Batch NotesDokumen3 halamanAzure Batch NotessharqBelum ada peringkat
- Linux Interview QuestionsDokumen51 halamanLinux Interview Questionsseenu933Belum ada peringkat
- Mani ResumeDokumen4 halamanMani ResumeSateesh MakenaboinaBelum ada peringkat
- Interview Questions 1Dokumen13 halamanInterview Questions 1Rajesh KannanBelum ada peringkat
- Exchange Interview QuestionsDokumen187 halamanExchange Interview QuestionsVipul KumarBelum ada peringkat
- OCI 2023 Multicloud Architect Associate Sure PassDokumen41 halamanOCI 2023 Multicloud Architect Associate Sure PassAshis DasBelum ada peringkat
- Failover Clustering What's NewDokumen192 halamanFailover Clustering What's NewAnderson LimaBelum ada peringkat
- Cisco UCMDokumen1.266 halamanCisco UCMdondegBelum ada peringkat
- Infomration On DNSDokumen255 halamanInfomration On DNSNaren RammohanBelum ada peringkat
- VMware Virtual Lab Student Instructions 120205 v12-1Dokumen8 halamanVMware Virtual Lab Student Instructions 120205 v12-1Mahmoud Ali Abdel SalamBelum ada peringkat
- Cisco CCNP Routing and Switching 300-115 SWITCH (2019) Exam Dumps Are Out - Download and PrepareDokumen5 halamanCisco CCNP Routing and Switching 300-115 SWITCH (2019) Exam Dumps Are Out - Download and PrepareDavidEButlerBelum ada peringkat
- Red Hat Enterprise Linux 7 Firewalld HowTo GuideDokumen23 halamanRed Hat Enterprise Linux 7 Firewalld HowTo Guideamine.besrour5214Belum ada peringkat
- 300 101Dokumen484 halaman300 101Diego Suarez0% (1)
- AZ 104T00A ENU PowerPoint - 00Dokumen17 halamanAZ 104T00A ENU PowerPoint - 00jwssdmhjw5Belum ada peringkat
- AWS - DOP-C01 - DumpsTool - MansoorDokumen4 halamanAWS - DOP-C01 - DumpsTool - MansoorMansoor AhmedBelum ada peringkat
- Hands-On Lab: Creating A Windows Azure Virtual MachineDokumen9 halamanHands-On Lab: Creating A Windows Azure Virtual MachineViknesh RajandranBelum ada peringkat
- Lab OratoriosDokumen101 halamanLab OratoriosAnonymous RKUQta8Belum ada peringkat
- CCNP3V30 Lab CorrectionDokumen16 halamanCCNP3V30 Lab CorrectionveeramachanenipurnaprasadBelum ada peringkat
- Configuring Kerberos SSOfor OBIEE12 C Part 2Dokumen20 halamanConfiguring Kerberos SSOfor OBIEE12 C Part 2Asad HussainBelum ada peringkat
- Active Directory ReplicationDokumen63 halamanActive Directory ReplicationPrakash MoorthyBelum ada peringkat
- Itexamguide: High-Quality It Cert Exam Study GuideDokumen7 halamanItexamguide: High-Quality It Cert Exam Study GuideSaira KhanBelum ada peringkat
- CP R80 Gaia InstallationAndUpgradeGuideDokumen33 halamanCP R80 Gaia InstallationAndUpgradeGuideMaria Regiane Lopes BarrozoBelum ada peringkat
- Reference Architecture: 11 April 2019 Vrealize Automation 7.6Dokumen41 halamanReference Architecture: 11 April 2019 Vrealize Automation 7.6Mahender Singh Yadav100% (1)
- Classless Inter-Domain Routing (Cidr)Dokumen5 halamanClassless Inter-Domain Routing (Cidr)Mohamed Abdou0% (1)
- Senior DevOps Engineer with AWS ExperienceDokumen6 halamanSenior DevOps Engineer with AWS ExperienceAnuditya SharmaBelum ada peringkat
- Weblogic Expert Seeks New ChallengeDokumen3 halamanWeblogic Expert Seeks New ChallengeT PrasadBelum ada peringkat
- Azure Core Services OverviewDokumen29 halamanAzure Core Services Overviewrajagopalan19100% (1)
- Cisco HyperFlex 40 in Action v1Dokumen92 halamanCisco HyperFlex 40 in Action v1Mahamoud AliBelum ada peringkat
- Azure RMDokumen1.870 halamanAzure RMBala SubramanyamBelum ada peringkat
- BCO1505-VMware Vsphere Replication Technical Walk-Through With Engineering - Final - US PDFDokumen35 halamanBCO1505-VMware Vsphere Replication Technical Walk-Through With Engineering - Final - US PDFkinan_kazuki104100% (1)
- Remote Access Configuration PDFDokumen5 halamanRemote Access Configuration PDFAli SaiviBelum ada peringkat
- Microsoft Azure Overview Sales GuideDokumen55 halamanMicrosoft Azure Overview Sales GuideRicardo LacalBelum ada peringkat
- Narayana P: Email: Mobile Experience SummaryDokumen4 halamanNarayana P: Email: Mobile Experience Summaryckesava_2Belum ada peringkat
- Network Load BalancingDokumen17 halamanNetwork Load BalancingAga ABelum ada peringkat
- Ccna SecurityDokumen292 halamanCcna SecurityAmine InpticBelum ada peringkat
- SQL Server Denali - Alwayson (Hadr) : Step-By-Setup Setup GuideDokumen17 halamanSQL Server Denali - Alwayson (Hadr) : Step-By-Setup Setup GuideamarBelum ada peringkat
- Vmware Site Recovery Manager 8.2 Theory and LabDokumen428 halamanVmware Site Recovery Manager 8.2 Theory and LabFeliz Bunguele100% (1)
- Laptop guide: history, uses, and componentsDokumen1 halamanLaptop guide: history, uses, and componentsvkboss1301Belum ada peringkat
- Huawei Video Phone ESpace 8850 Administrator Guide (V100R001C01 - 01)Dokumen130 halamanHuawei Video Phone ESpace 8850 Administrator Guide (V100R001C01 - 01)minhBelum ada peringkat
- Rocscience Installation Guide for Commercial NetworksDokumen14 halamanRocscience Installation Guide for Commercial NetworksRasa KuBelum ada peringkat
- Silabus Kursus Keahlian Komputer Pada MMSIDokumen4 halamanSilabus Kursus Keahlian Komputer Pada MMSIR. Arief Ferdiansyah PrajaBelum ada peringkat
- Understanding CPU Components and TerminologyDokumen1 halamanUnderstanding CPU Components and TerminologyCher LongBelum ada peringkat
- Movilizer SAP PM-CS enDokumen8 halamanMovilizer SAP PM-CS enJosue QuirozBelum ada peringkat
- Bcs 011 PDFDokumen33 halamanBcs 011 PDFRahul RawatBelum ada peringkat
- MECHATRONICSDokumen83 halamanMECHATRONICSHod of ME PRRMBelum ada peringkat
- LogDokumen95 halamanLogAnugrah FajarBelum ada peringkat
- Infomration On DNSDokumen255 halamanInfomration On DNSNaren RammohanBelum ada peringkat
- H9tj6aae Lab07Dokumen22 halamanH9tj6aae Lab07Manuel RBelum ada peringkat
- (GUIDE) (HOW-To) Crack Android Pattern Lock! - Xda-DevelopersDokumen7 halaman(GUIDE) (HOW-To) Crack Android Pattern Lock! - Xda-DevelopersJeeva SuriyanBelum ada peringkat
- Datasheet XPG SX8200 en 20180316Dokumen2 halamanDatasheet XPG SX8200 en 20180316rumi1975Belum ada peringkat
- What Is x64dbgDokumen31 halamanWhat Is x64dbgAnonymous Q96RQrTBelum ada peringkat
- MaxSea User ManualDokumen303 halamanMaxSea User ManualMaria Louiza Loucas100% (1)
- Developing A Springboard ModuleDokumen15 halamanDeveloping A Springboard Modulefedor1Belum ada peringkat
- RS3668 - Computer Science Grade 9 PDFDokumen273 halamanRS3668 - Computer Science Grade 9 PDFShree Shrestha100% (1)
- Cisco Aci VMDCDokumen39 halamanCisco Aci VMDCFaisal Abdul Gaffoor100% (1)
- Catalogo 3COMDokumen91 halamanCatalogo 3COMbrreakerrBelum ada peringkat
- Installation Requirements UsDokumen20 halamanInstallation Requirements Usbrayam11Belum ada peringkat
- Bannari Amman Institute of Technology: Regulation: 2018Dokumen2 halamanBannari Amman Institute of Technology: Regulation: 2018veerakumarsBelum ada peringkat
- Discover Media PQ Gen.2 April - 2018 - enDokumen5 halamanDiscover Media PQ Gen.2 April - 2018 - enMir MihailescuBelum ada peringkat
- 01.radware DefensePro Tech SpecDokumen3 halaman01.radware DefensePro Tech SpecLe Vinh HienBelum ada peringkat
- IP SAN Data Storage For Media ApplicationsDokumen4 halamanIP SAN Data Storage For Media ApplicationsAmerican Megatrends IndiaBelum ada peringkat
- LAB 1 Operating SystemDokumen7 halamanLAB 1 Operating SystemV-Yuggan YoBelum ada peringkat
- F.A.Q. enDokumen30 halamanF.A.Q. enmxnoxnBelum ada peringkat
- Microsoft.70 236 Exchange DumpsDokumen94 halamanMicrosoft.70 236 Exchange Dumpssk64232Belum ada peringkat
- UntitledDokumen64 halamanUntitledMamadou oury DialloBelum ada peringkat
- 3D display project report metadata at core.ac.ukDokumen58 halaman3D display project report metadata at core.ac.ukBharathBelum ada peringkat