ITIL Overview Diagram English
Diunggah oleh
yudesh.g1857Hak Cipta
Format Tersedia
Bagikan dokumen Ini
Apakah menurut Anda dokumen ini bermanfaat?
Apakah konten ini tidak pantas?
Laporkan Dokumen IniHak Cipta:
Format Tersedia
ITIL Overview Diagram English
Diunggah oleh
yudesh.g1857Hak Cipta:
Format Tersedia
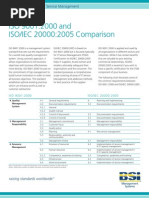
CSI Approach
Continual Service Improvement
7 Steps improvement process
Service Measurement
Service Reporting
Service Design
Define policies
and methods
Plan design resources
and capabilities
SKMS
Coordinate design
activities
Capacity
Management
Planning
Business/Service/
Component capacity
Maintain catalogue
SKMS
CMIS
Capture Service
Level Requirements
SCMIS
UC
Review and update
OLA (and UC)
Supplier
Management
Technical Business
Service Catalogue
Management
Negotiate &
establish SLA
Produce and
present service
reports
Strategies & policies
Requirements
Define service and
service package
Design Coordination
SLA
Descripti
on
Servic
Suppor
e
t
Hours
Establish contract
Performance
SLA
Duratio
n
Signatur
e
Align with service
Portfolio and CMS
SKMS
SLA
Renew/terminate
suppliers and
contracts
Service
Catalogues
10%
30%
Publish and update
Capacity Plan
Requirements
Plan, design and
model for
performance
Demand
Management
Application sizing
Monitor, adjust &
maintain
Report & Improve
Projected
Service
Unavailability
Performance
reports
Service/Component
availability
Requirements
Risk assessment
and management
Vital Business
Functions (VBF)
Plan and design for
availability
Implement
Monitor, adjust &
maintain
Report & Improve
Coordinate
individual designs
Strategy Management for IT Services
Standards
Support business
vision and mission
Architecture
Identify customers
Prioritize
investments
Identify market
space
Governance
Service
Portfolio
10%
Continuity
Plan
Availability
Plan
Service Operation
Applications Management function
Service Portfolio
Management
Customer Portfolio
Define
Customer
Agreements
Portfolio
Evaluate services
Customer
Satisfaction
Charge-back
Technical Management function
Analyse
Service Desk function
Authorise
Self serve
Charter
SKMS
Service
Requests
Events and
alerts
Event Management
Design for event
management
Configure system
Notification/
Detection/Log
Request fulfillment
Modeling
Respond and close
Access Management
Log request
Receive request
Automate workflow
Request verification
Fulfillment
Provide access rights
Closure
Filter/correlation/
significance
Alert and response
Request
Models
Log and track access
1
Request
Models
Revise and tuning
Remove-restrict
access rights
Maintain groups and
roles
SKMS
Roles and
groups
Organizational Change
Deming Cycle
Detect and log
Categorize &
prioritize
Categorise and
prioritize
Initial support
Investigate and
diagnose
Diagnose
Workaround
Close
SKMS
Raise known error
Incident
records
Resolve
Known error
records
Follow up &
communicate
Problem
records
User satisfaction
survey
Ownership
Close
Major problem
review
Service
Improvement
proposals
Service review and
improvement planning
Service
Design
Package
(SDP)
Discovery
tools
Change
Management
Log, review and
categorize
Assess and authorize
build and test
Mon
27
Organization and
RACI Charts
Tue
28
Change Schedule
Work
order
Release and
Deployment
Management
3
Release
packages
Knowledge
Management
Knowledge
management strategy
Manage data,
information,
knowledge
Maintain and control
Authorize deployment
Status report
Spares
Inventory and
licence management
Emergency change
Transition Planning and Support
Setup Transition
Strategy
Lifecycle
stages
Pilot and tests
Deployment
planning
Execute
deployment,
transfer, retire
Prepare
transition
Service Validation
and Testing
Service and quality
assurance
Early life support
Test policies
Test strategy
Knowledge transfer
Test levels and
models
Using SKMS
Test approach and
technique
Process review and
compliance
CMDBs
Verification and
audit
Measure and report
Prepare
Release review
CMS
Plan and coordinate
build and test
Post Implementation
Review
Build and test cycles
Deployment
Plans
SKMS
Plan and Identify
Coordinate
deployment
Plan
Validation and
Tests Plans
Service Asset and
Configuration
Management
CAB
Financial Plan
Patch
Management
Identifiy and log
Resolve and recover
Definitive
Media Library
Return On
Investment
Problem
Management
Risk assessment and
management
Countermeasures
Define & enforce
information security
policies
Requirements & plans
Document &
implement security
controls
Monitor & manage
security breach/
incidents/problems
Improvement of
security controls
SKMS
ISMS
Service Cost
Structure
Incident
Management
Information Security
management
Risk
Management
Service Transition
Business activities
and patterns
Funding
Service
Requirements
Security
Policies
ITSCM and the BCM
Business Impact
Analysis (BIA)
Risk assessment
and management
Countermeasures
Requirements and
strategy
Plan recovery (DRP)
and continuity
Implement
Test and review
On going operation
and maintain
Invoke
Demand
Management
IT Financial
Management
Business
Relationship
Management
Review designs and
handover SDP
IT Service
Continuity
Management
SKMS
AMIS
30%
IT Operations Management function
Monitor individual
designs
Service Strategy
SKMS
Maintain service
catalogues
20%
Plan individual
designs
Availability
Management
Produce service
catalogues
Evaluation of new
suppliers
Maintain SCMIS
Improve
service design
Service Level
Management
SLA/
OLA
SKMS
Manage design
risks and issues
ITIL 2011
CSI Register
Transition
policies
release
policies
Plan and coordinate
Transition
Support
transition
And asset
Change Evaluation
Evaluation plan
Expected and
unexpected effects of
change
Evaluation of expected
performance
Evaluation of real
performance
Risk management
Test plan and results
CSI Framework and
Quality System
Version
2015/01/11
IT Governance
Anda mungkin juga menyukai
- Itil ISO 20000 C T Itil ISO 20000 C T: ITIL V3 Foundation Study GuideDokumen1 halamanItil ISO 20000 C T Itil ISO 20000 C T: ITIL V3 Foundation Study GuideNancy HaeltermanBelum ada peringkat
- ITIL v3 Service Lifecycle ChartDokumen1 halamanITIL v3 Service Lifecycle Chartdardenne_tBelum ada peringkat
- CHART v.2.0 - ITSM - DRUCK PDFDokumen1 halamanCHART v.2.0 - ITSM - DRUCK PDFamirel80Belum ada peringkat
- ITIL V3 Lifecycle OverblikDokumen1 halamanITIL V3 Lifecycle OverblikDavid RovsingBelum ada peringkat
- Itil at A GlanceDokumen1 halamanItil at A Glancefernandomp100% (1)
- Figure 23-Overall C T Framework: Business ObjectivesDokumen1 halamanFigure 23-Overall C T Framework: Business ObjectivesAbdul Rohman AchmaBelum ada peringkat
- Lesson 6 - ITIL Management PracticesDokumen90 halamanLesson 6 - ITIL Management PracticesAlahor DelPubgBelum ada peringkat
- ITIL Capacity Management: Much More Than Charts Over CoffeeDokumen44 halamanITIL Capacity Management: Much More Than Charts Over CoffeeGary ReynoldsBelum ada peringkat
- Iso ItilDokumen1 halamanIso ItilAlvi Nailus Sa'adahBelum ada peringkat
- Network Operations Center A Complete Guide - 2019 EditionDari EverandNetwork Operations Center A Complete Guide - 2019 EditionBelum ada peringkat
- Introducing ITIL Best Practices For IT Service Management: Presentation Will Begin at 9:00 AmDokumen90 halamanIntroducing ITIL Best Practices For IT Service Management: Presentation Will Begin at 9:00 Amearth2783Belum ada peringkat
- ITILv3-2011 Continual Service ImprovementDokumen1 halamanITILv3-2011 Continual Service ImprovementkjaffeBelum ada peringkat
- Service Capacity Management Complete Self-Assessment GuideDari EverandService Capacity Management Complete Self-Assessment GuideBelum ada peringkat
- Enterprise Architecture A Complete Guide - 2021 EditionDari EverandEnterprise Architecture A Complete Guide - 2021 EditionBelum ada peringkat
- RKT Itsm OverviewDokumen71 halamanRKT Itsm OverviewMohammed Anwer KaleemBelum ada peringkat
- Continual Service Improvement (ITIL CSI) v3 - Process EvaluationDokumen1 halamanContinual Service Improvement (ITIL CSI) v3 - Process EvaluationAndrea GiulianiBelum ada peringkat
- TICsDokumen4 halamanTICsBryand Sanchez PalaciosBelum ada peringkat
- ITOM IT Operations Management Software Complete Self-Assessment GuideDari EverandITOM IT Operations Management Software Complete Self-Assessment GuideBelum ada peringkat
- VINSYS Service Offerings in Itil / Itsm: Key To DiagramDokumen1 halamanVINSYS Service Offerings in Itil / Itsm: Key To DiagramrahulkedarBelum ada peringkat
- IT Organizational Design A Complete Guide - 2019 EditionDari EverandIT Organizational Design A Complete Guide - 2019 EditionBelum ada peringkat
- Using ITSM to Optimize ResourcesDokumen48 halamanUsing ITSM to Optimize ResourcesJulius Villacruz100% (1)
- IT Operations Management A Complete Guide - 2020 EditionDari EverandIT Operations Management A Complete Guide - 2020 EditionBelum ada peringkat
- Introduction To ITIL: An Overview of The Fundamentals of ITILDokumen9 halamanIntroduction To ITIL: An Overview of The Fundamentals of ITILRaghuvamsi KandukuriBelum ada peringkat
- Service Desk Automation Software A Complete Guide - 2020 EditionDari EverandService Desk Automation Software A Complete Guide - 2020 EditionBelum ada peringkat
- Enterprise Architecture EA A Complete Guide - 2019 EditionDari EverandEnterprise Architecture EA A Complete Guide - 2019 EditionBelum ada peringkat
- ITIL v3 CSI Sample Questions2Dokumen35 halamanITIL v3 CSI Sample Questions2kultiwett100% (1)
- Capacity Management DeckDokumen29 halamanCapacity Management DeckMelissa Miller100% (1)
- IT Infrastructure Deployment A Complete Guide - 2020 EditionDari EverandIT Infrastructure Deployment A Complete Guide - 2020 EditionBelum ada peringkat
- ITILDokumen7 halamanITILabcdBelum ada peringkat
- Cloud Center of Excellence CCoE Complete Self-Assessment GuideDari EverandCloud Center of Excellence CCoE Complete Self-Assessment GuideBelum ada peringkat
- Be An IT Services Broker: HP Service Integration and ManagementDokumen15 halamanBe An IT Services Broker: HP Service Integration and ManagementRamón AlonsoBelum ada peringkat
- ISO9001 20000 Cross-ReferenceDokumen2 halamanISO9001 20000 Cross-ReferenceAlvi Nailus Sa'adahBelum ada peringkat
- What Is IT Service Management - ITIL - AXELOSDokumen4 halamanWhat Is IT Service Management - ITIL - AXELOSaliBelum ada peringkat
- Survey of IT Governance Capability in 5 Countries Using ISO 38500 FrameworkDokumen27 halamanSurvey of IT Governance Capability in 5 Countries Using ISO 38500 FrameworkLeo CerenoBelum ada peringkat
- Integrated Business Planning A Complete Guide - 2020 EditionDari EverandIntegrated Business Planning A Complete Guide - 2020 EditionBelum ada peringkat
- ITIL - Session 01 - ITIL QualificationDokumen17 halamanITIL - Session 01 - ITIL QualificationAhmad Abdul HaqBelum ada peringkat
- 2 1466061-16PL-213 No Item MKD': For ConstructionDokumen1 halaman2 1466061-16PL-213 No Item MKD': For ConstructionKhaled KittanaBelum ada peringkat
- 2 1466061-16PL-212 No Item MKD': For ConstructionDokumen1 halaman2 1466061-16PL-212 No Item MKD': For ConstructionKhaled KittanaBelum ada peringkat
- 16LO84Dokumen1 halaman16LO84Khaled KittanaBelum ada peringkat
- For This Masked Area Refere To Sec A-ADokumen1 halamanFor This Masked Area Refere To Sec A-AKhaled KittanaBelum ada peringkat
- 284 Masked Area: 5 For This Masked Area Refere To Sec A-ADokumen1 halaman284 Masked Area: 5 For This Masked Area Refere To Sec A-AKhaled KittanaBelum ada peringkat
- 16LO1Dokumen1 halaman16LO1Khaled KittanaBelum ada peringkat
- PL30X300 X 350 PL30X300: 1 1466061-16PL-1 No Item MKD'Dokumen1 halamanPL30X300 X 350 PL30X300: 1 1466061-16PL-1 No Item MKD'Khaled KittanaBelum ada peringkat
- PL25X135 X 135: 4 1466061-16PL-206 No Item MKD'Dokumen1 halamanPL25X135 X 135: 4 1466061-16PL-206 No Item MKD'Khaled KittanaBelum ada peringkat
- 80 Masked Area: For This Masked Area Refere To Sec A-ADokumen1 halaman80 Masked Area: For This Masked Area Refere To Sec A-AKhaled KittanaBelum ada peringkat
- PL15X269 X 558: 20 1466061-16LO-82 No Item MKD'Dokumen1 halamanPL15X269 X 558: 20 1466061-16LO-82 No Item MKD'Khaled KittanaBelum ada peringkat
- 09 Q7 ITIL 2011 Overview Diagram English 11012015Dokumen1 halaman09 Q7 ITIL 2011 Overview Diagram English 11012015Khaled KittanaBelum ada peringkat
- 16LO1Dokumen1 halaman16LO1Khaled KittanaBelum ada peringkat
- ITIL Foundation Overview v5 4 FINALDokumen2 halamanITIL Foundation Overview v5 4 FINALKhaled KittanaBelum ada peringkat
- 09 Q7 ITIL 2011 Overview Diagram English 11012015Dokumen1 halaman09 Q7 ITIL 2011 Overview Diagram English 11012015Khaled KittanaBelum ada peringkat
- OUT of Scope: Local Support ScheduleDokumen1 halamanOUT of Scope: Local Support ScheduleKhaled KittanaBelum ada peringkat
- BRMP Overview v1 4 A3 FinalDokumen2 halamanBRMP Overview v1 4 A3 FinalKhaled KittanaBelum ada peringkat
- COBIT Foundation Overview v2 4 FINALDokumen2 halamanCOBIT Foundation Overview v2 4 FINALvrsymart100% (3)
- TI25xl25/: Local Support ScheduleDokumen1 halamanTI25xl25/: Local Support ScheduleKhaled KittanaBelum ada peringkat
- TI25xl25/: Local Support ScheduleDokumen1 halamanTI25xl25/: Local Support ScheduleKhaled KittanaBelum ada peringkat
- Steel framing plans for vapor shelterDokumen1 halamanSteel framing plans for vapor shelterKhaled KittanaBelum ada peringkat
- Steel framing plans for vapor shelterDokumen1 halamanSteel framing plans for vapor shelterKhaled KittanaBelum ada peringkat
- Steel framing plans for vapor shelterDokumen1 halamanSteel framing plans for vapor shelterKhaled KittanaBelum ada peringkat