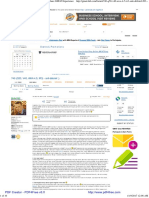
DoD IA Policy Chart - 23 April 2010
Diunggah oleh
David Glenn ProctorHak Cipta
Format Tersedia
Bagikan dokumen Ini
Apakah menurut Anda dokumen ini bermanfaat?
Apakah konten ini tidak pantas?
Laporkan Dokumen IniHak Cipta:
Format Tersedia
DoD IA Policy Chart - 23 April 2010
Diunggah oleh
David Glenn ProctorHak Cipta:
Format Tersedia
Cyber, Identity & Information Assurance (CIIA)
Build and Operate a Trusted GIG Related Policies and Issuances
Developed by DASD(CIIA)
CIIA GOAL 1: ORGANIZE Last Updated: April 23, 2010
Send questions/suggestions to iatac@dtic.mil
1.1 Lead and Govern
AUTHORITIES
DoDD 8000.01 DoDD 8500.01E DoDI 8500.2 DoD Cyber, Identity & Information ASD(NII)/DoD CIO G&PM 11-8450 Quadrennial Defense Review (QDR) Federal Information Security
Management of the DOD Information Information Assurance (IA) Information Assurance Implementation Assurance Strategic Plan DoD GIG Computing Report Management Act, 44 U.S.C. §3541 et
Enterprise Clinger-Cohen Act, Pub. L. 104-106
seq
Guidance for Development of the National Military Strategic Plan for the National Military Strategy for Title 10 Title 14
National Defense Strategy (NDS) National Military Strategy (NMS)
Force (GDF) for 2010-2015 War on Terrorism Cyberspace Operations (NMS-CO) Armed Forces Cooperation With Other Agencies
(§§2224, 3013(b), 5013(b), 8013(b)) (Ch. 7:§§ 141,144,145,148,149,150)
Title 32 Title 40
CIIA GOAL 1: ORGANIZE CIIA GOAL 2: ENABLE CIIA GOAL 3: ANTICIPATE CIIA GOAL 4: PREPARE National Guard Public Buildings, Property, and Works
(§102) (Ch. 113: §§11302, 11315, 11331)
1.2 Design for the Fight 2.1 Secure Data in Transit 3.1 Understand the Battlespace
4.1 Develop and Maintain Trust… Title 44 Title 50
SP 800-59 Public Printing and Documents War and National Defense
SP 800-39 FIPS 140-2 NSTISSI-4006 FIPS 199 (§§401, 1801)
Common Criteria Evaluation and Standards for Security Categorization Guideline for Identifying an Information (Ch. 35: §§3541, 3504)
Managing Risk from Info Systems: An Security Requirements for Controlling Authorities for COMSEC NSTISSD-600
Validation Scheme (CCEVS) Cryptographic Modules Material of Federal Info. and Info. Systems System as a NSS NSTISSI-7002
Organizational Perspective Communications Security (COMSEC) TEMPEST Glossary UCP
Monitoring Unified Command Plan
NTISSP-11 DFARS NSTISSP-101 SP 800-60 R1
NSTISSI-7003 Guide for Mapping Types of Info and (US Constitution Art II, Title 10 & 50)
National Information Assurance Subpart 208.74, Enterprise Software National Policy on Securing Voice CNSSP-12 CNSSP-21
Protective Distribution Systems (PDS) Communications Info Systems to Security Categories
Acquisition Policy Agreements National IA Policy for Space Systems National IA Policy on Enterprise
Used to Support NSS Architectures for NSS
DoDD 4630.05 CNSSI-5000 CNSSI-5001 NATIONAL / FEDERAL
DoDD 8115.01 Guidelines for Voice Over Internet Type-Acceptance Program for VoIP DoDD 5144.1
Interoperability and Supportability of IT IT Portfolio Management DoDD 3100.10
and National Security Systems (NSS) Protocol (VoIP) Computer Telephony Telephones ASD for Networks and Information
3.2 Prevent and 3.3 Prevent Space Policy Integration/DoD CIO
A-130, Management of Fed Info Computer Fraud and Abuse Act
Resources, Appendix III, Security of
DoDI 8115.02 DoDI 8510.01 CNSSP-1
National Policy for Safeguarding and
CNSSP-15
National Policy on the Use of AES to
Delay Attackers… Attackers from Staying… DTM 09-016
Fed Automated Info Sys
Title 18 (§1030)
IT Portfolio Management DoD IA Certification and Accreditation DoDD 8581.1
Implementation Process (DIACAP) Control of COMSEC Material Protect National Security Systems… IA Policy for Space Systems Used by SCRM to Improve the Integrity of
the DoD Components Used in DoD Systems Federal Wiretap Act Foreign Intelligence Surveillance Act
CNSSP-19 DoDD O-8530.1 Title 18 (§2510 et seq.) Title 50 (§1801 et seq)
DoDI 8580.1 CNSSP-17 Computer Network Defense (CND)
DIACAP Knowledge Service Information Assurance (IA) in the National Information Assurance Policy National Policy Governing the Use of DoDD 3020.40
Defense Acquisition System on Wireless Capabilities HAIPE Products Defense Critical Infrastructure Pen Registers and Trap and Trace Presidential Memo, “Classified
DoDI 8551.1 Protection Program Devices Information and Controlled Unclassified
CNSSP-25 NACSI-2005 Title 18 (§3121 et seq.) Information,” 27 May 09
Alignment Framework for the GIG IA IA Component of the GIG Integrated National Policy for PKI in National Communications Security (COMSEC) Ports, Protocols, and Services Management (PPSM)
Architecture (AFG) version 1.1 Architecture, v1.1 Security Systems End Item Modification
DoDI 8552.01
4.2 Strengthen Cyber Readiness Stored Communications Act Executive Order 12958
DNI CIO Memo NACSI-2006, Foreign Military Sales of NACSI-6002 Title 18 (§2701 et seq.) Classified National Security Information
DoDD 5000.01 Nat’l COMSEC Instruction Protection of Use of Mobile Code Technologies in DoD Information Systems
Intelligence Community (IC) Enterprise COMSEC Articles and Services to
The Defense Acquisition System Foreign Gov’ts and Int’l Orgs Gov’t Contractor Telecomm’s SP 800-18 R1 SP 800-30
Software Licensing Guide for Developing Security Plans Risk Management Guide for IT Executive Order 13231 NSD 42, National Policy for the
DoDI O-8530.2 for Federal Information Systems Systems Critical Infrastructure Protection in the Security of Nat’l Security Telecom and
DoDI 5000.02 DoDI 7000.14 NCSC-5, Nat’l Policy on Use of DoDD 4640.13 Information Age Information Systems
Support to Computer Network Defense (CND)
Operation of the Defense Acquisition Financial Management Policy and Cryptomaterial by Activities Operating Mgt of Base and Long Haul
in High Risk Environments DoDD O-5100.30 DoDD S-5100.44
System Procedures (PPBE) Telecomms Equipment and Services Defense and National Leadership
Department of Defense (DoD) NSPD 54 / HSPD 23 FAR
DoDI 4650.1 DoD O-8530.1-M Command and Control (C2) Command Capability (DNLCC) (U) Computer Security and Monitoring Federal Acquisition Regulation
ASD(NII)/DoD CIO Memo DoDD 8100.2 CND Service Provider Certification and Accreditation Program
DoDD 7045.20 DoD Support for the SmartBUY Use of Commercial Wireless Devices, Policy and Procedures for Mgt and Use
Capability Portfolio Management of the Electromagnetic Spectrum DoDI 8560.01
Initiative Services, and Tech in the DoD GIG
COMSEC Monitoring and Information National Strategy to Secure
CJCSI 6510.01E National Security Strategy
CJCSI 3170.01G DoDI 8420.01 Assurance Readiness Testing Cyberspace
DoD CIO G&PM 12-8430 DoDI 8523.01 Information Assurance (IA) and Computer Network Defense (CND)
Joint Capabilities Integration and Commercial WLAN Devices, Systems, Communications Security (COMSEC)
Acquiring Commercial Software Development System (JCIDS) and Technologies NSTISSI-4002 CNSSD-502
CJCSI 6212.01E DoDI S-5200.16
CJCSM 6510.01A 4.3 Sustain Missions Classification Guide for COMSEC National Directive On Security of
DoDD 8521.01E Information Assurance (IA) and Computer Network Defense (CND) Information National Security Systems
Interoperability and Supportability of IT Objectives and Min Stds for COMSEC Department of Defense Biometrics
and National Security Systems Measures used in NC2 Comms CNSSD-900, Governing Procedures of CNSSD-901
FIPS 200 CNSSI-1001
ASD(C3I) Policy Memo NSTISSI-7001 National Instruction on Classified the Committee on National Security Nat’l Security Telecomm’s and Info Sys
CJCSI 6510.06A Minimum Security Requirements for NONSTOP Countermeasures Systems Security (CNSS) Issuance System
CJCSI 6510.02C Guidance for CND Response Actions Information Spillage
Communications Security Releases to Federal Information Systems
1.3 Develop the Workforce Cryptographic Modernization Plan
Foreign Nations DoDD 3020.40
ASD(NII)/DoD CIO Memo CNSSI-4004, Destruction and CNSSI-7000 CNSSI-4009
ASD(NII)/DoD CIO Memo National Information Assurance DoD Policy and Responsibilities for
NSTISSI-4000 Federal Desktop Core Configuration DoD Guidance on Protecting Emergency Protection Procedures for TEMPEST Countermeasures for
NSTISSD-501 Facilities) Glossary Critical Infrastructure
National Training Program for COMSEC Equipment Maintenance 2.2 Manage Access (FDCC) Personally Identifiable Information (PII) COMSEC and Class. Material
INFOSEC Professionals and Maintenance Training
DTM 08-060 ASD(NII)/DoD CIO Memo, Encryption CNSSP-6 CNSSP-18
HSPD-12 National Policy for C&A of National National Policy on Classified
NSTISSI-4011 NSTISSI-4015 Policy for a Common ID Standard for
M-05-24 Policy on Use of DoD Info Sys – Std of Unclass DAR on Mobile Comp
Security Telecom and Info Systems Information Spillage
Operational
National Training Standard for National Training Standard for System Implementation of HSPD-12 Consent Banner and User Agreement Devices and Removable Storage
Federal Employees and Contractors
INFOSEC Professionals Certifiers
ASD(NII)/DoD CIO Memo CNSSP-22 CNSSP-300 SD 527-01
FIPS 201-1 NSTISSI-3028 National Policy on Control of Computer Network Directives
CNSSD-500 CNSSI-4012 Protection of Sensitive DoD Data at IA Risk Management Policy for (CTO, FRAGO, WARNORD)
Personal Identity Verification (PIV) of Operational Security Doctrine for the National Security Systems Compromising Emanations DoD INFOCON System Procedures
Information Assurance (IA) Education, National IA Training Standard for Federal Employees and Contractors FORTEZZA User PCMCIA Card Rest on Portable Computing Devices
Training, and Awareness Senior Systems Managers SI 507-01
DoDI 8410.02 SI 504-04
NSTISSI-4003 DoDD C-5200.19 NetOps for the Global Information Grid NetOps Community of Interest (NCOI)
CNSSI-4013 CNSSI-4014 NSTISSI-4001 Reporting and Evaluating COMSEC Control of Compromising Emanations Readiness Reporting
National IA Training Standard For Controlled Cryptographic Items (GIG) Charter
National IA Training Standard For Incidents
System Administrators (SA) Information Systems Security Officers
DoDD 3020.26 SI 701-01
NSTISSI-4005 Color Key - OPRs Defense Acquisition Guidebook Department of Defense Continuity STRATCOM CONPLAN 8039-08
CNSSI-4016 DoDD 8570.01 NSTISSI-4010 Section 7.5 Information Assurance NetOps Reporting
Safeguarding COMSEC Facilities and Keying Material Management Programs
National IA Training Standard For Risk IA Training, Certification, and Materials ASD(NII)/ASD(C3I)
Analysts Workforce Management
/DOD CIO NSA IA Directorate (IAD) Management
CNSSP-3 CNSSP-10, Nat’l Policy Governing Use DoDD 3020.44 Directive MD-10
DoD 8570.01-M DTM-09-026 Defense Crisis Management STRATCOM OPLANs
National Policy for Granting Access to of Approved Security Containers in Info CNSS/NSTISS Cryptographic Key Protection
Information Assurance Workforce Responsible and Effective Use of Classified Cryptographic Information Sys Security Apps
Improvement Program Internet-based Capabilities DISA
CNSSP-16 DoDD 1000.25
National Policy for the Destruction of DoD Personnel Identity Protection DNI SUBORDINATE POLICY
1.4 Partner for Strength COMSEC Paper Material (PIP) Program
ABOUT THIS CHART
JCS Component-level Policy
SP 800-37 R1 SP 800-53 R3 DoDI 8520.02 ASD(NII)/DoD CIO Memo (Directives, Instructions, Publications, DISA FSO Whitepapers
Guide for Applying the Risk Mgmnt Recommended Security Controls for Public Key Infrastructure (PKI) and Approval of External Public Key NIAP Memoranda)
Infrastructures This chart organizes information assurance policies and guidance by CIIA Strategic Goal
Framework to Fed. Info. Sys’s Federal Information Systems Public Key (PK) Enabling
NIST and Office of Primary Responsibility (see Color Key). It is intended to show all IA or IA-
NSTISSI-1000 NSA/CSS Policy 3-9 Security Readiness Review Scripts
SP 800-53A DoD Strategic Plan for Identity related policies a Component may need to comply with and direct users to the full text. Security Checklists (SRRs)
Guide for Assessing the Security National Information Assurance C&A Crypto Modernization Initiative Req’s NSA
Management No priority is intended by the arrangement of the guidance boxes.
Controls in Fed. Info. Systems Process (NIACAP) for Type 1 Classified Products
OSD In the electronic version, each policy is hyperlinked to its full text online. To use the Security Technical Implementation Security Configuration Guidelines
CNSSI-1253 CNSSI-4007
Security Categorization and Control Communications Security (COMSEC) STRATCOM hyperlink, simply click on the box. Guides (STIGs) (SCGs)
Selection for Nat’l Security Systems Utility Program
2.3 Assure Information Sharing
Policies in italics indicate the document is marked for limited distribution or no public-facing
USD(AT&L)
CNSSI-4008 CNSSP-14 DoDD 8320.02 United States Intelligence Community
hyperlink is currently available.
Program for the Mgt and Use of Nat’l National Policy Governing the Release Data-Sharing in a Net-Centric Information Sharing Strategy USD(C) Boxes with red borders were updated since 1 April 2010.
Reserve IA Security Equipment of IA Products/Services… Department of Defense
USD(I)
For printing, this chart is best viewed on 22"x17" (Size C) paper.
DoDI 5205.13 ICD 503 ASD(NII)/DoD CIO Memo DTM-08-027
Use of Peer-to-Peer File Sharing Security of Unclassified DoD
For the latest version of this chart go to http://iac.dtic.mil/iatac/ia_policychart.html.
Defense Industrial Base Cyber IT Systems Security Risk Management
and C&A Applications Across DoD USD(P)
Security / IA Activities Information on Non-DoD Info Systems
USD(P&R)
DoD Information Sharing Strategy Cross Domain Community Roadmap
Other Agencies
CJCSI 6211.02C Recently updated box
Defense Information System Network:
CJCSM 3213.02
Joint Staff Focal Point Distribution Statement A: Approved for Public
Policy and Responsibilities
Release. Distribution is unlimited.
Anda mungkin juga menyukai
- Shoe Dog: A Memoir by the Creator of NikeDari EverandShoe Dog: A Memoir by the Creator of NikePenilaian: 4.5 dari 5 bintang4.5/5 (537)
- Asus X553MA Repair Guide Rev2.0Dokumen7 halamanAsus X553MA Repair Guide Rev2.0UMA AKANDU UCHEBelum ada peringkat
- Grit: The Power of Passion and PerseveranceDari EverandGrit: The Power of Passion and PerseverancePenilaian: 4 dari 5 bintang4/5 (587)
- The Secret Language of AttractionDokumen278 halamanThe Secret Language of Attractionsandrojairdhonre89% (93)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceDari EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RacePenilaian: 4 dari 5 bintang4/5 (894)
- Canterburytales-No Fear PrologueDokumen10 halamanCanterburytales-No Fear Prologueapi-261452312Belum ada peringkat
- The Yellow House: A Memoir (2019 National Book Award Winner)Dari EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Penilaian: 4 dari 5 bintang4/5 (98)
- Canna DispensariesDokumen35 halamanCanna DispensariesWaf Etano100% (1)
- The Little Book of Hygge: Danish Secrets to Happy LivingDari EverandThe Little Book of Hygge: Danish Secrets to Happy LivingPenilaian: 3.5 dari 5 bintang3.5/5 (399)
- Degree and Order of ODEDokumen7 halamanDegree and Order of ODEadiba adibBelum ada peringkat
- On Fire: The (Burning) Case for a Green New DealDari EverandOn Fire: The (Burning) Case for a Green New DealPenilaian: 4 dari 5 bintang4/5 (73)
- Rock Laboratory PricelistDokumen1 halamanRock Laboratory PricelistHerbakti Dimas PerdanaBelum ada peringkat
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeDari EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifePenilaian: 4 dari 5 bintang4/5 (5794)
- WBC Study Reveals God's NatureDokumen11 halamanWBC Study Reveals God's NatureSherwin Castillo DelgadoBelum ada peringkat
- Never Split the Difference: Negotiating As If Your Life Depended On ItDari EverandNever Split the Difference: Negotiating As If Your Life Depended On ItPenilaian: 4.5 dari 5 bintang4.5/5 (838)
- OTGNNDokumen13 halamanOTGNNAnh Vuong TuanBelum ada peringkat
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureDari EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FuturePenilaian: 4.5 dari 5 bintang4.5/5 (474)
- Acid content in fruitsDokumen2 halamanAcid content in fruitsbone fire100% (1)
- Chams 1Dokumen78 halamanChams 1Das RavindraBelum ada peringkat
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryDari EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryPenilaian: 3.5 dari 5 bintang3.5/5 (231)
- 740 (Q50, V40, Awa 4Dokumen10 halaman740 (Q50, V40, Awa 4rawat2583Belum ada peringkat
- Transport in Plants: Test Yourself 9.1 (Page 178)Dokumen3 halamanTransport in Plants: Test Yourself 9.1 (Page 178)lee100% (3)
- The Emperor of All Maladies: A Biography of CancerDari EverandThe Emperor of All Maladies: A Biography of CancerPenilaian: 4.5 dari 5 bintang4.5/5 (271)
- Department of Education Doña Asuncion Lee Integrated School: Division of Mabalacat CityDokumen2 halamanDepartment of Education Doña Asuncion Lee Integrated School: Division of Mabalacat CityRica Tano50% (2)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreDari EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You ArePenilaian: 4 dari 5 bintang4/5 (1090)
- Salford Care Organisation Job Description & Person SpecificationDokumen14 halamanSalford Care Organisation Job Description & Person SpecificationAyesha EhsanBelum ada peringkat
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyDari EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyPenilaian: 3.5 dari 5 bintang3.5/5 (2219)
- Complimentary JournalDokumen58 halamanComplimentary JournalMcKey ZoeBelum ada peringkat
- Team of Rivals: The Political Genius of Abraham LincolnDari EverandTeam of Rivals: The Political Genius of Abraham LincolnPenilaian: 4.5 dari 5 bintang4.5/5 (234)
- Axel LeijonhufvudDokumen7 halamanAxel LeijonhufvudDario CoceresBelum ada peringkat
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersDari EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersPenilaian: 4.5 dari 5 bintang4.5/5 (344)
- Gantt Chart Engr110 - Gantt Chart Template 3Dokumen1 halamanGantt Chart Engr110 - Gantt Chart Template 3api-375485735Belum ada peringkat
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaDari EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaPenilaian: 4.5 dari 5 bintang4.5/5 (265)
- Rethinking Classification and Localization For Object DetectionDokumen13 halamanRethinking Classification and Localization For Object DetectionShah Nawaz KhanBelum ada peringkat
- PE and Health 12 - Module 7Dokumen19 halamanPE and Health 12 - Module 7Stephen Lorenzo A. DoriaBelum ada peringkat
- Silicone Bonding BrochureDokumen4 halamanSilicone Bonding BrochureAmir ShahzadBelum ada peringkat
- Rise of ISIS: A Threat We Can't IgnoreDari EverandRise of ISIS: A Threat We Can't IgnorePenilaian: 3.5 dari 5 bintang3.5/5 (137)
- AD 251 - Equivalent Uniform Moment Factor, M (Italic)Dokumen1 halamanAD 251 - Equivalent Uniform Moment Factor, M (Italic)symon ellimacBelum ada peringkat
- CE ProblemDokumen5 halamanCE ProblemJho FBelum ada peringkat
- Socio-cultural influences on educationDokumen4 halamanSocio-cultural influences on educationofelia acostaBelum ada peringkat
- The Unwinding: An Inner History of the New AmericaDari EverandThe Unwinding: An Inner History of the New AmericaPenilaian: 4 dari 5 bintang4/5 (45)
- TOS 22402 Winter 19th I SCHEME Paper Model Answer PaperDokumen25 halamanTOS 22402 Winter 19th I SCHEME Paper Model Answer Paperirshadmirza753Belum ada peringkat
- ComputerDokumen26 halamanComputer29.Kritika SinghBelum ada peringkat
- Moment Influence Line LabsheetDokumen12 halamanMoment Influence Line LabsheetZAXBelum ada peringkat
- The Clàsh The 0nly Band That MatteredDokumen255 halamanThe Clàsh The 0nly Band That MatteredNikos VaxevanidisBelum ada peringkat
- Writing A Formal Letter To The PresidentDokumen1 halamanWriting A Formal Letter To The PresidentPiaAnaisBelum ada peringkat
- Math-149 MatricesDokumen26 halamanMath-149 MatricesKurl Vincent GamboaBelum ada peringkat
- Statement Bank MBBDokumen11 halamanStatement Bank MBBminyak bidara01Belum ada peringkat
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)Dari EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Penilaian: 4.5 dari 5 bintang4.5/5 (119)
- Her Body and Other Parties: StoriesDari EverandHer Body and Other Parties: StoriesPenilaian: 4 dari 5 bintang4/5 (821)