Wi-Fi (Wireless Fidelity) Definition of Terms: IEEE 802.11b
Diunggah oleh
anon_86683981Judul Asli
Hak Cipta
Format Tersedia
Bagikan dokumen Ini
Apakah menurut Anda dokumen ini bermanfaat?
Apakah konten ini tidak pantas?
Laporkan Dokumen IniHak Cipta:
Format Tersedia
Wi-Fi (Wireless Fidelity) Definition of Terms: IEEE 802.11b
Diunggah oleh
anon_86683981Hak Cipta:
Format Tersedia
Wi-Fi (Wireless Fidelity)
Definition of Terms
AP Access Point
Encryption is the most effective way to achieve
data security.
Ethernet is a family of computer networking
technologies commonly used in local area
networks
GHz Gigahertz
Internet - the global system of
interconnected computer networks that use
the Internet protocol suite (TCP/IP) to link billions
of devices worldwide.
IEEE Institute of Electrical and Electronics
Engineers
LAN Local Area Network
Mbps short for megabits per second, a measure
of data transfer speed (a megabit is equal to one
million bits).
MHZ megahertz
Mobile Device a portable computing device such
as a smartphone or tablet computer.
Modem Short for modulator-demodulator. A
modem is a device or program that enables
a computer to transmit data over, for example,
telephone or cable lines.
Radio Waves an electromagnetic wave of a
frequency between about 104 and 1011 or 1012 Hz,
as used for long-distance communication.
Router a networking device
that forwards data packets between computer
networks.
Security is the degree of resistance to, or
protection from harm.
SSID Service Set Identifier
WEP Wired Equivalent Privacy
Wi-Fi Wireless Fidelity
TCP- Transmission Control Protocol
IP Internet Protocol
Wireless Technology which is commonly used,
for connecting devices in wireless mode.
WLAN Wireless Local Area Network
WPA Wireless Protected Access
Wi-Fi
Wireless Fidelity
name of a popular wireless networking technology that uses
radio waves to provide wireless high-speed Internet and
network connections
Wi-Fi is simply a trademarked phrase that means IEEE
802.11x.
History
Wi-Fi technology builds on IEEE 802.11 standards.
The IEEE develops and publishes these
standards, but does not test equipment for
compliance with them.
The non-profit Wi-Fi Alliance formed in 1999 to fill
this void.
As of 2009 the Wi-Fi Alliance consisted of more
than 300 companies from around the world.
The term Wi-Fi suggests Wireless Fidelity, resembling the
long-established audio-equipment classification term high
fidelity (in use since the 1930s ) or Hi-Fi (used since 1950).
The yin-yang logo indicates the certification of a product
for interoperability.
There are three versions of Wi-Fi radios currently
available- the ones that work with:
IEEE 802.11b
Appeared in late 1999
Operates at 2.4GHz radio spectrum
11 Mbps (theoretical Speed) Within 30
m Range
4-6 Mbps (actual speed)
100-150 feet range
Most Popular, Less Expensive
Interference from Mobile phones and
Bluetooth devices which can reduce the
transmission speed
IEEE 802.11a
Introduced in 2001
Operates at 5 GHz (less popular)
54 Mbps (theoretical speed)
15-20 Mbps (actual speed)
50-75 feet range
More Expensive
Not Compatible with 802.11b
IEEE 802.11g
Introduced in 2003
Combine the Feature of both
Standards(a,b)
100-150 feet range
54 Mbps
2.4 GHz radio frequencies
Compatible with b
Hotspot
hotspot is used to define an area where Wi-Fi
access is available.
It can either be through a closed wireless network
at home or in public places such as restaurants or
airports.
Pocket Wifi
Pocket Wi-Fi router is a battery power mobile
router which enables Wi-Fi-enabled devices to
connect to the internet via the mobile network.
Wi-Fi and its Uses
Share your internet
Share resources between PCs
Print & scan
Remote control of your entertainment system
Stream video
Play online games
Monitor your home
Wi-Fi Advantages
No Wires Needed
Convenience
Mobility
Productivity
Deployment
Expandability
Cost
Wi-Fi Disadvantages
Security
Range
Reliability
Speed
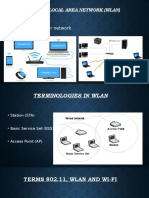
Elements of Wi-Fi Network
Access Point (AP)
The AP is a wireless LAN transceiver or base station that
can connect one or many wireless devices simultaneously to
the Internet.
Wi-Fi cards
They accept the wireless signal and relay information. They
can be internal and external.(e.g PCMCIA Card for Laptop
and PCI Card for Desktop PC)
Safeguards
Firewalls and anti-virus software protect networks from
uninvited users and keep information secure.
How Does Wi-Fi Works?
Basic concept is same as walkie talkies.
A Wi-Fi hotspot can be created by installing an
accept point to an internet connection.
An accept point acts as base station.
When Wi-Fi enabled device encounters a hotspot
the device can they connect to that network
wirelessly.
A single access point can support up to30 users
and can function with in a range of 100-150 ft.
indoor and 300 ft. outdoors.
How to Connect to Wi-Fi
Step 1: Locate yourself in a property or public
space that has a wireless router. I.e. Somewhere
where a Wi-Fi signal is being transmitted.
Step 2: Make sure that the device you're going to
use is a.) Capable of connecting to the internet
and b.) Capable of connecting to Wi-Fi.
Step 3: Find out the name of the Wi-Fi network
that the router in your location is transmitting.
Step 4: Once you know the name of the Wi-Fi
network, use your chosen device to find it
navigate to Wi-Fi settings > turn Wi-Fi on > click
on the name of your Wi-Fi network > click
"connect".
Step 5: Many Wi-Fi networks are made private,
with access restricted via a password. If your
chosen Wi-Fi network is password protected, at
this point it will ask you enter that password.
Wi-Fi Security Threats
Wireless technology doesnt remove any old
security issues, but introduces new ones
Eavesdropping
Man-in-the-middle attacks
Denial of Service
Wi-Fi Security
The Requirements Of Wi-Fi network security can be
broken down into two primary components:
Authentication
User and Server Authentication
Privacy
Authentication
Keeping unauthorized users off the network
User Authentication Server is Used
Username and password
Risk:
Data{username and password} send before
secure channel established
Phone to passive eavesdropping by attacker
Solution
Establishing a encrypted channel before sending
username and password
Wi-Fi Security
Service Set Identifier (SSID)
used to identify an 802.11 network
It can be pre-configured or advertised in beacon
broadcast
It is transmitted in clear text
provide very little security
Wired Equivalency Protocol (WEP)
Basic encryption technology.
Uses an RC4 stream cipher.
Two versions: 64-bit and 128-bit
versions.
Built into Wi-Fi certified equipment.
Implemented at the MAC level.
Protects radio signal between device and access
point.
Does not protect data beyond the
access point.
Uses static encryption keys.
Easy to crack.
Still better then nothing.
Wi-Fi Protected Access (WPA)
Designed to replace WEP.
Firmware update.
128-bit Temporal Key Integrity Protocol
(TKIP) encryption.
Uses a master key that is
regularly changed.
User authentication.
Data Integrity.
Protects radio signal between device and access
point.
Built into Wi-Fi certified equipment.
Implemented at the MAC level.
Available in two versions:
WPA2 Personal.
WPA2 Enterprise.
Wi-Fi Protected Access 2 (WPA2)
Designed to replace WEP.
128-bit Advanced Encryption Standard
(AES).
Based on the IEEE 802.11i standard.
Provides government level security.
Wi-Fi and Ethernet
Speed
Wi-Fi offered maximum theoretical speeds of
54Mbps (megabits per second), and far less in
practice.
Ethernet, which can produce speeds anywhere
from 100Mbps to 1000Mbps and beyond.
Reliability
A fixed Ethernet connection is likely to be fast,
stable and deliver consistent speeds.
Wi-Fi is susceptible to countless environmental
factors. Radio waves can be blocked by walls and
floors.
Security
theres really no comparison.
The data on an Ethernet network can only be
accessed by devices physically attached to the
network.
With Wi-Fi, the data is in the air. Most Wi-Fi
networks are secured, so your data is encrypted.
But the strength of the encryption depends on the
security method you are using.
Wi-Fi Problems and Solution
1. I cannot connect to my router. How do I resolve
this?
This is a wide-open problem with an almost limitless
range of causes and solutions, but here are several
actions that might do the trick. First, make sure your
router is configured for Dynamic Host Configuration
Protocol (DHCP). If it is, try disabling and re-enabling the
DHCP function. If that doesn't work, disable wireless
security and see if you get a connection; sometimes a
mismatched Wired Equivalent Privacy (WEP) key can drop
the IP address. You should also check for electrical
interference from competing devices such as cordless
phones, baby monitors, alarm systems, and microwave
ovens. Disable all suspect devices, then recheck your WiFi connection. If all else fails, reboot the router and all
computers on your network.
2. What steps should I take to secure my Wi-Fi
network?
Routers typically offer at least two common forms of
security: WEP, and Wi-Fi Protected Access (WPA)
encryption. Both are easy to enable, although you'll get
maximum protection from WPA. To activate security, go to
your router's browser-based administration tool (the
default address for most routers is http://192.168.0.1 or
http://192.168.1.1) and look for the wireless-security
area. WPA requires you to enter a simple security phrase
(eight to 63 characters), or, with some routers, a more
secure (but much harder to remember) 64-digit key.
Similarly, WEP demands that you choose from 64-bit or
128-bit encryption, and enter an alphanumeric hex
phrase, with some routers giving you the option to enter
a simpler ASCII phrase. In addition to enabling wireless
security, you can also disable the broadcasting of the
Service Set Identifier (SSID, or network name). Doing so
can make the network more difficult for hackers to see.
Also available in two versions:
WPA2 Personal.
WPA2 Enterprise.
Also, make sure to enable the router's hardware firewall
(more on that later), and change the router's default
password. And do not enable file sharing, unless you
really use it. This will safeguard your personal files from
interlopers.
3. How do I automatically connect to a Wi-Fi
network without having to manually connect the
first time?
If you just want to connect fast to any available network,
you can set your notebook to do so automatically. Go to
Control Panel > Network Connections and right-click your
current wireless network. Then click Properties > Wireless
Networks > Advanced. Make sure the radio button next to
"Any available network (access point preferred)" is on,
then check the box "Automatically connect to nonpreferred networks."
4. Should I allow other people to access my Wi-Fi service?
What are the dangers?
Some users see no harm in sharing the Wi-Fi love, giving
neighbors and even total strangers free access to the
Internet. Others maintain that piggybacking can open
their networks to potential danger. The decision is yours,
but if you choose not to encrypt, make sure to disable file
sharing. Assuming you have your hardware firewall
turned on, the worst that probably will happen is that
your throughput will drop if your piggybacking neighbors
crank up BitTorrent every evening. If you want to
determine whether others are using your unsecured
network, most routers have a page that lists all the
wireless clients currently connected.
Most people, however, are not comfortable with the idea
of allowing just anyone to use their wireless service. In
theory, the practice can make your network vulnerable to
hackers, since anyone who uses your wireless signal is on
your home network. Malevolent users, for instance, could
release nasty viruses or hijack your PC. That's not terribly
likely, but you should avoid the possibility by using WPA
to protect yourself and keep others off your network.
5. You have a dead spot in your home that your
802.11g router can't seem to reliably reach.
Solution: If you're not already using an 802.11n router
and adapter, it might be time for the switch. (True, the
standard hasn't been finally approved yet, but best guess
is that the hardware is locked down and any changes that
are needed will be done to firmware --which you can
upgrade.)
Why "n?" Because it uses a technology called MIMO
(Multiple Input Multiple Output) that allows it to broadcast
and receive multiple signals.
When a data stream arrives at your dead spot, it's often
been bounced off of too many walls, floors, and other
obstructions to make much sense to your 802.11g or
802.11b router. A MIMO-enabled router takes all those
bounced reflections and compares them, looking to fill in
the blanks until it's pieced together as much of the signal
-- if not all of it -- as possible. It's more than likely that the
drop-outs you've experienced with your 802.11b/g router
and adapter will be cured and you might actually see
some honest Wi-Fi speed emerge.
No Internet Connection
6. You just moved your router and modem to a new
location and now Windows says you have a local
connection but no access to the Internet.
Solution: Reorganizing your network topology to make
best use of your wired and wireless connections is always
a good thing, but changing something that's working can
often lead to unintended consequences. Assuming that
everything is plugged in as before, your router may not
be at fault. If you have a local connection (and you've
tried it to be sure) but no Internet connection, it could be
your modem. Some modems have parental control
buttons that, once pressed, lock out your internet
connection. They're not always in the best locations.
Anda mungkin juga menyukai
- Wifi A-31Dokumen40 halamanWifi A-31Amrit SianBelum ada peringkat
- Seminar On: Wi-Fi TechnologyDokumen23 halamanSeminar On: Wi-Fi TechnologyRitika VermaBelum ada peringkat
- Jaipur Engineering College, Kukas: Submitted To: Submitted byDokumen26 halamanJaipur Engineering College, Kukas: Submitted To: Submitted byRahul AgarwalBelum ada peringkat
- Wi-Fi Technology & Its Security: By: Sandeep Kr. Gangwar EC-09Dokumen30 halamanWi-Fi Technology & Its Security: By: Sandeep Kr. Gangwar EC-09Arpit AgarwalBelum ada peringkat
- Wireless FidelityDokumen28 halamanWireless FidelityZaid Mahmood100% (2)
- Wifi Technology: by Nikhila Ann Varghese Malla Reddy Engineering CollegeDokumen29 halamanWifi Technology: by Nikhila Ann Varghese Malla Reddy Engineering CollegeNeeha KuttyBelum ada peringkat
- WifiDokumen24 halamanWifichinmayee222Belum ada peringkat
- WIFIDokumen8 halamanWIFIswathiBelum ada peringkat
- Wi-Fi Technology: Guided By: Jenela Prajapati Presented byDokumen27 halamanWi-Fi Technology: Guided By: Jenela Prajapati Presented byNikhilesh KhatraBelum ada peringkat
- Wifi Technology Ce 70Dokumen27 halamanWifi Technology Ce 70Abhishek PatelBelum ada peringkat
- Wi-Fi Technology: Submitted by Sagar Tak 3610332Dokumen15 halamanWi-Fi Technology: Submitted by Sagar Tak 3610332Saurabh SainiBelum ada peringkat
- WPAN & WLAN Part 2Dokumen26 halamanWPAN & WLAN Part 2Erman HamidBelum ada peringkat
- WiFi Technology BssDokumen25 halamanWiFi Technology BssTanmay Karan100% (1)
- Wi Fi 130331083514 Phpapp02Dokumen32 halamanWi Fi 130331083514 Phpapp02Mohammed ElmadaniBelum ada peringkat
- 21-1 (Kulangpa)Dokumen29 halaman21-1 (Kulangpa)jhade_cabatoBelum ada peringkat
- WiFi TechnologyDokumen35 halamanWiFi TechnologySmitesh MukaneBelum ada peringkat
- Connecting People 1.abstract:: Wi-Fi TechnologyDokumen9 halamanConnecting People 1.abstract:: Wi-Fi TechnologySanthosh SalemBelum ada peringkat
- Wifi MoniDokumen32 halamanWifi MoniSunil BerwalBelum ada peringkat
- Wlan & WifiDokumen59 halamanWlan & WifiCelestian Paul PepitoBelum ada peringkat
- TCIL 10 WiFi TechnologyDokumen42 halamanTCIL 10 WiFi TechnologyShivali SainiBelum ada peringkat
- WiFi TechnologyDokumen22 halamanWiFi Technologyvishnu0751Belum ada peringkat
- Wi-Fi 802.11 Standard SecurityDokumen22 halamanWi-Fi 802.11 Standard SecurityAdrianBelum ada peringkat
- Wi-Fi Technology: Presentation OnDokumen21 halamanWi-Fi Technology: Presentation OnДоржоо Э.Belum ada peringkat
- Wi FiDokumen27 halamanWi FiHarish KumarBelum ada peringkat
- TCIL 10 WiFi TechnologyDokumen42 halamanTCIL 10 WiFi TechnologyRam VBITBelum ada peringkat
- Wi-Fi 802.11 Standard SecurityDokumen22 halamanWi-Fi 802.11 Standard SecurityAbdul HameedBelum ada peringkat
- WifiDokumen13 halamanWifi'Mohnish Anand'Belum ada peringkat
- Wireless TechnologiesDokumen45 halamanWireless TechnologiesKenneth O'BrienBelum ada peringkat
- Unit IVDokumen54 halamanUnit IVChetan SaiBelum ada peringkat
- Introduction To Wifi by Tarique AkhtarDokumen23 halamanIntroduction To Wifi by Tarique AkhtarMegha PodderBelum ada peringkat
- Chapter 1-5-NE 5eDokumen34 halamanChapter 1-5-NE 5eJames JohfBelum ada peringkat
- Wireless Fidelity: Technology and ApplicationsDokumen22 halamanWireless Fidelity: Technology and ApplicationsPurboday GhoshBelum ada peringkat
- Wireless CommunicationDokumen9 halamanWireless CommunicationViJay KuMarBelum ada peringkat
- Raj The KingDokumen51 halamanRaj The KingShiva Kumar KBelum ada peringkat
- Presentation Wifi 1464365861 211837Dokumen20 halamanPresentation Wifi 1464365861 211837Selwsc BhiwaniBelum ada peringkat
- Wireless Local Area Network (Wlan)Dokumen55 halamanWireless Local Area Network (Wlan)saadansariBelum ada peringkat
- Wifi 1Dokumen24 halamanWifi 1Nandan DamaniaBelum ada peringkat
- Computer Networking Image Gallery: Inside This ArticleDokumen6 halamanComputer Networking Image Gallery: Inside This ArticleYogesh GiriBelum ada peringkat
- Parwez WifiDokumen26 halamanParwez WifiSaahil MuhammadBelum ada peringkat
- WiFi, Working, Elements of WiFiDokumen67 halamanWiFi, Working, Elements of WiFiZohaib Jahan100% (1)
- WifiDokumen40 halamanWifiabhay_83Belum ada peringkat
- Wi-Fi Technology: By: Pranav Mandora Rikin Mistry Ldrp-EcDokumen26 halamanWi-Fi Technology: By: Pranav Mandora Rikin Mistry Ldrp-EcPranav MandoraBelum ada peringkat
- What Is WiFiDokumen14 halamanWhat Is WiFipappu507Belum ada peringkat
- AssignmentDokumen15 halamanAssignmentNikhil MoudgilBelum ada peringkat
- Introduction To How WiFi WorksDokumen4 halamanIntroduction To How WiFi WorksDeepak SinhaBelum ada peringkat
- WifiDokumen26 halamanWifiR.SwethaBelum ada peringkat
- What Is Wifi and How Does It Work 298 O1yu7tDokumen2 halamanWhat Is Wifi and How Does It Work 298 O1yu7tAntoneyGeorgeBelum ada peringkat
- Wifi Technology PresentationDokumen22 halamanWifi Technology PresentationDimple Verma100% (1)
- Wireless Fidelity: Technology and ApplicationsDokumen22 halamanWireless Fidelity: Technology and ApplicationsPurboday GhoshBelum ada peringkat
- Wi-Fi Security: Prepaired By: Virendra Singh Thakur GTU PG School, AhmeadabadDokumen20 halamanWi-Fi Security: Prepaired By: Virendra Singh Thakur GTU PG School, Ahmeadabadveeru3112Belum ada peringkat
- Deepika WifiDokumen9 halamanDeepika WifiAnubhuti JalanBelum ada peringkat
- Wi-Fi Technology: B y N.Nirmal Kumar P.SudheerDokumen14 halamanWi-Fi Technology: B y N.Nirmal Kumar P.SudheerZeeshan AliBelum ada peringkat
- Wifi SeminarDokumen10 halamanWifi SeminarAmandeep AmanBelum ada peringkat
- Wi-Fi TechnologyDokumen14 halamanWi-Fi TechnologyYashith DissanayakeBelum ada peringkat
- Shawon WifiDokumen10 halamanShawon WifiFoez LeonBelum ada peringkat
- An Introduction To Wireless Network and Wireless FidelityDokumen39 halamanAn Introduction To Wireless Network and Wireless FidelityPale KhanBelum ada peringkat
- Cisco Network Administration Interview Questions: CISCO CCNA Certification ReviewDari EverandCisco Network Administration Interview Questions: CISCO CCNA Certification ReviewPenilaian: 4.5 dari 5 bintang4.5/5 (6)
- BDSM Library - After The Garden PartyDokumen5 halamanBDSM Library - After The Garden PartyManu ShankarBelum ada peringkat
- Insulation Considered Is LRB 120 Kg/M3 Density, 100mm Thk. Suitable For 24SWG Aluminium SheetDokumen1 halamanInsulation Considered Is LRB 120 Kg/M3 Density, 100mm Thk. Suitable For 24SWG Aluminium SheetPriya TanejaBelum ada peringkat
- Orchestral Technique: A Manual For Students: Gordon JacobDokumen1 halamanOrchestral Technique: A Manual For Students: Gordon JacobDeepan AkashBelum ada peringkat
- Undaunted Solo Rules v5Dokumen10 halamanUndaunted Solo Rules v5re-peteBelum ada peringkat
- MB Manual Ga-G41mt-S2pt e PDFDokumen40 halamanMB Manual Ga-G41mt-S2pt e PDFLeonel AtaramaBelum ada peringkat
- AlteonDokumen13 halamanAlteonChuck CheungBelum ada peringkat
- Amanpulo FactsheetDokumen6 halamanAmanpulo FactsheetAlexBelum ada peringkat
- Breath of Fire II (SNES) - Prima Authorized Game SecretsDokumen227 halamanBreath of Fire II (SNES) - Prima Authorized Game Secretsspadira100% (2)
- Enrique IglesiasDokumen25 halamanEnrique IglesiasNagham Bazzi0% (1)
- Complex SentencesDokumen3 halamanComplex SentencesPilar Romero CandauBelum ada peringkat
- ASSASSIN'S CREED UNITY 100% Complete Save Game PCDokumen10 halamanASSASSIN'S CREED UNITY 100% Complete Save Game PCunitysavegame0% (6)
- 19504635547018266Dokumen77 halaman19504635547018266Kuushal SodhiBelum ada peringkat
- Freezer Bag Recipes PDFDokumen38 halamanFreezer Bag Recipes PDFchieflittlehorse100% (1)
- Kbeatbox KSNet450 User GuideDokumen12 halamanKbeatbox KSNet450 User GuideRin DragonBelum ada peringkat
- CIE IGCSE FLE PAST PAPER 0500 - w03 - QP - 2Dokumen8 halamanCIE IGCSE FLE PAST PAPER 0500 - w03 - QP - 2mwah5iveBelum ada peringkat
- 5 Yrs 5 Yrs 1 Yr 5 Yrs 1 Yr 1 Yr 1 Yrs 5 Yrs 1 Yr 5 Yrs 1 Yr 5 YrsDokumen2 halaman5 Yrs 5 Yrs 1 Yr 5 Yrs 1 Yr 1 Yr 1 Yrs 5 Yrs 1 Yr 5 Yrs 1 Yr 5 YrsMuhamad YusreyBelum ada peringkat
- ALDI Growth Announcment FINAL 2.8Dokumen2 halamanALDI Growth Announcment FINAL 2.8Shengulovski IvanBelum ada peringkat
- Brief History of Jazz History EssayDokumen9 halamanBrief History of Jazz History EssayMoses WenBelum ada peringkat
- Product: Spotify Category: Live StreamingDokumen4 halamanProduct: Spotify Category: Live StreamingKeerthana AravindBelum ada peringkat
- Warner Records IncDokumen5 halamanWarner Records IncMi PhanBelum ada peringkat
- Grade 5 PPT - English - Q1 - W2 - Day 1-5Dokumen83 halamanGrade 5 PPT - English - Q1 - W2 - Day 1-5Melanie Niña CullarBelum ada peringkat
- 21 Defensive IdDokumen29 halaman21 Defensive IdJay Green100% (1)
- xlr8 Carb CyclingDokumen67 halamanxlr8 Carb CyclingH DrottsBelum ada peringkat
- User Manual Titan MuxDokumen81 halamanUser Manual Titan Muxak1828100% (1)
- Identity TheotherDokumen4 halamanIdentity Theotherapi-282750167Belum ada peringkat
- Reviewer For Business MarketingDokumen5 halamanReviewer For Business MarketingEira AvyannaBelum ada peringkat
- SE125 ClassDokumen125 halamanSE125 ClassdanialsafianBelum ada peringkat
- RRR Rabbit Care Info 2021Dokumen7 halamanRRR Rabbit Care Info 2021api-534158176Belum ada peringkat
- Chapter 5Dokumen28 halamanChapter 5Nada ElDeebBelum ada peringkat
- WOL-3 - Dragons of SpringDokumen341 halamanWOL-3 - Dragons of SpringRyan Hall100% (15)