Assignment 3
Diunggah oleh
muse0 penilaian0% menganggap dokumen ini bermanfaat (0 suara)
89 tayangan1 halamanmuse
Hak Cipta
© © All Rights Reserved
Format Tersedia
PDF, TXT atau baca online dari Scribd
Bagikan dokumen Ini
Apakah menurut Anda dokumen ini bermanfaat?
Apakah konten ini tidak pantas?
Laporkan Dokumen Inimuse
Hak Cipta:
© All Rights Reserved
Format Tersedia
Unduh sebagai PDF, TXT atau baca online dari Scribd
0 penilaian0% menganggap dokumen ini bermanfaat (0 suara)
89 tayangan1 halamanAssignment 3
Diunggah oleh
musemuse
Hak Cipta:
© All Rights Reserved
Format Tersedia
Unduh sebagai PDF, TXT atau baca online dari Scribd
Anda di halaman 1dari 1
ADVANCED COMPUTER NETWORKS
Assignment 3: Data Link Layers
Assigned on: 29 March 2017
Due by: 04 April 2017 for Communication and Computer
Taken from: A S Tannenbaum "Computer Networks" Prentice Hall of India Publication, 2002.
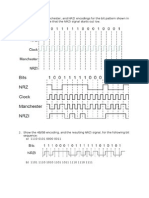
1. The following character encoding is used in a data link protocol:
A: 01000111 B: 11100011 FLAG: 01111110 ESC: 11100000
Show the bit sequence transmitted (in binary) for the four-character frame A B ESC
FLAG when each of the following framing methods is used:
(a) Byte count.
(b) Flag bytes with byte stuffing.
(c) Starting and ending flag bytes with bit stuffing.
2. The following data fragment occurs in the middle of a data stream for which the byte
stuffing algorithm described in the text is used: A B ESC C ESC FLAG FLAG D. What
is the output after stuffing?
3. What is the maximum overhead in byte-stuffing algorithm?
4. One of your classmates, Scrooge, has pointed out that it is wasteful to end each frame
with a flag byte and then begin the next one with a second flag byte. One flag byte could
do the job as well, and a byte saved is a byte earned. Do you agree?
5. A bit string, 0111101111101111110, needs to be transmitted at the data link layer.
What is the string actually transmitted after bit stuffing?
6. Sixteen-bit messages are transmitted using a Hamming code. How many check bits
are needed to ensure that the receiver can detect and correct single-bit errors? Show
the bit pattern transmitted for the message 1101001100110101. Assume that even parity
is used in the Hamming code.
7. Suppose that a message 1001 1100 1010 0011 is transmitted using Internet Checksum
(4-bit word). What is the value of the checksum?
8. What is the remainder obtained by dividing x 7 + x 5 + 1 by the generator polynomial
x 3 + 1?
9. A bit stream 10011101 is transmitted using the standard CRC method described in the
text. The generator polynomial is x 3 + 1. Show the actual bit string transmitted. Suppose
that the third bit from the left is inverted during transmission. Show that this
error is detected at the receiver’s end. Give an example of bit errors in the bit string
transmitted that will not be detected by the receiver.
Anda mungkin juga menyukai
- Lab 4 SolutionsDokumen2 halamanLab 4 Solutionsapi-251706325100% (2)
- CN NumericalsDokumen3 halamanCN Numericals22bce546Belum ada peringkat
- Assignment 2 Deadline: 17 JULY 2019Dokumen1 halamanAssignment 2 Deadline: 17 JULY 2019usmanBelum ada peringkat
- TUT5Dokumen2 halamanTUT5yogesh israniBelum ada peringkat
- Quiz 1 2019 IF3130 PDFDokumen1 halamanQuiz 1 2019 IF3130 PDFHamzah Chairil SalimBelum ada peringkat
- ICOM 5026-090: Computer Networks: Homework 3 Due On March 19, 2012Dokumen1 halamanICOM 5026-090: Computer Networks: Homework 3 Due On March 19, 2012edwinfgBelum ada peringkat
- CCN Assignment: Name:-Hermain Fayyaz KarimDokumen7 halamanCCN Assignment: Name:-Hermain Fayyaz KarimHermain Fayyaz KarimBelum ada peringkat
- CN Assignment 1Dokumen2 halamanCN Assignment 1KrishanuNayakBelum ada peringkat
- Data Link LayerDokumen33 halamanData Link Layerwinster21augBelum ada peringkat
- CN Unit IIIDokumen24 halamanCN Unit IIIsrikanthBelum ada peringkat
- Chapter 3 2022Dokumen127 halamanChapter 3 2022adityadas.657100% (1)
- MST Latest 2025Dokumen8 halamanMST Latest 2025bndianonymousBelum ada peringkat
- Data Communication and Computer Networks (Ece-4308) : Overview of Data Link LayerDokumen80 halamanData Communication and Computer Networks (Ece-4308) : Overview of Data Link LayerBezabh AbebawBelum ada peringkat
- UNIT2 NotesDokumen24 halamanUNIT2 NotesMunawar MohammedBelum ada peringkat
- University Malaysia Sarawak KNL 3333: Data and Computer Networking ProblemsDokumen1 halamanUniversity Malaysia Sarawak KNL 3333: Data and Computer Networking ProblemsZA IzatBelum ada peringkat
- CN Module IIDokumen28 halamanCN Module IImbucse a9Belum ada peringkat
- Data Link Layer: Net 221D: Computer Networks FundamentalsDokumen58 halamanData Link Layer: Net 221D: Computer Networks FundamentalsMARAM ABDULAZIZBelum ada peringkat
- Lecture 3Dokumen15 halamanLecture 3Khalid AbnodeBelum ada peringkat
- Error Detection CorrectionDokumen22 halamanError Detection CorrectionJagdish BhanushaliBelum ada peringkat
- DLLDokumen51 halamanDLLSohil SharmaBelum ada peringkat
- New Microsoft Word DocumentDokumen4 halamanNew Microsoft Word DocumentKhangBelum ada peringkat
- Week 5 Fundamentals of Network Communication PDFDokumen3 halamanWeek 5 Fundamentals of Network Communication PDFSyed Ashraf100% (1)
- Parity CheckDokumen41 halamanParity CheckAmit DhullBelum ada peringkat
- 08 Data Link LayerError ControlDokumen29 halaman08 Data Link LayerError Controlcodingstuff18Belum ada peringkat
- 7650547Dokumen2 halaman7650547saraalazazy343Belum ada peringkat
- Hw5 ReportDokumen4 halamanHw5 ReportMadhan ReddyBelum ada peringkat
- CN Assignment 1Dokumen1 halamanCN Assignment 1HacraloBelum ada peringkat
- Assignment 2Dokumen5 halamanAssignment 2Mudit JainBelum ada peringkat
- Tutorial Sheet 3 (Computer Networks)Dokumen2 halamanTutorial Sheet 3 (Computer Networks)Areej AhmadBelum ada peringkat
- Computer Network Module 2Dokumen160 halamanComputer Network Module 2shakti139Belum ada peringkat
- Scs2101-Class Assignment-N01521664rDokumen5 halamanScs2101-Class Assignment-N01521664rugwakBelum ada peringkat
- Data Link LayerDokumen121 halamanData Link Layermubin.pathan765Belum ada peringkat
- Error Control For Digital Satellite LinksDokumen57 halamanError Control For Digital Satellite LinksMajd KhaderBelum ada peringkat
- 08 Data Link LayerError ControlDokumen30 halaman08 Data Link LayerError Controlsaurabh singh gahlotBelum ada peringkat
- Lecture 10Dokumen40 halamanLecture 10Rohit AgrawalBelum ada peringkat
- Home Assignment1Dokumen1 halamanHome Assignment1JayanthkumarBelum ada peringkat
- Chapter 3 Data Link LayerDokumen104 halamanChapter 3 Data Link LayerArnav MohanBelum ada peringkat
- Class 3Dokumen25 halamanClass 3Prathik KharviBelum ada peringkat
- Data Link Layer 1Dokumen88 halamanData Link Layer 1PalashAhujaBelum ada peringkat
- Network ExerciseDokumen3 halamanNetwork ExerciseSundari MuthuBelum ada peringkat
- DC aDCghskjskksks FjsDokumen4 halamanDC aDCghskjskksks FjsSaiteja GundapuBelum ada peringkat
- B.sc. (CBCS) Semester III 2020Dokumen22 halamanB.sc. (CBCS) Semester III 2020Isha DalmiaBelum ada peringkat
- 2020-10-20SupplementaryCS307CS307-F - Ktu QbankDokumen3 halaman2020-10-20SupplementaryCS307CS307-F - Ktu QbankPragyanshree SwainBelum ada peringkat
- CAP256: Computer Networks: Unit-3: Data Link Layer - Error ControlDokumen29 halamanCAP256: Computer Networks: Unit-3: Data Link Layer - Error ControlYash jangidBelum ada peringkat
- Test+ +1Dokumen2 halamanTest+ +1Praneeth Kumar100% (1)
- Homework3 WrittenDokumen2 halamanHomework3 WrittenGaunish gargBelum ada peringkat
- Assignment # 4 Course: DCN Submission Date: 31st March 2020Dokumen2 halamanAssignment # 4 Course: DCN Submission Date: 31st March 2020Shahnaz ShakirBelum ada peringkat
- CEG3185 Winter 2021 Assignment 1: Due Date: 5pm On Monday, February 8, 2021 Problem 1Dokumen1 halamanCEG3185 Winter 2021 Assignment 1: Due Date: 5pm On Monday, February 8, 2021 Problem 1Ren3rBelum ada peringkat
- 17 EC 3085 Data Networks Protocols Test 1 KeyDokumen6 halaman17 EC 3085 Data Networks Protocols Test 1 KeyBonagiri PraneethBelum ada peringkat
- The Data Link LayerDokumen35 halamanThe Data Link Layernitu2012Belum ada peringkat
- 09 Data Link LayerError ControlDokumen29 halaman09 Data Link LayerError Controlanushka aroraBelum ada peringkat
- Physical Addressing - Error Handling PDFDokumen14 halamanPhysical Addressing - Error Handling PDFGopal AgarwalBelum ada peringkat
- CCNA Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesDari EverandCCNA Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesBelum ada peringkat
- Computer Network UNIT 2Dokumen30 halamanComputer Network UNIT 2Nihal GuptaBelum ada peringkat
- CHP 2Dokumen103 halamanCHP 2luze asdBelum ada peringkat
- F16examplestut2 Tut3 AnswersDokumen3 halamanF16examplestut2 Tut3 Answersdanh nguyenBelum ada peringkat
- Lecture 10: Error Control Coding IDokumen40 halamanLecture 10: Error Control Coding ICường NguyễnBelum ada peringkat
- Possible Question Summary From Previous Year QuestionDokumen12 halamanPossible Question Summary From Previous Year QuestionRISHI NITHIN.E.MBelum ada peringkat
- (Sem. Vi) Even Theory Examination 2012-13: PAPER ID: 2474Dokumen2 halaman(Sem. Vi) Even Theory Examination 2012-13: PAPER ID: 2474123vidyaBelum ada peringkat
- Error-Correction on Non-Standard Communication ChannelsDari EverandError-Correction on Non-Standard Communication ChannelsBelum ada peringkat
- Advanced Computer Networks: Assignment 1: Fundamentals and Principles of Computer NetworkingDokumen1 halamanAdvanced Computer Networks: Assignment 1: Fundamentals and Principles of Computer NetworkingmuseBelum ada peringkat
- Eit-M Department of Civil EngineeringDokumen6 halamanEit-M Department of Civil EngineeringmuseBelum ada peringkat
- Final Report To Be Printed2Dokumen41 halamanFinal Report To Be Printed2museBelum ada peringkat
- Eit-M Department of Civil EngineeringDokumen6 halamanEit-M Department of Civil EngineeringmuseBelum ada peringkat
- Edited Girma RerserchDokumen27 halamanEdited Girma RerserchmuseBelum ada peringkat
- Araya GHHHDokumen63 halamanAraya GHHHmuseBelum ada peringkat
- Edited Girma RerserchDokumen27 halamanEdited Girma RerserchmuseBelum ada peringkat
- Design and Development of True Centrifugal Casting Machine: Prof. M. D. PatelDokumen34 halamanDesign and Development of True Centrifugal Casting Machine: Prof. M. D. Patelmuse100% (1)
- Technical & Vocational Education & Training Institute Institute of Technology Department of Manufacturing TechnologyDokumen26 halamanTechnical & Vocational Education & Training Institute Institute of Technology Department of Manufacturing TechnologymuseBelum ada peringkat
- The DescribtionDokumen1 halamanThe DescribtionmuseBelum ada peringkat
- Final RiportDokumen56 halamanFinal RiportmuseBelum ada peringkat
- The DescribtionDokumen1 halamanThe DescribtionmuseBelum ada peringkat
- ManualDokumen128 halamanManualmuseBelum ada peringkat
- 2.1 AntennaDokumen9 halaman2.1 AntennamuseBelum ada peringkat
- Emw Group Assinment: - Members - Id NoDokumen12 halamanEmw Group Assinment: - Members - Id NomuseBelum ada peringkat
- Eit-M: 1.title: Design, Simulation and Performance Analysis of Helix Array AntennaDokumen18 halamanEit-M: 1.title: Design, Simulation and Performance Analysis of Helix Array AntennamuseBelum ada peringkat
- Project Proposal On Design and Modelling and Development Of: Submission DateDokumen24 halamanProject Proposal On Design and Modelling and Development Of: Submission DatemuseBelum ada peringkat
- Centrifugal Casting: Sufei Wei, The Centrifugal Casting Machine Company, and Steve Lampman, ASM InternationalDokumen7 halamanCentrifugal Casting: Sufei Wei, The Centrifugal Casting Machine Company, and Steve Lampman, ASM InternationalmuseBelum ada peringkat
- ARP Mapping: in A Frame With The MAC Address of The Local Host, or Next-Hop RouterDokumen17 halamanARP Mapping: in A Frame With The MAC Address of The Local Host, or Next-Hop RoutermuseBelum ada peringkat
- How OFDM WorksDokumen9 halamanHow OFDM WorksmuseBelum ada peringkat
- 1205 3394 PDFDokumen20 halaman1205 3394 PDFmuseBelum ada peringkat
- How OFDM WorksDokumen9 halamanHow OFDM WorksmuseBelum ada peringkat
- Multi Carrier ModulationDokumen22 halamanMulti Carrier ModulationmuseBelum ada peringkat
- Final Projet 2010Dokumen31 halamanFinal Projet 2010museBelum ada peringkat
- Helsinki - Network PlanningDokumen26 halamanHelsinki - Network Planningjure.denkBelum ada peringkat
- Parabolic Reflector Antenna For Home ResidenceDokumen1 halamanParabolic Reflector Antenna For Home ResidencemuseBelum ada peringkat
- Aperture AntennaDokumen24 halamanAperture AntennamuseBelum ada peringkat
- Emw Group Assinment: Members IDDokumen17 halamanEmw Group Assinment: Members IDmuseBelum ada peringkat