Red
Diunggah oleh
Galo Mariduena0 penilaian0% menganggap dokumen ini bermanfaat (0 suara)
33 tayangan2 halamanThe document describes a VPN tunnel configuration between networks 192.168.10.0/24 and 134.209.233.19/32 using IPsec with AES256 encryption. Firewall rules are configured to accept IPSec traffic and masquerade traffic from 192.168.10.0/24. Logs show the establishment of tunnels for two clients.
Deskripsi Asli:
Red
Hak Cipta
© © All Rights Reserved
Format Tersedia
TXT, PDF, TXT atau baca online dari Scribd
Bagikan dokumen Ini
Apakah menurut Anda dokumen ini bermanfaat?
Apakah konten ini tidak pantas?
Laporkan Dokumen IniThe document describes a VPN tunnel configuration between networks 192.168.10.0/24 and 134.209.233.19/32 using IPsec with AES256 encryption. Firewall rules are configured to accept IPSec traffic and masquerade traffic from 192.168.10.0/24. Logs show the establishment of tunnels for two clients.
Hak Cipta:
© All Rights Reserved
Format Tersedia
Unduh sebagai TXT, PDF, TXT atau baca online dari Scribd
0 penilaian0% menganggap dokumen ini bermanfaat (0 suara)
33 tayangan2 halamanRed
Diunggah oleh
Galo MariduenaThe document describes a VPN tunnel configuration between networks 192.168.10.0/24 and 134.209.233.19/32 using IPsec with AES256 encryption. Firewall rules are configured to accept IPSec traffic and masquerade traffic from 192.168.10.0/24. Logs show the establishment of tunnels for two clients.
Hak Cipta:
© All Rights Reserved
Format Tersedia
Unduh sebagai TXT, PDF, TXT atau baca online dari Scribd
Anda di halaman 1dari 2
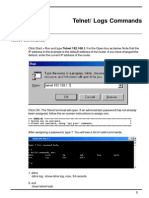
conn advancedTechCell
left=%defaultroute
leftsubnet=134.209.233.19/32
leftfirewall=yes
lefthostaccess=yes
right=186.3.220.228
rightsubnet=192.168.10.0/24
leftid=@ussd1
rightid=@ipfire.localdomain
type=tunnel
ike=aes256-md5-modp1024!
esp=aes256-md5-modp1024!
keyexchange=ikev2
ikelifetime=3h
keylife=1h
dpdaction=clear
dpddelay=30
dpdtimeout=120
authby=secret
auto=start
iptables -t nat -A POSTROUTING -s 192.168.10.0/24 -d 134.209.233.19/32 -j
MASQUERADE
10.100.2.200/21
Sep 17 22:15:27 ipfire vpn: client+ ussd1 10.100.2.201/32 == 134.209.233.19 --
192.168.2.19 == 192.168.10.0/24
Sep 17 22:15:27 ipfire vpn: tunnel+ 134.209.233.19 -- 192.168.2.19
Sep 17 22:16:41 ipfire vpn: client+ C=EC, O=samsung, CN=samsung 10.100.2.200/32 ==
45.236.169.232 -- 192.168.2.19 == 192.168.10.0/24
Sep 17 22:16:41 ipfire vpn: tunnel+ 45.236.169.232 -- 192.168.2.19
iptables -t nat -A POSTROUTING -s 192.168.5.0/24 -o eth0 -m policy --dir out --pol
ipsec -j ACCEPT
iptables -t nat -A POSTROUTING -s 192.168.5.0/24 -o eth0 -j MASQUERADE
route add -net 192.168.10.0/24 192.168.5.1
--list-all-zones List everything added for or enabled in all zones [P]
--list-all List everything added for or enabled in a zone [P] [Z]
--list-services List services added for a zone [P] [Z]
--list-ports List ports added for a zone [P] [Z]
--list-protocols List protocols added for a zone [P] [Z]
--list-source-ports List source ports added for a zone [P] [Z]
--list-icmp-blocks List Internet ICMP type blocks added for a zone [P] [Z]
--list-forward-ports List IPv4 forward ports added for a zone [P] [Z]
--list-rich-rules List rich language rules added for a zone [P] [Z]
--list-interfaces List interfaces that are bound to a zone [P] [Z]
--list-sources
[root@ussd1 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: ssh dhcpv6-client ipsec
ports: 500/udp 4500/udp 8080/tcp 3306/tcp 443/tcp 80/tcp 500/tcp 4500/tcp
protocols:
masquerade: yes
forward-ports:
source-ports:
icmp-blocks:
rich rules:
rule protocol value="esp" accept
rule protocol value="ah" accept
[root@ussd1 ~]# firewall-cmd --direct --get-all-rules
ipv4 nat POSTROUTING 0 -m policy --pol ipsec --dir out -j ACCEPT
"plink.exe" -batch -ssh -pw Kn@wc3lL01 root@134.209.233.19 "tcpdump -ni eth0 -s 0
-w -" | "D:\Program Files\Wireshark\Wireshark.exe" -k -i -
firewall-cmd --state
ip route show table 220
192.168.10.0/24 via 134.209.224.1 dev eth0 proto static src 192.168.5.1
Anda mungkin juga menyukai
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkDari EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkBelum ada peringkat
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityDari EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityBelum ada peringkat
- Rhel Notes For Rh253Dokumen27 halamanRhel Notes For Rh253jayaraj5382100% (1)
- Telekom SIP Trunk - GermanyDokumen7 halamanTelekom SIP Trunk - Germanyثائر هاني فرج اللهBelum ada peringkat
- HOWTO Ethereal Wireshark Trace enDokumen9 halamanHOWTO Ethereal Wireshark Trace enJose Carlos Fernandez VargasBelum ada peringkat
- SWHUENET01Dokumen53 halamanSWHUENET01leonardo.roslerBelum ada peringkat
- ##Verificación de Servicio PE##Dokumen10 halaman##Verificación de Servicio PE##libardoBelum ada peringkat
- Cisco1921 0Dokumen92 halamanCisco1921 0DeadMikeBelum ada peringkat
- Net AdminDokumen26 halamanNet AdminAnto PadaunanBelum ada peringkat
- WCCP Proxy ConfigurationDokumen7 halamanWCCP Proxy ConfigurationMd Ariful IslamBelum ada peringkat
- + Iptables: Packet Filtering && FirewallDokumen31 halaman+ Iptables: Packet Filtering && Firewall-aaa-Belum ada peringkat
- Site 2 Site VPNDokumen31 halamanSite 2 Site VPNwinter00Belum ada peringkat
- IPMP On Solaris 10Dokumen3 halamanIPMP On Solaris 10Mirza Jubayar TopuBelum ada peringkat
- Configuraciones Routers Puntos de VentaDokumen5 halamanConfiguraciones Routers Puntos de Ventaangela castroBelum ada peringkat
- Config. Roteador 2811Dokumen6 halamanConfig. Roteador 2811Asafh CamiloBelum ada peringkat
- IosDokumen11 halamanIoscarrotmadman6Belum ada peringkat
- Esxcfg Command HelpDokumen7 halamanEsxcfg Command HelpPieter BothaBelum ada peringkat
- MXK-Gpon-Unified Prov PPPoE - Telbo Rev1Dokumen6 halamanMXK-Gpon-Unified Prov PPPoE - Telbo Rev1Abdulfatah Kasim ImanBelum ada peringkat
- Nouveau Document TexteDokumen9 halamanNouveau Document Textetest testBelum ada peringkat
- Setingan MikrotikDokumen6 halamanSetingan Mikrotiktuyul sekenBelum ada peringkat
- Telnet CommandsDokumen9 halamanTelnet CommandsNithindev GuttikondaBelum ada peringkat
- RHCE 7 Exam Point of View Question and Answer - RHCE 7 DumsDokumen33 halamanRHCE 7 Exam Point of View Question and Answer - RHCE 7 Dumssivachandran kaliappanBelum ada peringkat
- Contoh Mikrotik: Load Balancing Multi Over Gateway Untuk LAN Dan Hotspot Plus Bandwith ManagementDokumen4 halamanContoh Mikrotik: Load Balancing Multi Over Gateway Untuk LAN Dan Hotspot Plus Bandwith ManagementTriple-eF NetBelum ada peringkat
- Firewall DDokumen6 halamanFirewall Dpaul andradeBelum ada peringkat
- Esxcfg-Firewall Esxcfg-Nics Esxcfg-Vswitch Esxcfg-Vswif Esxcfg-Route Esxcfg-VmknicDokumen6 halamanEsxcfg-Firewall Esxcfg-Nics Esxcfg-Vswitch Esxcfg-Vswif Esxcfg-Route Esxcfg-VmknicRogerio Cataldi RodriguesBelum ada peringkat
- Cisco Security Troubleshooting: Part I - Connectivity Through ASA or PIX FirewallsDokumen19 halamanCisco Security Troubleshooting: Part I - Connectivity Through ASA or PIX FirewallsAhmed ThabitBelum ada peringkat
- Muestra PingDokumen56 halamanMuestra PingJEAN LUISBelum ada peringkat
- Configuring A Cisco 827 For Pppoe With VPN Ipsec Nat OverloadingDokumen9 halamanConfiguring A Cisco 827 For Pppoe With VPN Ipsec Nat OverloadingAndika PajriBelum ada peringkat
- All - Linux - Iptables at Master K00lith - All GitHubDokumen3 halamanAll - Linux - Iptables at Master K00lith - All GitHubDoru Ciprian MuresanBelum ada peringkat
- Fichier de Configuration Mikrotik Sle Loango TchissangaDokumen9 halamanFichier de Configuration Mikrotik Sle Loango Tchissangakevinlevrai30Belum ada peringkat
- By Jamison SchmidtDokumen8 halamanBy Jamison SchmidtneevuBelum ada peringkat
- MCQ - Networktut V2Dokumen67 halamanMCQ - Networktut V2dee_g666Belum ada peringkat
- Integracion CISCO E ISSABELA-PBX KEVIN PARRA CME-KDokumen10 halamanIntegracion CISCO E ISSABELA-PBX KEVIN PARRA CME-KCINDY PAOLA PIEDRAHITA MESABelum ada peringkat
- 4.3.2.7 CommandsDokumen3 halaman4.3.2.7 CommandsStill ggBelum ada peringkat
- How To Install Router-FirewallDokumen6 halamanHow To Install Router-Firewallamazingguy07Belum ada peringkat
- Linux DVB Server Setup Commands 2006Dokumen3 halamanLinux DVB Server Setup Commands 2006api-3832033Belum ada peringkat
- VOD - Shift & Patch Upade RFC MOP - V3.0Dokumen65 halamanVOD - Shift & Patch Upade RFC MOP - V3.0Aizaz HussainBelum ada peringkat
- CCNA Router and Catalyst Switch IOS Command ReferenceDokumen8 halamanCCNA Router and Catalyst Switch IOS Command Referencemisio8118Belum ada peringkat
- Inappropriate Usage of Policy Action SeDokumen8 halamanInappropriate Usage of Policy Action SeDebarros MartinsBelum ada peringkat
- ASLogDokumen6 halamanASLogGaby IonitaBelum ada peringkat
- RWPS ApexM2 PublicDokumen9 halamanRWPS ApexM2 Publickuratsa49Belum ada peringkat
- Subnet /28: HostsDokumen9 halamanSubnet /28: HostsraymundoBelum ada peringkat
- Configuracion Dslam Huawei Smartax Ma5600Dokumen30 halamanConfiguracion Dslam Huawei Smartax Ma5600UserJoseBelum ada peringkat
- Configuracion Router Junos ChavarroDokumen4 halamanConfiguracion Router Junos ChavarroJA González CastillaBelum ada peringkat
- Firewall FBasic ExamplesDokumen3 halamanFirewall FBasic ExamplesKayode EmmanuelBelum ada peringkat
- Plantilla 10 MB NormadoDokumen35 halamanPlantilla 10 MB NormadoArturo SilvaBelum ada peringkat
- Show Run Router 2801Dokumen3 halamanShow Run Router 2801Manuel ArellanoBelum ada peringkat
- Plantilla 30MBDokumen46 halamanPlantilla 30MBArturo SilvaBelum ada peringkat
- Huawei Cli Output Modifiers PDFDokumen4 halamanHuawei Cli Output Modifiers PDFHussein DhafanBelum ada peringkat
- Secure Your Kloxo Installation With Your Firewall/IPTABLESDokumen4 halamanSecure Your Kloxo Installation With Your Firewall/IPTABLESMatt JanecekBelum ada peringkat
- Exercises:: Exercise # 1Dokumen5 halamanExercises:: Exercise # 1Osama FarooquiBelum ada peringkat
- NMAP Testing: Iptables Flushed in The Target (Default)Dokumen5 halamanNMAP Testing: Iptables Flushed in The Target (Default)Kanthanathan SBelum ada peringkat
- Config Router WANDokumen6 halamanConfig Router WANRonald EnriqueBelum ada peringkat
- SW PoldaDokumen5 halamanSW PoldabudiBelum ada peringkat
- Plantilla Reval Multipagas EncriptacionDokumen2 halamanPlantilla Reval Multipagas EncriptacionJA González CastillaBelum ada peringkat
- Plantilla Configuracion Mocrotik NewVersionDokumen7 halamanPlantilla Configuracion Mocrotik NewVersionJose Daniel CogolloBelum ada peringkat
- Hades EndgameDokumen42 halamanHades EndgameJean PierreBelum ada peringkat
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationDari EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationBelum ada peringkat
- 3900 Series Base Station ENodeBFunction Performance Counter Reference (V100R010C10 - 11) (PDF) - enDokumen4.129 halaman3900 Series Base Station ENodeBFunction Performance Counter Reference (V100R010C10 - 11) (PDF) - enTuanBelum ada peringkat
- Ex 2Dokumen5 halamanEx 2push5Belum ada peringkat
- Certificate: of ConformityDokumen3 halamanCertificate: of ConformityGerson SouzaBelum ada peringkat
- Surge AnalysisDokumen39 halamanSurge AnalysisAneeq Sh100% (1)
- Z7sz69ez Pandolfini x27 S Ultimate Guide To ChessDokumen4 halamanZ7sz69ez Pandolfini x27 S Ultimate Guide To Chessnair.aalamBelum ada peringkat
- AISC Seismic Design-Module2-Moment Resisting FramesDokumen231 halamanAISC Seismic Design-Module2-Moment Resisting FramesJon LawheadBelum ada peringkat
- Paper Week 11 - Concorde ProjectDokumen2 halamanPaper Week 11 - Concorde ProjectRay Mutalibov75% (4)
- Summer19 PDFDokumen16 halamanSummer19 PDFMoriyasu NguyenBelum ada peringkat
- 5051 AppDokumen37 halaman5051 AppawemetalBelum ada peringkat
- DVD Receiver Owner'S Manual: Model: Ht902TbDokumen27 halamanDVD Receiver Owner'S Manual: Model: Ht902TbJaijeev PaliBelum ada peringkat
- Arri Alexa User-Manual Sup 11.0 01Dokumen328 halamanArri Alexa User-Manual Sup 11.0 01Electra/Off TraxBelum ada peringkat
- Fuel Transport & On-Site Refuelling PDFDokumen2 halamanFuel Transport & On-Site Refuelling PDFcityofdarwingisBelum ada peringkat
- ATCOM IP04 IP PBX Appliance DatasheetDokumen2 halamanATCOM IP04 IP PBX Appliance Datasheetmaple4VOIPBelum ada peringkat
- Plains All American Pipeline Lines 901 and 903 Replacement ProjectDokumen2 halamanPlains All American Pipeline Lines 901 and 903 Replacement Projectgiana_magnoliBelum ada peringkat
- (Book No. 18) - (04) - Aerb Safety Code No. Aerb - SC-G - (Other)Dokumen59 halaman(Book No. 18) - (04) - Aerb Safety Code No. Aerb - SC-G - (Other)pratip_bBelum ada peringkat
- BPW EL Luft 1032701eDokumen184 halamanBPW EL Luft 1032701eSahaya GrinspanBelum ada peringkat
- IECDokumen7 halamanIECGerry MalapitanBelum ada peringkat
- Shift Charge Engineer: Rajahmundry, Andhra PradeshDokumen2 halamanShift Charge Engineer: Rajahmundry, Andhra PradeshBv RaoBelum ada peringkat
- 15 Inch PV755A Optoma PanoView PV755A MonitorDokumen3 halaman15 Inch PV755A Optoma PanoView PV755A MonitorVictor Tito C GBelum ada peringkat
- HAV-EXT-QC-STA-0245: Method Statement of Hdpe PipingDokumen19 halamanHAV-EXT-QC-STA-0245: Method Statement of Hdpe Pipingum erBelum ada peringkat
- Procurement Plan Oil & Gas New Main Warehouse, Brega, Area 1 Tareq AsiaDokumen25 halamanProcurement Plan Oil & Gas New Main Warehouse, Brega, Area 1 Tareq AsiaDanish mallickBelum ada peringkat
- Astm D25Dokumen7 halamanAstm D25Fatian RaktibutBelum ada peringkat
- 4.27 Density Computer FML621 Operating InstructionsDokumen170 halaman4.27 Density Computer FML621 Operating Instructionsel misBelum ada peringkat
- DownloadDokumen220 halamanDownloadfredloulouBelum ada peringkat
- Vcard 21Dokumen37 halamanVcard 21Tice HarmanBelum ada peringkat
- Superpower CS6K-290 - 295 - 300MS: Linear Power Output Warranty Key FeaturesDokumen2 halamanSuperpower CS6K-290 - 295 - 300MS: Linear Power Output Warranty Key FeaturesViviana RolónBelum ada peringkat
- ZXG10-BSC (V2) Maintenance ManualDokumen112 halamanZXG10-BSC (V2) Maintenance ManualBahara KhBelum ada peringkat
- EN ISO 9606 1 2013 E Codified PDFDokumen1 halamanEN ISO 9606 1 2013 E Codified PDFPM LOgsBelum ada peringkat
- Murphy FluidDokumen40 halamanMurphy FluiddptecnicocmspBelum ada peringkat
- Objectives - 2023Dokumen9 halamanObjectives - 2023JamieBelum ada peringkat