Applications of Bidirectional Forwarding Detection (BFD) : Rahul Aggarwal
Diunggah oleh
Alaa Al-saggafDeskripsi Asli:
Judul Asli
Hak Cipta
Format Tersedia
Bagikan dokumen Ini
Apakah menurut Anda dokumen ini bermanfaat?
Apakah konten ini tidak pantas?
Laporkan Dokumen IniHak Cipta:
Format Tersedia
Applications of Bidirectional Forwarding Detection (BFD) : Rahul Aggarwal
Diunggah oleh
Alaa Al-saggafHak Cipta:
Format Tersedia
Applications of
Bidirectional Forwarding
Detection (BFD)
Rahul Aggarwal
rahul@juniper.net
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 1
Overview
Goals
Protocol Overview
Applications
BFD’s applicability for Voice over IP
IETF status
Conclusion
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 2
Goals
Detection of forwarding plane-to-forwarding
plane connectivity (including links, interfaces,
tunnels etc.)
A single mechanism that is independent of
media, routing protocol, and data protocol
No changes to existing protocols
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 3
Goals
Faster convergence of routing protocols,
particularly on shared media (Ethernet)
Detection of one-way link failures
Semantic separation of forwarding plane
connectivity vs. control plane connectivity
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 4
BFD Protocol Overview
At its heart, Yet Another Hello Protocol
Packets sent at regular intervals; neighbor failure
detected when packets stop showing up
Intended to be implemented in the forwarding plane to
the extent possible (avoiding fate sharing with the control
plane)
Context defined by encapsulating protocol (sending
inside IPv4 packets signals IPv4 connectivity; also could
be sent over IPv6, directly over the datalink, or whatever)
Always unicast, even on shared media
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 5
BFD Protocol Overview
Not just for direct links; could also be used over MPLS
LSPs, or other unidirectional links (where the return path
is potentially routed over multiple hops)
Sufficient context in the protocol to keep track of multiple
parallel paths between systems
Timing is adjustable on-the-fly, allowing for adaptivity to
avoid catastrophic collapse due to false failure detection
Fully predictive (identical packets sent and received
when all is well), making implementation in firmware or
hardware more practical
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 6
BFD Operation
BFD Control Packets sent in both directions, providing
basic connectivity check and continuous parameter
negotiation
Optional Echo Mode can be negotiated
• BFD Echo Packets transmitted addressed to
originating system; other system forwards them back
through regular forwarding path
• Exercises entire forwarding path in destination system
• May not always be possible or desirable, thus it is
negotiated
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 7
BFD Async Mode
Control packets flow in each direction
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 8
BFD Echo Mode
Control packets flow in each direction
Echo packets loop through remote system
Control packet flow more sedate
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 9
BFD Operation
No discovery protocol; there are already enough of those
(IGPs et al)
Semantics of BFD session failure are contextual
• BFD-over-IP implies neighbor failure; IGP neighbor should
be torn down
• BFD-over-Ethernet implies switch failure; subnet should be
withdrawn from routing protocols
Works over a wide range of time constants
• Timers specified in microseconds, allowing very fast or
very slow detection
• Systems specify how quickly they can receive BFD
packets so that boxes of differing abilities can interoperate
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 10
BFD Applications
IGP liveliness detection
Tunnel liveliness detection
• MPLS LSPs
• IP-in-IP/GRE tunnels
BFD for edge network availability
BFD over ethernet
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 11
BFD for IGP Liveliness Detection
One of the first motivations for BFD
Faster convergence particularly on shared media
• Sub-second IGP adjacency failure detection
IGP hellos can be set to higher intervals
• Can improve IGP adjacency scaling
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 12
BFD for IGP Liveliness Detection..
BFD session boot-strapped by OSPF/IS-IS
• When the adjacency is established
• First BFD control packet is demuxed based on the
incoming IGP interface
State of the IGP adjacency is tied to the BFD session
• Adjacency is brought down if the BFD session fails
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 13
BFD for MPLS LSPs
Motivation
BFD can be used to detect the liveliness of MPLS LSPs
Light-weight compared to LSP-Ping
Sub-second failure detection times
Periodic fault detection possible
Fault detection for a larger number of LSPs
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 14
BFD for MPLS LSPs
Operation
BFD provides LSP data plane verification
However BFD doesn’t provide data plane – control plane
verification
• LSP-Ping does
Use BFD in conjunction with LSP-Ping
• Establish a BFD session for the MPLS LSP
• Boot strap BFD using LSP-Ping
• Periodically use LSP-Ping to verify data plane against
the control plane
• draft-raggarwa-mpls-bfd-00.txt
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 15
BFD for MPLS LSPs
Operation…
Health of the MPLS LSP tied to the BFD session
Failure of the BFD session results in
• MPLS LSP being declared down
• Alarms can be issued
Fast-reroute considerations
• Guard against ‘spurious’ failures
• BFD detection time should be more than fast-reroute
failover time
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 16
BFD for MPLS LSPs
Applicability
Transport LSPs
• Periodic fault detection to meet SLAs
MPLS PWs
• In the absence of end-to-end Layer 2 OAM, periodic
fault detection may be desired
Fast-reroute bypass LSPs
• Protect a number of primary LSPs
• Fast failure detection of a bypass LSP may be
desirable
• BFD session for the bypass LSP
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 17
BFD for MPLS LSPs
Layer 2 Transport over MPLS
Periodic BFD Fault Detection on Tunnel LSP and/or MPLS PW
MPLS Core
Tunnel LSP
ATM/FR ATM/FR
Access MPLS PW Access
Segment ATM OAM
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 18
BFD For GRE Tunnels
Motivation
GRE tunnels do not have a liveliness mechanism
GRE tunnel failure detection depends on IGP
• Doesn’t provide a means to test the tunnel egress’s
GRE forwarding path
• Sub-second failure detection is a challenge
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 19
BFD For GRE Tunnels
Operation
BFD session is established between the tunnel
endpoints
BFD session boot-strapped using:
• Configuration or
• Auto-discovery
Health of the GRE tunnel tied to the BFD
session
• BFD session failure results in declaring the
GRE tunnel down
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 20
BFD For GRE Tunnels
Applicability
IP applications over GRE tunnels
2547 VPNs over GRE tunnels
MPLS PWs over GRE tunnels
• Layer 2 VPNs
• VPLS
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 21
BFD For Edge Network Availability
Last Mile i.e. CE to PE fast failover is a missing piece
• Particularly for an ethernet infrastructure
Often relies on application timeout
• For eg. EBGP session timeout
Failure detection in the order of seconds
• Not acceptable for applications such as Voice over IP
BFD can be used to fill the Last Mile void
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 22
BFD Fills the Last Mile Void
A big opportunity
• Driven primarily by Voice over IP
Router-to-host liveliness detection
• For eg. Host is a media gateway
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 23
Router to Host Liveness Detection
BFD between router and host
• The host must support BFD
Host can be the Voice over IP gateway
Host can also be a web server
Support for common routing paradigms between
router and host
• Static routes
• EBGP peering
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 24
BFD for Static Routes
Host support
• Dual homed host
• BFD session to each router
• Should not be an echo session
• BFD session failure triggers failover to the
backup router
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 25
BFD for Static Routes..
Router support
• Static route to the subnet with the host as the
next-hop
• BFD session associated with the static route’s
next-hop.
• BFD session failure results in de-activating
the static route
• A backup route to reach the host takes over
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 26
BFD for EBGP Peers
CPE support
• Dual homed CPE
• BFD session to each EBGP peering router
• BFD session failure triggers failover to the backup
router
Router support
• BFD session to the EBGP peer
• BFD session failure results in declaring the EBGP
peer down
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 27
Voice Over IP
Meeting SLAs
End to end failure recovery times of ~300ms
MPLS backbone
• Fast reroute provides failure recovery times of
~50ms
What about the edge ?
• BFD on the edge allows fast failure detection
• Pre-setup alternate path allows fast failure
recovery
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 28
BFD for Edge Availability
Voice over IP
MPLS LSP + Fast Reroute
Static/EBGP +
BFD
IBGP route to MGW1
PE1 PE3
MGW1
MGW2
Ethernet infrastructure PE2
PE4
MGW Media Gateway
BFD between MGW and PEs
Enables fast detection/failover
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 29
BFD for Edge Availability
Voice over IP
BFD session failure
MPLS LSP + Fast Reroute
Primary path Static/EBGP +
BFD
IBGP route to MGW1
PE1 PE3
MGW1 MGW2
Backup path takes over
PE2 PE4
Link/switch failure
PE1 switches to a backup route
through PE2 to reach MGW1
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 30
BFD Over Ethernet
Motivation
OAM mechanism for ethernet links is needed
• Fast failure detection over ethernet not
possible currently
Router to a CE
Router to an ethernet switch
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 31
BFD Over Ethernet
Operation
BFD directly over ethernet i.e. 802.3
BFD session established between the router and
a CE or an ethernet switch
• Driven by configuration
BFD control packets can be sent directly over
ethernet
• A new ether type to identify BFD packets is
needed
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 32
BFD IETF Status
Protocol jointly developed by Juniper and Cisco
Base spec: draft-katz-ward-bfd-01.txt
Over IP: draft-katz-ipv4-ipv6-01.txt
Over MPLS: draft-raggarwa-mpls-bfd-00.txt
A BFD WG has been formed
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 33
Conclusion
Increasing interest in the service provider
community
Shipping in JunOS for IGP since 6.1
Copyright © 2003 Juniper Networks, Inc. Proprietary and Confidential www.juniper.net 34
Anda mungkin juga menyukai
- Route 2 Eigrp ImplementingeigrpDokumen97 halamanRoute 2 Eigrp ImplementingeigrpAdrian AdmiBelum ada peringkat
- Ospf PDFDokumen2 halamanOspf PDFJerson andrade fasanandoBelum ada peringkat
- Routing Information Protocol (RIP)Dokumen5 halamanRouting Information Protocol (RIP)Kyawzaw AungBelum ada peringkat
- BRKSEC-2695 - Building An Enterprise Access Control Architecture Using ISE and Trust SecDokumen179 halamanBRKSEC-2695 - Building An Enterprise Access Control Architecture Using ISE and Trust SecmorpheusnaakBelum ada peringkat
- 7.2.2.4 Packet Tracer - Configuring Basic EIGRP With IPv4 Instructions IGDokumen5 halaman7.2.2.4 Packet Tracer - Configuring Basic EIGRP With IPv4 Instructions IGkarenBelum ada peringkat
- © 2019 Juniper Networks: Juniper Business Use OnlyDokumen26 halaman© 2019 Juniper Networks: Juniper Business Use OnlyKettab ZoherBelum ada peringkat
- Telecom Interview Questions Answers Guide PDFDokumen10 halamanTelecom Interview Questions Answers Guide PDFtom2626Belum ada peringkat
- A10 Thunder ADC Series PDFDokumen8 halamanA10 Thunder ADC Series PDFRizqi Angga PratamaBelum ada peringkat
- Juniper CosDokumen2 halamanJuniper CosSiva TejaBelum ada peringkat
- BRKSPG 2402Dokumen84 halamanBRKSPG 2402cool dude911Belum ada peringkat
- Chapter 3 Lab 3-7, OSPF Case Study: TopologyDokumen6 halamanChapter 3 Lab 3-7, OSPF Case Study: TopologyTony Hayek100% (2)
- Lab - 5 - OSPFDokumen10 halamanLab - 5 - OSPFLipp00 M0MA100% (1)
- Data Center Switching: Nexus 9000 Series SwitchesDokumen23 halamanData Center Switching: Nexus 9000 Series SwitchesVIMAL KUMAR CHAUHANBelum ada peringkat
- Ccnpv6 Route SbaDokumen4 halamanCcnpv6 Route SbaAtilio Alexander100% (1)
- BRKSEC 3052 TroubleshootingDokumen133 halamanBRKSEC 3052 Troubleshootingvch801Belum ada peringkat
- Learning Guide - How Does VoIP WorkDokumen18 halamanLearning Guide - How Does VoIP Workshubham_cool1996Belum ada peringkat
- Tecccie 3000 PDFDokumen246 halamanTecccie 3000 PDFMario Aguirre HelgueroBelum ada peringkat
- Juniper Networks Virtual Chassis Fabric TechnologyDokumen8 halamanJuniper Networks Virtual Chassis Fabric TechnologyVan LeBelum ada peringkat
- Asr9k Multicast Troubleshooting ExternalDokumen25 halamanAsr9k Multicast Troubleshooting Externalsurge031Belum ada peringkat
- IPv4 Addressing and SubnettingDokumen37 halamanIPv4 Addressing and SubnettingGJ RecaldeBelum ada peringkat
- Sense of Security VoIP Security Testing Training (PDFDrive)Dokumen160 halamanSense of Security VoIP Security Testing Training (PDFDrive)haitham aloolBelum ada peringkat
- 22 Typical Campus Network Architectures and PracticesDokumen32 halaman22 Typical Campus Network Architectures and PracticesDerick Wayne BatucanBelum ada peringkat
- INE - Routing Technologies for ProfessionalsDokumen1 halamanINE - Routing Technologies for ProfessionalsBilel AmeurBelum ada peringkat
- CISCO OTV On ASR1002Dokumen38 halamanCISCO OTV On ASR1002oscarledesmaBelum ada peringkat
- Wireless LAN ComponentsDokumen6 halamanWireless LAN ComponentsEphrem ChernetBelum ada peringkat
- Ccie Rs 400-101 UpdateDokumen234 halamanCcie Rs 400-101 UpdateEduardo AguilarBelum ada peringkat
- Storage BasicsDokumen103 halamanStorage BasicsCharlie FlowersBelum ada peringkat
- Virtual Link Trunking-Reference Architecture 2 0 - External PDFDokumen84 halamanVirtual Link Trunking-Reference Architecture 2 0 - External PDFVanquish64Belum ada peringkat
- What's New Cisco ACI 5.x ReleaseDokumen61 halamanWhat's New Cisco ACI 5.x Releaseravi kantBelum ada peringkat
- Huawei Firewall System Overview and Basic ConceptsDokumen61 halamanHuawei Firewall System Overview and Basic ConceptsAbdelilah CharboubBelum ada peringkat
- TCP IP ApplicationsDokumen10 halamanTCP IP ApplicationsJetesh DevgunBelum ada peringkat
- Broadband Subscriber Services Feature Guide - 14.2Dokumen856 halamanBroadband Subscriber Services Feature Guide - 14.2openid_dr4OPAdEBelum ada peringkat
- Botnets Infrastructure and AttacksDokumen51 halamanBotnets Infrastructure and AttacksianpcoxBelum ada peringkat
- Juniper StudiesDokumen7 halamanJuniper StudiesJohnBelum ada peringkat
- Junos Release Notes 18.1r2 PDFDokumen265 halamanJunos Release Notes 18.1r2 PDFRogérs Rizzy MugangaBelum ada peringkat
- Cisco Security PDFDokumen678 halamanCisco Security PDF40539216Belum ada peringkat
- Ruckus Enterprise Campus NetworkDokumen27 halamanRuckus Enterprise Campus NetworkFrendi Yusroni RomadhonaBelum ada peringkat
- Radisys Mediaengine™ Nokia Cbam Installtion Guide: Release V11.0.0Dokumen15 halamanRadisys Mediaengine™ Nokia Cbam Installtion Guide: Release V11.0.0FERIDBelum ada peringkat
- Chapter 6: IP Routing Essentials: CCNP Enterprise: Core NetworkingDokumen37 halamanChapter 6: IP Routing Essentials: CCNP Enterprise: Core NetworkingPhan Sư ÝnhBelum ada peringkat
- Netelastic VBNG Manager Installation GuideDokumen11 halamanNetelastic VBNG Manager Installation GuideKhaing myal HtikeBelum ada peringkat
- JNCIP-SEC JN0 634 (Update Answers)Dokumen27 halamanJNCIP-SEC JN0 634 (Update Answers)leehsiehyangBelum ada peringkat
- Telecommunications Job Interview Preparation GuideDokumen8 halamanTelecommunications Job Interview Preparation GuideNourhan KhaledBelum ada peringkat
- Technical Proposal - Ipsec VPN ImplementationDokumen6 halamanTechnical Proposal - Ipsec VPN ImplementationSai Kyaw HtikeBelum ada peringkat
- Cisco Switch 9300 - DatasheetDokumen61 halamanCisco Switch 9300 - DatasheetJose RojasBelum ada peringkat
- Cisco IOS XR Virtual Private Network Configuration Guide for the Cisco CRS RouterDokumen86 halamanCisco IOS XR Virtual Private Network Configuration Guide for the Cisco CRS RouterAung Zaw Lin100% (1)
- DKNOG12 Rev1b PDFDokumen48 halamanDKNOG12 Rev1b PDFGinger NixBelum ada peringkat
- Cisco DNA Center Wireless Assurance TDMDokumen310 halamanCisco DNA Center Wireless Assurance TDMThang Cao BaBelum ada peringkat
- Basic Cisco CommandsDokumen5 halamanBasic Cisco CommandsiarnabBelum ada peringkat
- Config Guide Routing Is Is PDFDokumen702 halamanConfig Guide Routing Is Is PDFLe KhangBelum ada peringkat
- IOS XR Introduction: Anilkumar Dantu CCIE (22536) HTTS, Cisco SystemsDokumen16 halamanIOS XR Introduction: Anilkumar Dantu CCIE (22536) HTTS, Cisco Systemslamvan tuBelum ada peringkat
- Cisco 4500 Config GuideDokumen1.120 halamanCisco 4500 Config GuideDeepuBelum ada peringkat
- PT Activity 8.6.1: CCNA Skills Integration Challenge: Topology DiagramDokumen7 halamanPT Activity 8.6.1: CCNA Skills Integration Challenge: Topology DiagramKok KosmaraBelum ada peringkat
- Troubleshooting Campus Networks: Practical Analysis of Cisco and LAN ProtocolsDari EverandTroubleshooting Campus Networks: Practical Analysis of Cisco and LAN ProtocolsPenilaian: 4 dari 5 bintang4/5 (1)
- IBM Security QRadar SIEM A Complete Guide - 2021 EditionDari EverandIBM Security QRadar SIEM A Complete Guide - 2021 EditionBelum ada peringkat
- TW QFabric TrafficFlowsDokumen82 halamanTW QFabric TrafficFlowsAlaa Al-saggafBelum ada peringkat
- Oracle Database Firewall Asm DGDokumen15 halamanOracle Database Firewall Asm DGAlaa Al-saggafBelum ada peringkat
- Customizing The Database of A V8 Profile in Reporter.6Dokumen4 halamanCustomizing The Database of A V8 Profile in Reporter.6Alaa Al-saggafBelum ada peringkat
- Management Authentication Using Windows IAS As A Radius ServerDokumen16 halamanManagement Authentication Using Windows IAS As A Radius Serverpablofs_93Belum ada peringkat
- Web Filtering enDokumen16 halamanWeb Filtering enbogatoffBelum ada peringkat
- Aruba Support Services Quick Reference GuideDokumen4 halamanAruba Support Services Quick Reference GuideAlaa Al-saggafBelum ada peringkat
- Configuring Junos BasicsDokumen84 halamanConfiguring Junos BasicsG3000LEEBelum ada peringkat
- PAN Initial Configuration 4.1Dokumen12 halamanPAN Initial Configuration 4.1Teodor ChiricaBelum ada peringkat
- PA500 SpecsheetDokumen3 halamanPA500 SpecsheetJustin JefferyBelum ada peringkat
- Next Generation Firewall Launch FAQDokumen2 halamanNext Generation Firewall Launch FAQAlaa Al-saggafBelum ada peringkat
- BlueCoat PROXYSG 300 600 900 9000 Acceleration EditionDokumen2 halamanBlueCoat PROXYSG 300 600 900 9000 Acceleration EditionAlaa Al-saggafBelum ada peringkat
- Bcs Ds Training BCCPA EN v3b PDFDokumen1 halamanBcs Ds Training BCCPA EN v3b PDFAndroBelum ada peringkat
- CcnaDokumen4 halamanCcnaksant77Belum ada peringkat
- SRX Troubleshooting Command Library.v3Dokumen39 halamanSRX Troubleshooting Command Library.v3Alaa Al-saggafBelum ada peringkat
- f5 Microsoft Remote Desktop Services DGDokumen29 halamanf5 Microsoft Remote Desktop Services DGAlaa Al-saggafBelum ada peringkat
- CITRIX NS TRAD Site Resources Dynamic Salesdocs Adv Load Balancers 8 Features1Dokumen9 halamanCITRIX NS TRAD Site Resources Dynamic Salesdocs Adv Load Balancers 8 Features1Alaa Al-saggafBelum ada peringkat
- Blue CoatDokumen1.034 halamanBlue Coatstevex1982100% (1)
- Nortel CS1000 Basic Maintenance CommandsDokumen1 halamanNortel CS1000 Basic Maintenance CommandsAlaa Al-saggaf100% (1)
- Citrix AGEE ICAProxyXenAppDokumen49 halamanCitrix AGEE ICAProxyXenAppAlaa Al-saggafBelum ada peringkat
- IP Addressing & Subnetting WorkbookDokumen58 halamanIP Addressing & Subnetting Workbookbaraynavab94% (32)
- Webinar SLIDESDokumen52 halamanWebinar SLIDESMary FallBelum ada peringkat
- Apache Flume - Data Transfer in Hadoop - TutorialspointDokumen2 halamanApache Flume - Data Transfer in Hadoop - TutorialspointMario SoaresBelum ada peringkat
- City Layers DocumentationDokumen80 halamanCity Layers Documentationnupur patel100% (1)
- GUI Payroll SystemDokumen4 halamanGUI Payroll Systemfeezy1Belum ada peringkat
- Fake News Detection Using LSTMDokumen67 halamanFake News Detection Using LSTMshoaib arshathBelum ada peringkat
- Mtap - Deped Program of Excellence in Mathematics Grade 5 Session 1Dokumen28 halamanMtap - Deped Program of Excellence in Mathematics Grade 5 Session 1Gil FernandezBelum ada peringkat
- Microsoft Word - INTRODUCTION TO PLC CONTROLLERSDokumen115 halamanMicrosoft Word - INTRODUCTION TO PLC CONTROLLERSMilan RakshitBelum ada peringkat
- NetworksDokumen3 halamanNetworksMuhd Hanif Mat RusdiBelum ada peringkat
- Guidelines For Submission of ProjectDokumen9 halamanGuidelines For Submission of ProjectRahul KaushikBelum ada peringkat
- Amity School of Engineering & Technology: B. Tech. (MAE), V Semester Rdbms Sunil VyasDokumen13 halamanAmity School of Engineering & Technology: B. Tech. (MAE), V Semester Rdbms Sunil VyasJose AntonyBelum ada peringkat
- First Math Handout PDFDokumen4 halamanFirst Math Handout PDFMichael Lopez IIBelum ada peringkat
- Filetype Johnnie PDFDokumen1 halamanFiletype Johnnie PDFFrankBelum ada peringkat
- Inverse of A 3x3 Matrix.Dokumen2 halamanInverse of A 3x3 Matrix.rodwellheadBelum ada peringkat
- Lecture Notes Artificial Intelligence COMP 241: Niccolo Machiavelli, Italian (1469-1527)Dokumen15 halamanLecture Notes Artificial Intelligence COMP 241: Niccolo Machiavelli, Italian (1469-1527)Ahmad JafaryBelum ada peringkat
- Coop's three-part research program and income statement projectionsDokumen3 halamanCoop's three-part research program and income statement projectionsKuthe Prashant GajananBelum ada peringkat
- JDBC Drivers: Java Database Connectivity (JDBC) Is An Application ProgrammingDokumen6 halamanJDBC Drivers: Java Database Connectivity (JDBC) Is An Application Programmingsupriya028Belum ada peringkat
- UHD 4th Class Computer Science ExercisesDokumen13 halamanUHD 4th Class Computer Science ExercisesuxBelum ada peringkat
- PDF 9532Dokumen158 halamanPDF 9532NenoBelum ada peringkat
- FEMCI Book VibrationDokumen1 halamanFEMCI Book VibrationSURESH BABUBelum ada peringkat
- H2OFFT UserGuide Windows V5.31Dokumen55 halamanH2OFFT UserGuide Windows V5.31Joe Jeyaseelan100% (1)
- Z-Mobile Computing Seminar ReportDokumen21 halamanZ-Mobile Computing Seminar ReportSurangma ParasharBelum ada peringkat
- Cad Desk Student Fee's ReceiptDokumen2 halamanCad Desk Student Fee's ReceiptPushpendra LodhiBelum ada peringkat
- KPRIET Deep Learning BrochureDokumen2 halamanKPRIET Deep Learning BrochureJuan Daniel Garcia VeigaBelum ada peringkat
- XpadminDokumen17 halamanXpadminfiredigitalBelum ada peringkat
- Unifier Managers UserDokumen597 halamanUnifier Managers UsersmrajbeBelum ada peringkat
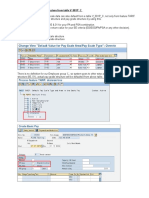
- Default Pay Scale/Grade Structure From Table V - 001P - CDokumen7 halamanDefault Pay Scale/Grade Structure From Table V - 001P - CDeepa ShiligireddyBelum ada peringkat
- Create Article Master and Cost from SpecificationDokumen159 halamanCreate Article Master and Cost from SpecificationGurushantha DoddamaniBelum ada peringkat
- M6800. Assembly Language ProgrammingDokumen53 halamanM6800. Assembly Language ProgrammingglizBelum ada peringkat
- Windows Operating SystemDokumen13 halamanWindows Operating Systemwdawdawgmail.comBelum ada peringkat