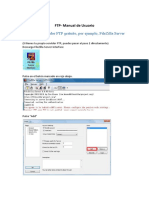
Parámetro Del GateWay and Message Server
Diunggah oleh
Miguel F. Matos G.Deskripsi Asli:
Judul Asli
Hak Cipta
Format Tersedia
Bagikan dokumen Ini
Apakah menurut Anda dokumen ini bermanfaat?
Apakah konten ini tidak pantas?
Laporkan Dokumen IniHak Cipta:
Format Tersedia
Parámetro Del GateWay and Message Server
Diunggah oleh
Miguel F. Matos G.Hak Cipta:
Format Tersedia
Parmetro:
gw/sec_info
Descripcin breve: external security filename for gateway Descripcin parmetro: Este parmetro permite evitar que programas externos puedan ser ejecutados. Actualizando el fichero secinfo en el directorio de datos de la instancia gateway, se puede evitar la ejecucin no autorizada de los programas externos. Las entradas de este fichero tienen la sintaxis siguiente: [USER=<user>] [PWD=<pwd>] [USER-HOST=<user_host>] [HOST=<host>] [TP=<tp>] Mediante una lnea determinada se permite al usuario <user> lanzar el programa <tp> en la mquina <host>. Esta verificacin de autorizacin puede intensificarse indicando los parmetros opcionales PWD y/o USERHOST. Ejemplos: USER=mueller HOST=hw1414 TP=test USER=hugo PWD=pass USER-HOST=hw1234 HOST=hw1414 TP=prog
El usuario mueller est autorizado para ejecutar el programa test en la mquina hw1414. El usuario hugo est autorizado para ejecutar el programa prog en la mquina hw1414, en caso de haberse identificado en el gateway desde la mquina hw1234 y de haber fijado la palabra clave de seguridad en pass mediante la llamada CMSCSP de CPIC. Si el usuario ha fijado el usuario de seguridad mediante la llamada CMSCSU, ste ser utilizado para la verificacin. En todos los parmetros puede utilizarse '*' como comodn. En caso de no haberse indicado PWD y/o USER-HOST, se tomar el valor '*' en su lugar. Ejemplo: Todos los usuario debe estar autorizados para ejecutar el programa test en la mquina hw1414: USER=* HOST=hw1414 TP=test; La lista actual de las entradas de seguridad puede visualizarse a travs del monitor y se puede iniciar un refrescado (refresh) procedente del fichero de seguridad. rea funcional: gateway Unidad : nombre de fichero Valor por defecto: <Data-Directory>/secinfo Quin puede modificar: cliente Limitaciones respecto a sist.operativos: ninguna Limitaciones respecto a los sistemas de BD: ninguna
Existen otros parmetros afectados o dependientes: ninguno Entradas, formatos y reas vlidos: nombre de fichero. Parameter : gw/reg_info Short Description : External security filename for gateway Parameter Description: You can use this parameter to protect the registration of external programs. You can avoid the unauthorized registration of programs by maintaining the file reginfo in the data directory of the gateway instance. If the file exists, the system searches for valid entries for the registration here. It also searches, as previously, in the gw/sec_info files. You can define the entries better than previously by using the reginfo file. Entries in this file have the following syntax: TP=<tp> [HOST=<hostname>] [NO=<n>] [ACCESS=<hostname>] [CANCEL=<hostname>] You can use a corresponding row to allow specific programs to register themselves from another host. Valid TP names: No restriction : * TP names : foo Start of name : foo* Valid host names: No restriction :* Host name : such as sapprod IP address : 192.1.1.3 Domain : *.sap.com Subnetwork addresses: 192.1.1.* Examples of valid entries: TP=* All registrations allowed HOST=* TP=foo* All registrations that begin with foo, but not f or fo, are allowed HOST=*.sap.com TP=* All registrations from the domain *.sap.com are allowed If the TP name was specified without wild cards, you can also specify the number of permissible registrations. Example: HOST=* TP=foo NO=1 , that is, only one program with the name foo can register, all other attempts to register by a program with this name are rejected.
You can also define an access list for each entry, to control access to the registered programs from the client side. An access list is a name of host names that must conform to the above rules. However, "*" is not allowed here. If no access list is specified, the program can be used from any client. The local gateway, with which the program is registered, always has access. It is important to note that this is a check based on hosts, and not at user level, such as: HOST=* TP=foo ACCESS=*.sap.com The program foo can only be accessed by hosts from the domain *.sap.com. Accesses from another domain are rejected. You can use the CANCEL list to define whether other clients may end the registered program. The same rules apply for this list as for HOST or ACCESS, such as: HOST=* TP=foo ACCESS=*.sap.com CANCEL=*.wdf.sap.corp The program foo can only be ended by clients that have logged on from the domain wdf.sap.corp. Application area: Gateway Unit : File Default value : <data directory>/reginfo Who is permitted to make changes: The customer Limitations for operating systems: None Limitations for database systems: None Other parameters affected or dependent: None Valid Inputs, Formats, Areas : File name
Anda mungkin juga menyukai
- Linux 9-16 ExamenesDokumen13 halamanLinux 9-16 ExamenesAndreaChicaiza70% (10)
- Examen9 18Dokumen15 halamanExamen9 18jchoque31460% (15)
- El Proceso Unificado de Desarrollo de Software - James Rumbaugh, Ivar Jacobson, Grady BoochDokumen458 halamanEl Proceso Unificado de Desarrollo de Software - James Rumbaugh, Ivar Jacobson, Grady BoochJuanf432182% (11)
- Orfeo Manual Instalacion PrincipiantesDokumen24 halamanOrfeo Manual Instalacion Principiantesluchiano100% (1)
- Paquete API PHP - MikroTik Wiki-EsDokumen12 halamanPaquete API PHP - MikroTik Wiki-Esgustavito920124209450% (1)
- El Archivo de Configuracion DHCPD ConfDokumen4 halamanEl Archivo de Configuracion DHCPD ConfArmando FernandezBelum ada peringkat
- Comandos FortigateDokumen4 halamanComandos FortigateLuis GonzalezBelum ada peringkat
- Examen de I Unidad - Ing - SoftwareDokumen3 halamanExamen de I Unidad - Ing - SoftwareholaBelum ada peringkat
- Informe Pic 16f84aDokumen10 halamanInforme Pic 16f84aArmando Nahuelneri MuñozBelum ada peringkat
- Instalación y Configuración de Un Servidor FTPDokumen28 halamanInstalación y Configuración de Un Servidor FTPAngel Vázquez Patiño100% (1)
- Instalación de Servicios en Linux-Tarea 1Dokumen20 halamanInstalación de Servicios en Linux-Tarea 1alherzBelum ada peringkat
- Servidor XinetDokumen4 halamanServidor Xinetdavid_cdbaBelum ada peringkat
- Guia para La Seguridad y Rendimiento de Un Servicio FTP PDFDokumen8 halamanGuia para La Seguridad y Rendimiento de Un Servicio FTP PDFCarlos Geovanny Escobar PortilloBelum ada peringkat
- Comandos Ejercicio 4 BashDokumen9 halamanComandos Ejercicio 4 BashChristian MendezBelum ada peringkat
- Modulo 6 - FTPDokumen18 halamanModulo 6 - FTPLaura Natalia ErmiagaBelum ada peringkat
- Practica 5 - Reporte Servidor FTPDokumen15 halamanPractica 5 - Reporte Servidor FTPFrank DiazBelum ada peringkat
- Protocolo Individual 2 BASE DE DATOS LLDokumen6 halamanProtocolo Individual 2 BASE DE DATOS LLandres argelBelum ada peringkat
- Procedimiento de Instalación de Graylog 3.0 at CentOS 7Dokumen9 halamanProcedimiento de Instalación de Graylog 3.0 at CentOS 7donpoolBelum ada peringkat
- Modulo 4. Servicios de Red Sobre LinuxDokumen42 halamanModulo 4. Servicios de Red Sobre LinuxMauricio AnentoBelum ada peringkat
- Aw02 FTPDokumen8 halamanAw02 FTPAngélica Bertha Carvajal QuintanaBelum ada peringkat
- Practica VSFTPOkV1Dokumen14 halamanPractica VSFTPOkV1Fatima CortesBelum ada peringkat
- Instalación y Configuración de Servicios FTP y Telnet en UbuntuDokumen12 halamanInstalación y Configuración de Servicios FTP y Telnet en UbuntuvelasgugolBelum ada peringkat
- ProFTPD - Un Servidor FTP para ProfesionalesDokumen5 halamanProFTPD - Un Servidor FTP para Profesionalesinfobits100% (1)
- 10.2.3.3 Lab - Exploring FTPDokumen9 halaman10.2.3.3 Lab - Exploring FTPdavvvidgalBelum ada peringkat
- Como Hacer Un Web Proxy Con SquidDokumen8 halamanComo Hacer Un Web Proxy Con SquidPGMejiaBelum ada peringkat
- AdminGuide EsDokumen452 halamanAdminGuide Esgabo1114524Belum ada peringkat
- Configuracionde Backup PCDokumen9 halamanConfiguracionde Backup PCCristhian PonceBelum ada peringkat
- Practica RPCDokumen14 halamanPractica RPCVirginia GarciaBelum ada peringkat
- Conf 4 Seguridad en Bases de DatosDokumen16 halamanConf 4 Seguridad en Bases de DatoskevinBelum ada peringkat
- 1.1 110 - 1-SeguridadDokumen6 halaman1.1 110 - 1-Seguridadpajaro amarilloBelum ada peringkat
- Cómo Configurar Pure-FtpdDokumen7 halamanCómo Configurar Pure-Ftpddescarga83Belum ada peringkat
- Manual de Instalación y Configuración HadoopDokumen13 halamanManual de Instalación y Configuración HadoopInversiones SolisBelum ada peringkat
- Servidor FTPDokumen13 halamanServidor FTPsmil01Belum ada peringkat
- Configuracion Rsyslog y SyslogDokumen6 halamanConfiguracion Rsyslog y SyslogDaniel HidalgoBelum ada peringkat
- OpenSSH en UBUNTUDokumen7 halamanOpenSSH en UBUNTUÁlvaro RocaBelum ada peringkat
- 10.2.3.3 Lab - Exploring FTP - ILMDokumen10 halaman10.2.3.3 Lab - Exploring FTP - ILMgivangustavoBelum ada peringkat
- Foglight Management Server5.9.4 20190513v1.5Dokumen12 halamanFoglight Management Server5.9.4 20190513v1.5pablojrcBelum ada peringkat
- Manual TicketDokumen8 halamanManual TicketHisterlee RamirezBelum ada peringkat
- HotSpot INDEXDokumen57 halamanHotSpot INDEXjersonmalesBelum ada peringkat
- Manual de Instalacion Servicio FTPDokumen9 halamanManual de Instalacion Servicio FTPMily MartinezBelum ada peringkat
- Manual SSHDokumen18 halamanManual SSHJose H OnchiBelum ada peringkat
- Ejercicios Avanzados de Apache2Dokumen7 halamanEjercicios Avanzados de Apache2Daniel Moreno BarónBelum ada peringkat
- Memoria 2014Dokumen37 halamanMemoria 2014Javier BenavidesBelum ada peringkat
- Instalacion RoundcubeDokumen4 halamanInstalacion RoundcubeJavier Sanós GiménezBelum ada peringkat
- Hots PotDokumen35 halamanHots PotChris KratosBelum ada peringkat
- LAB03 Flash Operator Panel 2Dokumen4 halamanLAB03 Flash Operator Panel 2Shiroi Enrique Diaz Mayta100% (1)
- Centos 7Dokumen27 halamanCentos 7Miguel Angel Gonzalez GBelum ada peringkat
- Instalar FTP Server en LinuxDokumen2 halamanInstalar FTP Server en LinuxAle MartinezBelum ada peringkat
- PROFTPDDokumen6 halamanPROFTPDKEVIN369Belum ada peringkat
- Guía de Uso de Servidor ProxyDokumen6 halamanGuía de Uso de Servidor ProxyJorge Horacio Pérez EspinalesBelum ada peringkat
- Informatica Forense I Eje 4Dokumen14 halamanInformatica Forense I Eje 4Oscar PachecoBelum ada peringkat
- Informática Forense I Eje 4 - GrupalDokumen12 halamanInformática Forense I Eje 4 - GrupalOzkar Dia'zBelum ada peringkat
- Mi - Catalogo - de - Comandos LinuxDokumen18 halamanMi - Catalogo - de - Comandos LinuxEder Santiago SalazarBelum ada peringkat
- Taller - 3 Sistemas OperativosDokumen32 halamanTaller - 3 Sistemas Operativosricardor73Belum ada peringkat
- SudoersDokumen6 halamanSudoersJorge L Mendoza MendozaBelum ada peringkat
- Sistemas Operativos-FTPDokumen4 halamanSistemas Operativos-FTPAlyss VizcaïnoBelum ada peringkat
- Práctica de Laboratorio - Exploración Del Protocolo FTPDokumen9 halamanPráctica de Laboratorio - Exploración Del Protocolo FTPAaron EcheverriaBelum ada peringkat
- Instalar y Configurar Fail2banDokumen15 halamanInstalar y Configurar Fail2banjormer bermudezBelum ada peringkat
- Manuales de Usuario Configuración Del FTPDokumen11 halamanManuales de Usuario Configuración Del FTPHans Malcolm Rasch DiazBelum ada peringkat
- Apuntes MikrotikDokumen133 halamanApuntes MikrotikCristian Pérez LecarosBelum ada peringkat
- Smoke PingDokumen14 halamanSmoke PingpatybonillaBelum ada peringkat
- Resolución de averías lógicas en equipos microinformáticos. IFCT0309Dari EverandResolución de averías lógicas en equipos microinformáticos. IFCT0309Belum ada peringkat
- UF1271 - Instalación y configuración del software de servidor webDari EverandUF1271 - Instalación y configuración del software de servidor webBelum ada peringkat
- Eliminar Virus y Otros Archivos Utilizando La Consola de CMD o MSDOSDokumen8 halamanEliminar Virus y Otros Archivos Utilizando La Consola de CMD o MSDOSMarco Antonio Fernandez CopaBelum ada peringkat
- Praticas MicrosDokumen19 halamanPraticas MicrosArroz Frito Poki de LimónBelum ada peringkat
- Suficiencia en InformaticaDokumen97 halamanSuficiencia en InformaticaJohn Jara CobosBelum ada peringkat
- Ejercicios Prácticos en JavaDokumen9 halamanEjercicios Prácticos en JavaEdgar GonzaloBelum ada peringkat
- Inteligencia Artificial Mendoza Silva Cesar ErnestoDokumen5 halamanInteligencia Artificial Mendoza Silva Cesar ErnestoCesar ErnestoBelum ada peringkat
- Comandos Unix-Linux PDFDokumen13 halamanComandos Unix-Linux PDFEsteban OrtizBelum ada peringkat
- Manual Operador IRC5 y RobotStudio-Procedimientos InicialesDokumen50 halamanManual Operador IRC5 y RobotStudio-Procedimientos InicialesLuis Aurelio Garcia FernandezBelum ada peringkat
- Ejercicios de Programacion Lineal Resueltos Mediante El Metodo SimplexDokumen8 halamanEjercicios de Programacion Lineal Resueltos Mediante El Metodo SimplexBeatriz DC Rincon100% (1)
- Códigos de Errores A1800Dokumen2 halamanCódigos de Errores A1800Enrique Tejada Farfan60% (5)
- Lenguajes de Bajo Nivel en MicrocontroladoresDokumen4 halamanLenguajes de Bajo Nivel en MicrocontroladoresMilenka QgBelum ada peringkat
- VMC On AWS 10 Preguntas y 10 RespuestasDokumen3 halamanVMC On AWS 10 Preguntas y 10 RespuestasUP TECHBelum ada peringkat
- S08. Construcción de GUIDokumen54 halamanS08. Construcción de GUIEdward Martin Julca SánchezBelum ada peringkat
- Prac01-01 AccessDokumen15 halamanPrac01-01 AccessJuan Carlos Calo Levano MagallanesBelum ada peringkat
- Tipos de HackersDokumen2 halamanTipos de Hackersjose_90Belum ada peringkat
- Aprenda A Programar Macros en OpenOfficeDokumen538 halamanAprenda A Programar Macros en OpenOfficeJuan Carlos Guartasaca Ordóñez100% (8)
- Ejercicio Complejo de RSA NO ExamenDokumen3 halamanEjercicio Complejo de RSA NO ExamenlinaBelum ada peringkat
- TECSUPDokumen23 halamanTECSUPJhonatan Cano DominguezBelum ada peringkat
- Raptor 1 1Dokumen36 halamanRaptor 1 1Joseph ZavaletaBelum ada peringkat
- Reporte JavaScript EjemplosDokumen16 halamanReporte JavaScript EjemplosLaloo MoolinaBelum ada peringkat
- Lenguaje C Teoria - UTNRDokumen80 halamanLenguaje C Teoria - UTNRdestructor85100% (5)
- Clase 1Dokumen14 halamanClase 1kamilolopezBelum ada peringkat
- TimerDokumen6 halamanTimerjuanperezsoftwareBelum ada peringkat
- ROB 002 Arduino ProgramaDokumen7 halamanROB 002 Arduino ProgramaDiego Muñoz CeaBelum ada peringkat
- Diez Trucos para Acelerar Tu PC DrásticamenteDokumen12 halamanDiez Trucos para Acelerar Tu PC DrásticamenteAmbrosio Nava GuadarramaBelum ada peringkat
- Actividad WireframesDokumen4 halamanActividad Wireframesdavid castroBelum ada peringkat
- Enunciado Ejercicios WebDokumen12 halamanEnunciado Ejercicios WebDoris AcháBelum ada peringkat