NAT em CPEs Cisco
Diunggah oleh
api-3709551Deskripsi Asli:
Judul Asli
Hak Cipta
Format Tersedia
Bagikan dokumen Ini
Apakah menurut Anda dokumen ini bermanfaat?
Apakah konten ini tidak pantas?
Laporkan Dokumen IniHak Cipta:
Format Tersedia
NAT em CPEs Cisco
Diunggah oleh
api-3709551Hak Cipta:
Format Tersedia
Cisco - Configuring Network Address Translation: Getting Started
Configuring Network Address Translation:
Getting Started
Contents
Introduction
Prerequisites
Requirements
Components Used
Conventions
Quick Start Steps for Configuring and Deploying NAT
Defining NAT Inside and Outside Interfaces
Example: Allowing Internal Users to Access the Internet
Configuring NAT to Allow Internal Users to Access the Internet
Configuring NAT to Allow Internal Users to Access the Internet Using Overloading
Example: Allowing the Internet to Access Internal Devices
Configuring NAT to Allow the Internet to Access Internal Devices
Example: Redirecting TCP Traffic to Another TCP Port or Address
Configuring NAT to Redirect TCP Traffic to Another TCP Port or Address
Example: Using NAT During a Network Transition
Configuring NAT for Use During a Network Transition
Example: Using NAT in Overlapping Networks
Verifying NAT Operation
Conclusion
NetPro Discussion Forums - Featured Conversations
Related Information
Introduction
This document explains configuring Network Address Translation (NAT) on a Cisco router for use in common
network scenarios. The target audience of this document is first time NAT users.
Note: In this document, when the internet, or an internet device is referred to, it means a device on any external
network.
file:///D|/paws/13772/12.html (1 of 12) [8/2/2004 3:37:24 PM]
Cisco - Configuring Network Address Translation: Getting Started
Prerequisites
Requirements
This document requires a basic knowledge of the terms used in connection with NAT. Some of the definitions
can be found in NAT: Local and Global Definitions.
Components Used
The information in this document is based on the software and hardware versions below.
● Cisco 2500 Series Routers
● Cisco IOS® Software Release 12.2 (10b)
The information presented in this document was created from devices in a specific lab environment. All of the
devices used in this document started with a cleared (default) configuration. If you are working in a live
network, ensure that you understand the potential impact of any command before using it.
Conventions
For more information on document conventions, see the Cisco Technical Tips Conventions.
Quick Start Steps for Configuring and Deploying NAT
When configuring NAT it is sometimes difficult to know where to begin, especially if you're new to NAT. These
steps guide you to define what you want NAT to do and how to configure it:
1. Define NAT inside and outside interfaces.
❍ Do users exist off multiple interfaces?
❍ Are there multiple interfaces going to the internet?
2. Define what you're trying to accomplish with NAT.
❍ Are you trying to allow internal users to access the internet?
❍ Are you trying to allow the internet to access internal devices (such as a mail server or web server)?
❍ Are you trying to redirect TCP traffic to another TCP port or address?
❍ Are you using NAT during a network transition (for example, you changed a server's IP address and
until you can update all the clients you want the non-updated clients to be able to access the server
using the original IP address as well as allow the updated clients to access the server using the new
address)?
❍ Are you using NAT to allow overlapping networks to communicate?
3. Configure NAT in order to accomplish what you defined above. Based on what you defined in step 2, you
need determine which of the following features to use:
file:///D|/paws/13772/12.html (2 of 12) [8/2/2004 3:37:24 PM]
Cisco - Configuring Network Address Translation: Getting Started
❍ Static NAT
❍ Dynamic NAT
❍ Overloading
❍ Any combination of the above
4. Verify the NAT operation.
Each of the following NAT examples guides you through steps 1 through 3 of the Quick Start Steps above.
These examples describe some common scenarios in which Cisco recommends you deploy NAT.
Defining NAT Inside and Outside Interfaces
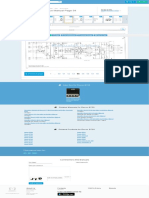
The first step in deploying NAT is to define NAT inside and outside interfaces. You may find it easiest to define
your internal network as inside, and the external network as outside. However, the terms internal and external
are subject to arbitration as well. The figure below shows an example of this.
Example: Allowing Internal Users to Access the
Internet
You may want to allow internal users to access the internet, but you may not have enough valid addresses to
accommodate everyone. If all communication with devices in the internet will originate from the internal
devices, you need a single valid address or a pool of valid addresses.
The figure below shows a simple network diagram with the router interfaces defined as inside and outside:
file:///D|/paws/13772/12.html (3 of 12) [8/2/2004 3:37:24 PM]
Cisco - Configuring Network Address Translation: Getting Started
In this example, we want NAT to allow certain devices (the first 31 from each subnet) on the inside to originate
communication with devices on the outside by translating their invalid address to a valid address or pool of
addresses. The pool has been defined as the range of addresses 172.16.10.1 through 172.16.10.63.
Now you are ready to configure NAT. In order to accomplish what is defined above, use dynamic NAT. With
dynamic NAT, the translation table in the router is initially empty and gets populated once traffic that needs to
be translated passes through the router. (As opposed to static NAT, where a translation is statically configured
and is placed in the translation table without the need for any traffic.)
In this example, we can configure NAT to translate each of the inside devices to a unique valid address, or to
translate each of the inside devices to the same valid address. This second method is known as overloading. An
example of how to configure each method is given below.
Configuring NAT to Allow Internal Users to Access the Internet
NAT Router
interface ethernet 0
ip address 10.10.10.1 255.255.255.0
ip nat inside
!--- Defines Ethernet 0 with an IP address and as a NAT inside interface.
interface ethernet 1
ip address 10.10.20.1 255.255.255.0
ip nat inside
!--- Defines Ethernet 1 with an IP address and as a NAT inside interface.
file:///D|/paws/13772/12.html (4 of 12) [8/2/2004 3:37:25 PM]
Cisco - Configuring Network Address Translation: Getting Started
interface serial 0
ip address 172.16.10.64 255.255.255.0
ip nat outside
!--- Defines serial 0 with an IP address and as a NAT outside interface.
ip nat pool no-overload 172.16.10.1 172.16.10.63 prefix 24
!
!--- Defines a NAT pool named no-overload with a range of addresses
!--- 172.16.10.1 - 172.16.10.63.
ip nat inside source list 7 pool no-overload
!
!
!--- Indicates that any packets received on the inside interface that
!--- are permitted by access-list 7
!--- will have the source address translated to an address out of the
!--- NAT pool "no-overload".
access-list 7 permit 10.10.10.0 0.0.0.31
access-list 7 permit 10.10.20.0 0.0.0.31
!--- Access-list 7 permits packets with source addresses ranging from
!--- 10.10.10.0 through 10.10.10.31 and 10.10.20.0 through 10.10.20.31.
Note: Cisco highly recommends that you do not configure access lists referenced by NAT commands with
permit any. Using permit any can result in NAT consuming too many router resources which can cause
network problems.
Notice in the above configuration that only the first 32 addresses from subnet 10.10.10.0 and the first 32
addresses from subnet 10.10.20.0 are permitted by access-list 7. Therefore, only these source addresses are
translated. There may be other devices with other addresses on the inside network, but these won't be translated.
The final step is to verify that NAT is operating as intended.
Configuring NAT to Allow Internal Users to Access the Internet Using
Overloading
NAT Router
file:///D|/paws/13772/12.html (5 of 12) [8/2/2004 3:37:25 PM]
Cisco - Configuring Network Address Translation: Getting Started
interface ethernet 0
ip address 10.10.10.1 255.255.255.0
ip nat inside
!--- Defines Ethernet 0 with an IP address and as a NAT inside interface.
interface ethernet 1
ip address 10.10.20.1 255.255.255.0
ip nat inside
!--- Defines Ethernet 1 with an IP address and as a NAT inside interface.
interface serial 0
ip address 172.16.10.64 255.255.255.0
ip nat outside
!--- Defines serial 0 with an IP address and as a NAT outside interface.
ip nat pool ovrld 172.16.10.1 172.16.10.1 prefix 24
!
!--- Defines a NAT pool named ovrld with a range of a single IP
!--- address, 172.16.10.1.
ip nat inside source list 7 pool ovrld overload
!
!
!
!
!--- Indicates that any packets received on the inside interface that
!--- are permitted by access-list 7 will have the source address
!--- translated to an address out of the NAT pool named ovrld.
!--- Translations will be overloaded which will allow multiple inside
!--- devices to be translated to the same valid IP address.
access-list 7 permit 10.10.10.0 0.0.0.31
access-list 7 permit 10.10.20.0 0.0.0.31
!--- Access-list 7 permits packets with source addresses ranging from
!--- 10.10.10.0 through 10.10.10.31 and 10.10.20.0 through 10.10.20.31.
Note in the second configuration above, the NAT pool "ovrld"only has a range of one address. The keyword
file:///D|/paws/13772/12.html (6 of 12) [8/2/2004 3:37:25 PM]
Cisco - Configuring Network Address Translation: Getting Started
overload used in the ip nat inside source list 7 pool ovrld overload command allows NAT to translate
multiple inside devices to the single address in the pool.
Another variation of this command is ip nat inside source list 7 interface serial 0 overload, which configures
NAT to overload on the address that is assigned to the serial 0 interface.
When overloading is configured, the router maintains enough information from higher-level protocols (for
example, TCP or UDP port numbers) to translate the global address back to the correct local address. For
definitions of global and local address, refer to NAT: Global and Local Definitions.
The final step is to verify that NAT is operating as intended.
Example: Allowing the Internet to Access Internal
Devices
You may need internal devices to exchange information with devices on the internet, where the communication
is initiated from the internet devices, for example, email. It's typical for devices on the internet to send email to a
mail server that resides on the internal network.
Configuring NAT to Allow the Internet to Access Internal Devices
In this example, we first define the NAT inside and outside interfaces, as shown in the network diagram above.
Second, we define that we want users on the inside to be able to originate communication with the outside.
Devices on the outside should be able to originate communication with only the mail server on the inside.
The third step is to configure NAT. To accomplish what we've defined, we can configure static and dynamic
NAT together. For more information on how to configure this example, refer to Configuring Static and Dynamic
NAT Simultaneously.
The final step is to verify that NAT is operating as intended.
file:///D|/paws/13772/12.html (7 of 12) [8/2/2004 3:37:25 PM]
Cisco - Configuring Network Address Translation: Getting Started
Example: Redirecting TCP Traffic to Another TCP Port
or Address
Having a web server on the internal network is another example of when it may be necessary for devices on the
internet to initiate communication with internal devices. In some cases the internal web server may be
configured to listen for web traffic on a TCP port other than port 80. For example, the internal web server may
be configured to listen to TCP port 8080. In this case, you can use NAT to redirect traffic destined to TCP port
80 to TCP port 8080.
After you define the interfaces as shown in the network diagram above, you may decide that you want NAT to
redirect packets from the outside destined for 172.16.10.8:80 to 172.16.10.8:8080. You can use a static nat
command to translate the TCP port number to achieve this. A sample configuration is shown below.
Configuring NAT to Redirect TCP Traffic to Another TCP Port or Address
NAT Router
interface ethernet 0
ip address 172.16.10.1 255.255.255.0
ip nat inside
!--- Defines Ethernet 0 with an IP address and as a NAT inside interface.
interface serial 0
ip address 200.200.200.5 255.255.255.252
ip nat outside
!--- Defines serial 0 with an IP address and as a NAT outside interface.
file:///D|/paws/13772/12.html (8 of 12) [8/2/2004 3:37:25 PM]
Cisco - Configuring Network Address Translation: Getting Started
ip nat inside source static tcp 172.16.10.8 8080 172.16.10.8 80
!--- Static NAT command that states any packet received in the inside
!--- interface with a source IP address of 172.16.10.8:8080 will be
!--- translated to 172.16.10.8:80.
Note that the configuration description for the static NAT command indicates any packet received in the inside
interface with a source address of 172.16.10.8:8080 will be translated to 172.16.10.8:80. This also implies that
any packet received on the outside interface with a destination address of 172.16.10.8:80 will have the
destination translated to 172.16.10.8:8080.
The final step is to verify that NAT is operating as intended.
Example: Using NAT During a Network Transition
Deploying NAT is useful when you need to readdress devices on the network or when you're replacing one
device with another. For instance, if all devices in the network use a particular server and this server needs to be
replaced with a new one that has a new IP address, reconfiguring all the network devices to use the new server
address will take some time. In the meantime, you can use NAT to configure the devices using the old address to
translate their packets to communicate with the new server.
Once you have defined the NAT interfaces as shown above, you may decide that you want NAT to allow
packets from the outside destined for the old server address (172.16.10.8) to be translated and sent to the new
server address. Note that the new server is on another LAN, and devices on this LAN or any devices reachable
file:///D|/paws/13772/12.html (9 of 12) [8/2/2004 3:37:25 PM]
Cisco - Configuring Network Address Translation: Getting Started
through this LAN (devices on the inside part of the network), should be configured to use the new server's IP
address if possible.
You can use static NAT to accomplish what you need. A sample configuration is shown below.
Configuring NAT for Use During a Network Transition
NAT Router
interface ethernet 0
ip address 172.16.10.1 255.255.255.0
ip nat outside
!--- Defines Ethernet 0 with an IP address and as a NAT outside interface.
interface ethernet 1
ip address 172.16.50.1 255.255.255.0
ip nat inside
!--- Defines Ethernet 1 with an IP address and as a NAT inside interface.
interface serial 0
ip address 200.200.200.5 255.255.255.252
!--- Defines serial 0 with an IP address. This interface is not
!--- participating in NAT.
ip nat inside source static 172.16.50.8 172.16.10.8
!--- States that any packet received on the inside interface with a
!--- source IP address of 172.16.50.8 will be translated to 172.16.10.8.
Note that the inside source NAT command in this example also implies that packets received on the outside
interface with a destination address of 172.16.10.8 will have the destination address translated to 172.16.50.8.
The final step is to verify that NAT is operating as intended.
Example: Using NAT in Overlapping Networks
Overlapping networks result when you assign IP addresses to internal devices that are already being used by
other devices within the internet. Overlapping networks also result when two companies, both of whom use RFC
1918 IP addresses in their networks, merge. These two networks need to communicate, preferably without
having to readdress all their devices. Refer to Using NAT in Overlapping Networks for more information about
configuring NAT for this purpose.
file:///D|/paws/13772/12.html (10 of 12) [8/2/2004 3:37:25 PM]
Cisco - Configuring Network Address Translation: Getting Started
Verifying NAT Operation
Once you've configured NAT, verify that it is operating as expected. You can do this in a number of ways: using
a network analyzer, show commands, or debug commands. For a detailed example of NAT verification, refer to
Verifying NAT Operation and Basic NAT Troubleshooting.
Conclusion
The examples in this document demonstrate quick start steps can help you configure and deploy NAT. These
quick start steps include:
1. Defining NAT inside and outside interfaces.
2. Defining what you are trying to accomplish with NAT.
3. Configuring NAT in order to accomplish what you defined in Step 2.
4. Verifying the NAT operation.
In each of the examples above, various forms of the ip nat inside command were used. You can also use the ip
nat outside command to accomplish the same objectives, keeping in mind the NAT order of operations. For
configuration examples using the ip nat outside commands, refer to Sample Configuration Using the ip nat
outside source list Command and Sample Configuration Using the ip nat outside source static Command.
The examples above also demonstrated the following:
Command Action
● Translates the source
of IP packets that are
traveling inside to
outside.
ip nat inside source ● Translates the
destination of the IP
packets that are
traveling outside to
inside.
● Translates the source
of the IP packets that
are traveling outside
to inside.
ip nat outside source ● Translates the
destination of the IP
packets that are
traveling inside to
outside.
file:///D|/paws/13772/12.html (11 of 12) [8/2/2004 3:37:25 PM]
Cisco - Configuring Network Address Translation: Getting Started
NetPro Discussion Forums - Featured Conversations
Networking Professionals Connection is a forum for networking professionals to share questions, suggestions,
and information about networking solutions, products, and technologies. The featured links are some of the most
recent conversations available in this technology.
NetPro Discussion Forums - Featured Conversations for RP
Service Providers: MPLS
Virtual Private Networks: Services
Virtual Private Networks: Security
Related Information
● NAT Support Page
● IP Routed Protocols Support Page
● IP Routing Support Page
● How NAT Works
● NAT Order of Operation
● Frequently Asked Questions about Cisco IOS NAT
● Technical Support - Cisco Systems
All contents are Copyright © 1992-2004 Cisco Systems, Inc. All rights reserved. Important Notices and Privacy Statement.
file:///D|/paws/13772/12.html (12 of 12) [8/2/2004 3:37:25 PM]
Anda mungkin juga menyukai
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeDari EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifePenilaian: 4 dari 5 bintang4/5 (5794)
- The Little Book of Hygge: Danish Secrets to Happy LivingDari EverandThe Little Book of Hygge: Danish Secrets to Happy LivingPenilaian: 3.5 dari 5 bintang3.5/5 (400)
- Ajax PHP Code Chapter02 Ajax Foundations Async AsyncDokumen1 halamanAjax PHP Code Chapter02 Ajax Foundations Async Asyncapi-3709551Belum ada peringkat
- User-Guide - Ethereal PDFDokumen454 halamanUser-Guide - Ethereal PDFLeonardo BroedelBelum ada peringkat
- Ajax PHP Code 1825 AppB FinalDokumen10 halamanAjax PHP Code 1825 AppB Finalapi-3709551Belum ada peringkat
- Ajax IntroDokumen10 halamanAjax Introapi-3709551Belum ada peringkat
- Successful Solaris Performance TuningDokumen5 halamanSuccessful Solaris Performance Tuningapi-3709551100% (2)
- Twlinvwinv 2Dokumen33 halamanTwlinvwinv 2api-3709551Belum ada peringkat
- Simple Apache and Tomcat HOWTODokumen13 halamanSimple Apache and Tomcat HOWTOapi-3709551Belum ada peringkat
- SDH Pocket Guide - ActernaDokumen76 halamanSDH Pocket Guide - Acternaapi-3709551100% (5)
- MicrosoftDokumen129 halamanMicrosoftapi-3709551Belum ada peringkat
- Windows XP Tips CollectionDokumen19 halamanWindows XP Tips Collectionnouman.abbasBelum ada peringkat
- Microsoft Windows Server 2003 Security GuideDokumen290 halamanMicrosoft Windows Server 2003 Security Guidevitalik095Belum ada peringkat
- (eBook-PDF) - Hacking Cisco RoutersDokumen11 halaman(eBook-PDF) - Hacking Cisco RoutersilecBelum ada peringkat
- Career Press - Money Mastery - Spending - PlannerDokumen2 halamanCareer Press - Money Mastery - Spending - Plannerapi-3709551Belum ada peringkat
- Shoe Dog: A Memoir by the Creator of NikeDari EverandShoe Dog: A Memoir by the Creator of NikePenilaian: 4.5 dari 5 bintang4.5/5 (537)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceDari EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RacePenilaian: 4 dari 5 bintang4/5 (895)
- The Yellow House: A Memoir (2019 National Book Award Winner)Dari EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Penilaian: 4 dari 5 bintang4/5 (98)
- The Emperor of All Maladies: A Biography of CancerDari EverandThe Emperor of All Maladies: A Biography of CancerPenilaian: 4.5 dari 5 bintang4.5/5 (271)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryDari EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryPenilaian: 3.5 dari 5 bintang3.5/5 (231)
- Never Split the Difference: Negotiating As If Your Life Depended On ItDari EverandNever Split the Difference: Negotiating As If Your Life Depended On ItPenilaian: 4.5 dari 5 bintang4.5/5 (838)
- Grit: The Power of Passion and PerseveranceDari EverandGrit: The Power of Passion and PerseverancePenilaian: 4 dari 5 bintang4/5 (588)
- On Fire: The (Burning) Case for a Green New DealDari EverandOn Fire: The (Burning) Case for a Green New DealPenilaian: 4 dari 5 bintang4/5 (73)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureDari EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FuturePenilaian: 4.5 dari 5 bintang4.5/5 (474)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaDari EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaPenilaian: 4.5 dari 5 bintang4.5/5 (266)
- The Unwinding: An Inner History of the New AmericaDari EverandThe Unwinding: An Inner History of the New AmericaPenilaian: 4 dari 5 bintang4/5 (45)
- Team of Rivals: The Political Genius of Abraham LincolnDari EverandTeam of Rivals: The Political Genius of Abraham LincolnPenilaian: 4.5 dari 5 bintang4.5/5 (234)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyDari EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyPenilaian: 3.5 dari 5 bintang3.5/5 (2259)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreDari EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You ArePenilaian: 4 dari 5 bintang4/5 (1090)
- Rise of ISIS: A Threat We Can't IgnoreDari EverandRise of ISIS: A Threat We Can't IgnorePenilaian: 3.5 dari 5 bintang3.5/5 (137)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersDari EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersPenilaian: 4.5 dari 5 bintang4.5/5 (344)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)Dari EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Penilaian: 4.5 dari 5 bintang4.5/5 (121)
- Her Body and Other Parties: StoriesDari EverandHer Body and Other Parties: StoriesPenilaian: 4 dari 5 bintang4/5 (821)
- Analysis of Digital IndiaDokumen12 halamanAnalysis of Digital IndiaThe United IndianBelum ada peringkat
- Offline Gold Lost Forum ThreadDokumen44 halamanOffline Gold Lost Forum ThreadJavaid IqbalBelum ada peringkat
- Brkaci 3503Dokumen89 halamanBrkaci 3503Rakesh KumarBelum ada peringkat
- Content Distribution NetworksDokumen38 halamanContent Distribution Networksমোহাম্মদ রাহাত হাসানBelum ada peringkat
- CMS Student Portal - User Manual For StudentsDokumen17 halamanCMS Student Portal - User Manual For StudentsKatyu MashashiBelum ada peringkat
- Fortianalyzer - 400B: Centralized Management Solutions For Fortinet SystemsDokumen2 halamanFortianalyzer - 400B: Centralized Management Solutions For Fortinet SystemseppoxroBelum ada peringkat
- MessageDokumen366 halamanMessage37 Minh Trí 8/6Belum ada peringkat
- FortiManager 7.0.7 Administration GuideDokumen796 halamanFortiManager 7.0.7 Administration Guidemhoudine hassaneBelum ada peringkat
- Cascading Style Sheets (CSS) : September 1, 2021Dokumen32 halamanCascading Style Sheets (CSS) : September 1, 2021Pratit Raj GiriBelum ada peringkat
- Empowerment Diagnostic TestDokumen15 halamanEmpowerment Diagnostic TestRutchie Abanto100% (1)
- Part202 CommunicationsOverTCPIPV1.03Dokumen49 halamanPart202 CommunicationsOverTCPIPV1.03toovBelum ada peringkat
- IMS: Powering The 21st CenturyDokumen70 halamanIMS: Powering The 21st CenturyvgrynyukBelum ada peringkat
- User Manual Acer Liquid X2Dokumen74 halamanUser Manual Acer Liquid X2Shogun Robert Deocariza AzarconBelum ada peringkat
- UntitledDokumen517 halamanUntitledDeboraBelum ada peringkat
- Sophos Firewall: How To Establish A Site-To-Site Ipsec VPN Connection Using Rsa KeysDokumen20 halamanSophos Firewall: How To Establish A Site-To-Site Ipsec VPN Connection Using Rsa KeysjasjusrBelum ada peringkat
- Configuracion de Routers en CiscoDokumen12 halamanConfiguracion de Routers en CiscoWomar Barrios LPBelum ada peringkat
- System Check Results - Program WorkshopDokumen3 halamanSystem Check Results - Program Workshopubaya tasBelum ada peringkat
- ProductSheet MDM2510 IP SatelliteModemDokumen2 halamanProductSheet MDM2510 IP SatelliteModemq1w2e3r4t5r4e3w2Belum ada peringkat
- Deploying Cisco Service Provider Network Routing: SPROUTE v1.01Dokumen20 halamanDeploying Cisco Service Provider Network Routing: SPROUTE v1.01Alan Jordan Jimenez UlloaBelum ada peringkat
- Interactive Worksheet - SEO Authority Audit-1Dokumen9 halamanInteractive Worksheet - SEO Authority Audit-1Bhavyata ChavdaBelum ada peringkat
- Revox B750 Service Manual (Page 54 of 62)Dokumen1 halamanRevox B750 Service Manual (Page 54 of 62)Сергей ТаировBelum ada peringkat
- Class X (Computer)Dokumen2 halamanClass X (Computer)RsBelum ada peringkat
- Eastland Badminton Association - Hardware and Software QuoteDokumen10 halamanEastland Badminton Association - Hardware and Software QuoteLinda WhiteBelum ada peringkat
- Unit Iv Transport Layer Overview of Transport LayerDokumen27 halamanUnit Iv Transport Layer Overview of Transport LayerNavin DasBelum ada peringkat
- A Guide To Effective Internet Searching / CIT Library Support ServicesDokumen3 halamanA Guide To Effective Internet Searching / CIT Library Support ServicesFridah KikiBelum ada peringkat
- Class 12 Complete Book of Informatics PracticesDokumen220 halamanClass 12 Complete Book of Informatics PracticesSuraj RajBelum ada peringkat
- Humans Emerging Beyond Universe With MetaverseDokumen9 halamanHumans Emerging Beyond Universe With MetaverseIJRASETPublicationsBelum ada peringkat
- JIR-12.a LDDokumen48 halamanJIR-12.a LDAnderson OlivierBelum ada peringkat
- Harshit Kumar ReportDokumen60 halamanHarshit Kumar ReportHarshit RajBelum ada peringkat
- FortiOS 7.2.5 Administration GuideDokumen3.117 halamanFortiOS 7.2.5 Administration GuideJosé PabloBelum ada peringkat