Security Protocols
Diunggah oleh
api-3701346Deskripsi Asli:
Judul Asli
Hak Cipta
Format Tersedia
Bagikan dokumen Ini
Apakah menurut Anda dokumen ini bermanfaat?
Apakah konten ini tidak pantas?
Laporkan Dokumen IniHak Cipta:
Format Tersedia
Security Protocols
Diunggah oleh
api-3701346Hak Cipta:
Format Tersedia
Security Protocols Overview An RSA Data Security Brief
SSL & TLS
Secure Socket Layer & Transport Layer Security
Secure Sockets Layer (SSL) is the that do not necessarily need to be
Internet security protocol for on the same secure network.
point-to-point connections. It pro- Where SSL secures two applica-
vides protection against eaves- tions, IPSec secures an entire net-
dropping, tampering, and forgery. work.
Clients and servers are able to au-
thenticate each other and to estab- Applications
lish a secure link, or “pipe,” across SSL can be used in any situation
the Internet or Intranets to protect where a link between two comput-
the information transmitted. ers or applications needs to be pro-
tected. The following are just a few
The Need for SSL of the real-world, practical appli-
With the growth of the Internet cations of SSL & TLS:
and digital data transmission, many applications need to se-
curely transmit data to remote applications and computers. • Client/Server Systems
SSL was designed to solve this problem in an open standard.
SSL in the browser is not enough to secure most systems.
Systems such as secure database access, or remote object
SSL is analogous to a secure “telephone call” between two
systems such as CORBA, can all be securely improved
computers on any network including the Internet. In SSL, a
using SSL. Other applications include redirection of se-
connection is made, parties authenticated, and data securely
cure connections such as proxy servers, secure Webserver
exchanged. The latest enhancement of SSL is called Trans-
plug-ins, and Java “Servlets.”
port Layer Security (TLS).
• Financial
Algorithms Banks and financial companies can use SSL to develop
In applications using SSL, the confidentiality of information remote banking programs that employ strong cryptogra-
is ensured using strong encryption technologies. Through phy. Some applications that operate outside of the Web
the use of digital certificates, SSL provides the transparent browser allow customers to check account balances, trans-
authentication of servers and, optionally, clients as well. SSL fer funds, or even apply for a new mortgage without
uses the RSA algorithm as the algorithm to enable security speaking to a loan officer.
using digital signatures and digital enveloping. For very fast • Information Systems
encryption and decryption of data for transmission after an
SSL connection has been established, the RC4® algorithm is Many systems employ SSL to create remote access and
the preferred algorithm. Other algorithms are available in administration applications. Using SSL, it is easy to cre-
the SSL specification as well. ate secure remote access and control systems for manage-
ment of system activity and resources.
Based on the strong cryptography in SSL, users have confi- • Travel Industry
dence that their information is confidential, authentic, and SSL can be used to create online reservation systems and
original during a network connection. secure information transfer. Organizations who build SSL-
enabled applications can allow their customers to securely
Why Isn’t SSL in the Browser Enough? book reservations online without ever speaking to a sales
While SSL is used on the Web for many applications, situa- person.
tions often demand that SSL in the browser is not enough.
For example, if one end of the connection is not SSL-enabled RSA Data Security Products that Support
or Web-enabled, then tools are needed to build SSL into the
SSL & TLS
application. Other situations require that applications have
more control over connections including the selection of ci-
pher suites and key negotiation. Developers who use the
SSL contained in the Web browser have little control over
SSL performance and operation.
SSL versus IPSec
IPSec secures the low-level network packets in order to cre-
ate a secure network of computers over insecure channels,
including the Internet and leased lines. SSL operates at the
transport layer, abstracted from the network layer where
IPSec operates. SSL operates between any two applications
Security Protocols Overview An RSA Data Security Brief
S/MIME
Secure Multipurpose Internet Mail Extensions
S/MIME is the electronic messaging standard that enables e- • Content Delivery
business by addressing the important issues of data privacy S/MIME can be used to implement electronic bill present-
and authenticity. S/MIME uses public-key encryption tech- ment and payment online. Customers using applications
nology to protect messages from unauthorized interception based on S/MIME can securely receive and pay their bills
and forgery. without any stamps. Other applications include online
software sales and subscription services.
An S/MIME-enabled application is analogous to
a secure piece of postal mail travelling between
two locations. The S/MIME protocol guar-
antees the secure transmission, storage,
authentication, and forwarding of secret
data.
The Need for S/MIME
Protocols such as SSL and TLS provide
security at the application level for com-
munication between hosts on a public
network. Other protocols, such as IPSec
and others, maintain the security of low-level
network communications. However, none of
these protocols handle situations where data
needs to be securely stored, transmitted, and for-
warded. In this area of use, S/MIME is the stan-
dard.
S/MIME versus SSL
• Healthcare
Where SSL secures a connection between a client and a server
over an insecure network, S/MIME is used to secure mes- Healthcare providers can use S/MIME to create secure
sages between users, applications, and computers. patient records and health claims. Providers can build
S/MIME enabled applications that remove the overhead
Algorithms of patient record management inherent in antiquated
S/MIME based on the RSA algorithm for digital signatures record storage techniques.
and digital envelopes. The RC2®, DES, and Triple DES algo-
rithms are utilized for symmetric encryption. For hashing,
S/MIME is based on the MD5™ and SHA1 hash algorithms. RSA Data Security Products that Support
S/MIME
Applications
S/MIME is applicable to any situation in which data must be
securely transferred, stored, forwarded, and authenticated.
The following are just a few of the real-world, practical ap-
plications of S/MIME:
• Electronic Data Interchange
S/MIME is used as a basis for EDI-INT, the Internet stan-
dard for EDI over the Internet. These applications include
digital signatures on contracts and secure data interchange
over the Internet.
• Financial Messaging
Organizations can use S/MIME to store and transfer bank
statements and financial forms between computers. Other
uses include transfer of stock trades, communication of
brokerage statements, and mortgage payment services.
Security Protocols Overview An RSA Data Security Brief
IPSec
IP Security Protocol
IPSec is the leading standard for cryptographically based used to create secure networks over insecure means of
authentication, integrity, and confidentiality services at the transmission such as the Internet. Using VPNs, compa-
IP datagram layer. IPSec comprises a basis for interoperably nies can save money in terms of the costs of leased lines
secured host-to-host pipes, encapsulated tunnels, and Vir- while maintaining the confidentiality of corporate infor-
tual Private Networks (VPNs), thus providing protection for mation.
client protocols residing above the IP layer. • Remote Access Software and Hardware
Remote access software based upon the IPSec standard
IPSec ensures that the low-level IP packets that are continu-
provides enterprises with secure access to their network
ously transferred between computers on a secure network
functions. Remote access hardware provides another level
are unaltered, authentic, and private.
of security not found in software enabling remote access
The Need for IPSec to the network resources.
At the IP layer, computers on a network communicate by rout- • Firewall Products
ing datagram “packets.” These datagrams contain data, des- Firewall products can easily incorporate IPSec to create
tination addresses, source addresses, and other information. secure VPN network tunneling. These products allow
In a conventional network configuration such as corporate corporations to easily create secure and cost-effective links
local area networks (LANs), these datagrams are passed “in with their business partners and members of the enter-
the clear.” There is nothing to stop a malicious attacker from prise.
hijacking, forging, and modifying these packets.
Generally, physical security and Internet firewalls prevent RSA Data Security Products that Support
attackers from outside of the LAN from mounting an attack IPSec
on conventional networks. However, in situations such as
RSA BSAFE™ Crypto-C and RSA BSAFE™ Crypto-J are prod-
the Internet and any other unsecured network, there is little
ucts that provide the core cryptography needed to imple-
to stop an attacker from intercepting, forging, or modifying
ment IPSec and VPN systems.
datagram packets.
Corporations such as Cisco, Bay Networks, IBM, Raptor, and
Algorithms Secure Computing have all incorporated IPSec and the RSA
IPSec is based on the Diffie-Hellman and/or the RSA algo-
BSAFE™ Crypto-C or RSA BSAFE™ Crypto-J security compo-
rithms for key exchange. For symmetric encryption, the DES
nents into their products.
and Triple-DES algorithms are utilized. In situations where
greater security is required for encryption in IPSec, the RC5™
algorithm is commonly used. For hashing, the SHA1 hash
algorithm and MD5™ are used.
IPSec versus SSL
IPSec secures the low-level network packets in order to cre-
ate a secure network of computers over insecure channels,
including the Internet and leased lines. SSL operates at the
transport layer where they do not need to be located on the
same secure network, but are instead used to ensure security
between applications across an public network. Where SSL
secures two networked applications, IPSec secures an entire
network.
Applications
IPSec is applicable to any situation in which secure network
communication is desired over insecure networks such as
the Internet. The following are just a few of the practical,
real-word applications of IPSec:
• Virtual Private Network (VPN) Software and Hardware
Many organizations use the IPSec standard to build soft-
ware that enables Virtual Private Networks. This can be
Security Protocols Overview An RSA Data Security Brief
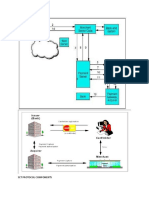
Security Protocols
A number of different security protocols have been introduced. The following table summarizes the most popular security
protocols and the RSA product that developers should use to implement them:
Protocol Summary Algorithms RSA Product
CDPD Standard designed to enable DH, RC4® BSAFE™ Crypto-C,
(Cellular Digital customers to send computer data BSAFE™ Crypto-J
Packet Data) over existing cellular networks.
DNSSEC Protocol for secure distributed name RSA, MD5™, BSAFE™ Crypto-C
(Domain Name System services such as hostname and DSA
Security Extensions) IP address lookup.
DOCSIS Cable modem standard for secure RSA, DES, RSA BSAFE™ Crypto-C
(Data Over Cable Service transmission of data with protection HMAC,
Interface Specification) from theft-of-service and denial-of- SHA1
service attacks and for protecting
the privacy of cable customers.
IEEE 802.11 Protocol standard for secure wireless RC4®, MD5™ RSA BSAFE™ Crypto-C,
Local Area Network products. RSA BSAFE™ Crypto-J
IPSec Standard for cryptographically- RSA, DH, RSA BSAFE™ Crypto-C,
(IP Security Protocol) based authentication, integrity, MD5™, DES, RSA BSAFE™ Crypto-J
and confidentiality services 3DES, SHA1
at the IP datagram layer.
PPTP Used to create Virtual Private RSA, DES RSA BSAFE™ Crypto-C
(Point-to-Point Network communication
Tunneling Protocol) across the Internet; works at
the IP Datagram layer.
SET Allows secure credit card RSA, SHA1, DES, Trintech’s S/PAY,
(Secure Electronic Transactions) transactions over the Internet. HMAC-SHA1 RSA BSAFE™ Crypto-C
S/MIME Guarantees the secure trans- RSA, DES, RSA BSAFE™ S/MIME-C
(Secure MIME) mission, storage, authentication, 3DES, RC2®,
and forwarding of secret data MD5™, SHA1
at the application level.
SSH Protocol that permits users secure RSA, RC5™, RSA BSAFE™ Crypto-C,
(Secure Shell) remote access over a network RC4®, RC2®, RSA BSAFE™ Crypto-J
from one computer to another. DES, 3DES
SSL & TLS Allows a “secure pipe” between RSA, RC4®, RSA BSAFE™ SSL-C,
(Secure Sockets Layer & any two applications for SHA1, MD5™, RSA BSAFE™ SSL-J
Transport Layer Security) secure transfer of data and 3DES, DES, DH
mutual authentication
Copyright © 1999 RSA Data Security, Inc. All rights reserved. RSA BSAFE , RC2, RC4, RC5, and MD5 are trademarks or registered trademarks of RSA Data Security, Inc.
All other trademarks are the property of their respective owners.
Anda mungkin juga menyukai
- 6th Central Pay Commission Salary CalculatorDokumen15 halaman6th Central Pay Commission Salary Calculatorrakhonde100% (436)
- Vedic Maths TutorialDokumen12 halamanVedic Maths TutorialNitin Jain100% (15)
- PALO+ALTO+INTERVIEW+QUESTIONS - (NETWORK+SECURITY) +WWW Imedita Com+Dokumen39 halamanPALO+ALTO+INTERVIEW+QUESTIONS - (NETWORK+SECURITY) +WWW Imedita Com+Mahmud AbdullahBelum ada peringkat
- Secure Socket Layer (SSL) : Divey Gupta Sunny Gajjar B.Tech-IV Computer Engg. NIT-SuratDokumen22 halamanSecure Socket Layer (SSL) : Divey Gupta Sunny Gajjar B.Tech-IV Computer Engg. NIT-SuratSunny Kishorbhai GajjarBelum ada peringkat
- Securing .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerDari EverandSecuring .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerBelum ada peringkat
- IPSECDokumen23 halamanIPSECAkhilendraBelum ada peringkat
- Threat Hunting With SplunkDokumen122 halamanThreat Hunting With SplunkJesus MoraBelum ada peringkat
- SSL and TLS: Privacy & IntegrityDokumen4 halamanSSL and TLS: Privacy & IntegrityVishesh TripathiBelum ada peringkat
- Iso - Iec A1 PDFDokumen12 halamanIso - Iec A1 PDFRushikaBelum ada peringkat
- Information Security Lecture 1Dokumen37 halamanInformation Security Lecture 1VershiyiLambertBelum ada peringkat
- A Quick Introduction To Tensor Analysis - R. SharipovDokumen47 halamanA Quick Introduction To Tensor Analysis - R. SharipovPhan Someta100% (2)
- CSCUDokumen1 halamanCSCUrinkesh gwalaniBelum ada peringkat
- Cybersecurity Case Study LabDokumen2 halamanCybersecurity Case Study LabSIPAMANDLA FLEKISI100% (1)
- Encrypted Threat Protection: White PaperDokumen7 halamanEncrypted Threat Protection: White PaperswsloanBelum ada peringkat
- Secure Networking 101 MACsec, IPsec, and SSL BasicsDokumen10 halamanSecure Networking 101 MACsec, IPsec, and SSL BasicsazertyBelum ada peringkat
- SSL Acceleration: Deployment Strategies For Enterprise SecurityDokumen8 halamanSSL Acceleration: Deployment Strategies For Enterprise SecurityMyOwnScribdAccountBelum ada peringkat
- SSL Visibility Appliance enDokumen4 halamanSSL Visibility Appliance enDebojit GoswamiBelum ada peringkat
- Secure Socket Layer: M S.Bhiogade Patni Computer Services, Mumbai, IndiaDokumen6 halamanSecure Socket Layer: M S.Bhiogade Patni Computer Services, Mumbai, Indiadidiey87Belum ada peringkat
- Network Security Unit 4Dokumen32 halamanNetwork Security Unit 4Satyam PandeyBelum ada peringkat
- Security in e - CommerceDokumen4 halamanSecurity in e - CommerceAlex T BinoyBelum ada peringkat
- SSL Decryption - Uncovering The New Infrastructure Blind Spot - Gigamon WhitepaperDokumen6 halamanSSL Decryption - Uncovering The New Infrastructure Blind Spot - Gigamon WhitepaperGigamonBelum ada peringkat
- InternetsecurityprotocolsDokumen30 halamanInternetsecurityprotocolsAvi SirikondaBelum ada peringkat
- W IPS VPN Vs SSL VPN: Hitepaper ECDokumen5 halamanW IPS VPN Vs SSL VPN: Hitepaper ECaldz1482Belum ada peringkat
- DiniDokumen20 halamanDiniiraj shaikhBelum ada peringkat
- Chapter 17Dokumen32 halamanChapter 17pravin_renold7435Belum ada peringkat
- Psycology 2Dokumen7 halamanPsycology 2Malik RohailBelum ada peringkat
- DocumentDokumen1 halamanDocumentHassan AhmadBelum ada peringkat
- SSL Offloading Relieves Server CPU LoadDokumen2 halamanSSL Offloading Relieves Server CPU Loadsyed_engrBelum ada peringkat
- Decryption Why Where and HowDokumen6 halamanDecryption Why Where and HowfanvantanBelum ada peringkat
- E-Commerce Security Best PracticesDokumen19 halamanE-Commerce Security Best PracticesNess Wadia College of Coomerce PuneBelum ada peringkat
- Web Security Threats and ApproachesDokumen24 halamanWeb Security Threats and ApproachesMohd FareeduddinBelum ada peringkat
- Symantec SSL Visibility Appliance: Data SheetDokumen6 halamanSymantec SSL Visibility Appliance: Data SheetDebojit GoswamiBelum ada peringkat
- Ipsec and SSL VPN Deployment Considerations: in This DocumentDokumen8 halamanIpsec and SSL VPN Deployment Considerations: in This DocumentGiorgos FotopoulosBelum ada peringkat
- Transport Layer Protection Cheat SheetDokumen6 halamanTransport Layer Protection Cheat SheetRoman PotapovBelum ada peringkat
- Network NotesDokumen16 halamanNetwork Notesboka987Belum ada peringkat
- TLS Encryption ProtocolDokumen19 halamanTLS Encryption ProtocolAbhiram SahuBelum ada peringkat
- Module - 1 Notes: Transport Level Security: Web Security Considerations, Secure Sockets Layer, TransportDokumen45 halamanModule - 1 Notes: Transport Level Security: Web Security Considerations, Secure Sockets Layer, Transportrushil prasadBelum ada peringkat
- U4 4 Secured Socket LayerDokumen22 halamanU4 4 Secured Socket LayerNeetishBelum ada peringkat
- Secure Data Exchange Via HSMDokumen3 halamanSecure Data Exchange Via HSMLayer7TechBelum ada peringkat
- Web Services Security Technologies and StandardsDokumen36 halamanWeb Services Security Technologies and StandardsvmeshalkinBelum ada peringkat
- Unit 4 - Presentation2Dokumen28 halamanUnit 4 - Presentation2parthjethva1407Belum ada peringkat
- BlueCoat Decrypting SSLDokumen15 halamanBlueCoat Decrypting SSLRichardBelum ada peringkat
- Network Security Protocols ExplainedDokumen35 halamanNetwork Security Protocols ExplainedHarsha GangwaniBelum ada peringkat
- NSC Unit - 3 - 221210 - 134942Dokumen29 halamanNSC Unit - 3 - 221210 - 134942SurenderBelum ada peringkat
- Sockets Layer (SSL) and The Follow-On (Subsequent) Internet Standard ofDokumen8 halamanSockets Layer (SSL) and The Follow-On (Subsequent) Internet Standard ofFazeelur RahmanBelum ada peringkat
- SecureSpan SOA Gateway Gateway & Software AGDokumen4 halamanSecureSpan SOA Gateway Gateway & Software AGLayer7TechBelum ada peringkat
- 165 TY B KenilSeminarDokumen30 halaman165 TY B KenilSeminarB K EnterpriseBelum ada peringkat
- Cryptographic Protocols For Secure Cloud Computing: S. A. Alhumrani and Jayaprakash KarDokumen10 halamanCryptographic Protocols For Secure Cloud Computing: S. A. Alhumrani and Jayaprakash KarWai ZinBelum ada peringkat
- CSS 4Dokumen20 halamanCSS 4Imran K DhanjiBelum ada peringkat
- Secure Socket Layer (SSL)Dokumen47 halamanSecure Socket Layer (SSL)Wasif ImranBelum ada peringkat
- VPN SecurityDokumen12 halamanVPN SecuritydondegBelum ada peringkat
- 5.3 Secure Socket Layer (SSL)Dokumen4 halaman5.3 Secure Socket Layer (SSL)Aryan PanchalBelum ada peringkat
- Web SecurityDokumen18 halamanWeb Securitykrii24u8Belum ada peringkat
- Web Security and ProtocolsDokumen35 halamanWeb Security and ProtocolsFarhan KhurshidBelum ada peringkat
- Is Cloud Computing There YetDokumen6 halamanIs Cloud Computing There YetMaximus CooperBelum ada peringkat
- Choosing A Cloud ProviderDokumen9 halamanChoosing A Cloud ProviderGabriel GiraldoBelum ada peringkat
- Chapter Two Fundamental of IS Web Services Security (WS Security)Dokumen7 halamanChapter Two Fundamental of IS Web Services Security (WS Security)Getnete degemuBelum ada peringkat
- SSL VPN For CLNDokumen29 halamanSSL VPN For CLNVJ SNGBelum ada peringkat
- SSL - Secure Sockets LayerDokumen15 halamanSSL - Secure Sockets Layerhareem100Belum ada peringkat
- IntroductionDokumen3 halamanIntroductionELDER LAGGAHBelum ada peringkat
- Secure Socket LayerDokumen14 halamanSecure Socket LayerbetoplapaBelum ada peringkat
- Workstation Hardware Is Computer System With High Performance Designed For A Single User Advanced Graphic CapabilitiesDokumen9 halamanWorkstation Hardware Is Computer System With High Performance Designed For A Single User Advanced Graphic CapabilitiesCustomer CUstomerBelum ada peringkat
- Strong Security On Eclipse Packet Node - OverviewDokumen2 halamanStrong Security On Eclipse Packet Node - OverviewSCgmailBelum ada peringkat
- Unit 5Dokumen26 halamanUnit 5raxit.janiBelum ada peringkat
- Web Security SSL and TLSDokumen22 halamanWeb Security SSL and TLSvice pyBelum ada peringkat
- Wireless Internet Security Full ReportDokumen26 halamanWireless Internet Security Full ReportRahul AhujaBelum ada peringkat
- Security Architecture of Cloud ComputingDokumen7 halamanSecurity Architecture of Cloud ComputingdeepiiitbhuBelum ada peringkat
- SSL - Secure Sockets LayerDokumen12 halamanSSL - Secure Sockets LayerAli. RaoBelum ada peringkat
- The Theory of Numbers, by Robert DDokumen85 halamanThe Theory of Numbers, by Robert Dapi-3701346Belum ada peringkat
- New Representations For The Madelung ConstantDokumen13 halamanNew Representations For The Madelung Constantapi-3701346Belum ada peringkat
- Computing The Generating Function of A Series Given Its First Few TermsDokumen6 halamanComputing The Generating Function of A Series Given Its First Few Termsapi-26401608Belum ada peringkat
- Yatra Aur YatreeDokumen3 halamanYatra Aur Yatreeapi-3702437Belum ada peringkat
- Random Generators and Normal NumbersDokumen29 halamanRandom Generators and Normal Numbersapi-26401608Belum ada peringkat
- The AES AlgorithmDokumen29 halamanThe AES Algorithmapi-3701346100% (2)
- Chaos and Random Number GenerationDokumen10 halamanChaos and Random Number GenerationRyan SullenbergerBelum ada peringkat
- Fuzzy Logic IntroductionDokumen9 halamanFuzzy Logic Introductionapi-3806146Belum ada peringkat
- Fuzzy Sets Type-2-Mendel Nns Connections 2003Dokumen4 halamanFuzzy Sets Type-2-Mendel Nns Connections 2003api-3701346Belum ada peringkat
- MadhushalaDokumen3 halamanMadhushalaPirated SoulBelum ada peringkat
- Computing A Glimpse of RandomnessDokumen16 halamanComputing A Glimpse of RandomnessRyan SullenbergerBelum ada peringkat
- Din Jaldi Jaldi Dhalta HaiDokumen1 halamanDin Jaldi Jaldi Dhalta Haiapi-3702437Belum ada peringkat
- Drawing Room Me inDokumen1 halamanDrawing Room Me inapi-3702437Belum ada peringkat
- Aaj Phir SeDokumen1 halamanAaj Phir Seapi-3702437Belum ada peringkat
- Jo Beet Gayee Wo Baat GayeeDokumen2 halamanJo Beet Gayee Wo Baat Gayeeapi-3702437Belum ada peringkat
- Lecture On CDokumen34 halamanLecture On Capi-3701346100% (2)
- Inter UnixDokumen48 halamanInter Unixapi-3701346Belum ada peringkat
- C++ Tutorial For C UsersDokumen56 halamanC++ Tutorial For C UsersKarthik TantriBelum ada peringkat
- DDR Memory TechnologyDokumen15 halamanDDR Memory Technologyapi-3701346100% (1)
- C++ From ScratchDokumen188 halamanC++ From ScratchFenil DesaiBelum ada peringkat
- CPU Decoder Ring - The Tech ReportDokumen7 halamanCPU Decoder Ring - The Tech ReportNahush BapatBelum ada peringkat
- C++ Programming Style GuidelinesDokumen28 halamanC++ Programming Style GuidelinesFenil DesaiBelum ada peringkat
- Linuxgl Quakeworld Mini HowDokumen31 halamanLinuxgl Quakeworld Mini Howapi-3701346Belum ada peringkat
- Computer QueriesDokumen116 halamanComputer Queriesapi-3840029100% (1)
- C++ Programming StyleDokumen6 halamanC++ Programming Styleapi-3701346Belum ada peringkat
- C Reference CardDokumen2 halamanC Reference CardGridmark100% (3)
- C Reference CardDokumen2 halamanC Reference CardGridmark100% (3)
- Security Basics Financial ApplicationsDokumen12 halamanSecurity Basics Financial ApplicationsJakoozi Kazuma100% (1)
- Evaluating Crime Prevention Strategies in LemeryDokumen6 halamanEvaluating Crime Prevention Strategies in LemeryLink SamantaBelum ada peringkat
- QTP Hackers - How To Decrypt Encrypted PasswordDokumen3 halamanQTP Hackers - How To Decrypt Encrypted Passwordapi-19840982Belum ada peringkat
- Employee attendance and delivery reportDokumen41 halamanEmployee attendance and delivery reportBFT FARMBelum ada peringkat
- My Resume 1567108557Dokumen1 halamanMy Resume 1567108557U n Eye OpticalsBelum ada peringkat
- Energy Reports: Yuchong Li Qinghui LiuDokumen11 halamanEnergy Reports: Yuchong Li Qinghui Liuchairul rachmanBelum ada peringkat
- Cryptpgrahy Simp TieDokumen3 halamanCryptpgrahy Simp TieArshiya BegumBelum ada peringkat
- Seminar PresentationDokumen16 halamanSeminar PresentationMUNABelum ada peringkat
- Week 7 AssignmentDokumen11 halamanWeek 7 Assignmentapi-414181025Belum ada peringkat
- WWW A2nacademy Com Course Ethical Hacking CourseDokumen17 halamanWWW A2nacademy Com Course Ethical Hacking Coursea2n academyBelum ada peringkat
- Hackers - Daniel Chabachevitch Jake Benlolo Jacob Cohen Adam GouldDokumen17 halamanHackers - Daniel Chabachevitch Jake Benlolo Jacob Cohen Adam Gouldapi-275924078Belum ada peringkat
- CEH Master BrochureDokumen14 halamanCEH Master Brochureahfuoahrf0384100% (2)
- Chapter 2 - Introduction Vulnerabilities, Threats and AttackDokumen23 halamanChapter 2 - Introduction Vulnerabilities, Threats and AttackPabbura_HatiBelum ada peringkat
- Digital envelopes and digital signatures: securing electronic mail with encryption and authenticationDokumen5 halamanDigital envelopes and digital signatures: securing electronic mail with encryption and authenticationThamolwan Chumni0% (1)
- Itu Botnet Mitigation ToolkitDokumen17 halamanItu Botnet Mitigation ToolkitTecnicoItcaBelum ada peringkat
- Cyber TerrorismDokumen20 halamanCyber TerrorismJane Omingo100% (1)
- Sap Netweaver As Java SecurityDokumen12 halamanSap Netweaver As Java SecuritySyedBelum ada peringkat
- CCNA Security FINAL and ChaptersDokumen70 halamanCCNA Security FINAL and Chaptersmegadrive007100% (1)
- Proxy Replacement - Green Light PresentationDokumen9 halamanProxy Replacement - Green Light PresentationPrasad KshirsagarBelum ada peringkat
- Biometric Security: Advantages DisadvantagesDokumen3 halamanBiometric Security: Advantages DisadvantagesFabriV9Belum ada peringkat
- Zero Trust Network Access-7.0-Architecture GuideDokumen20 halamanZero Trust Network Access-7.0-Architecture GuideNgo Van TruongBelum ada peringkat
- 3 ProtocolsDokumen174 halaman3 ProtocolsManuel Aleixo LeiriaBelum ada peringkat
- International Journal of Computer Engineering and ApplicationsDokumen7 halamanInternational Journal of Computer Engineering and ApplicationsrishithaBelum ada peringkat
- Form VPN Site-To-Site v.1.0Dokumen7 halamanForm VPN Site-To-Site v.1.0r35kiBelum ada peringkat
- Bug-Bounty Video Collection PDFDokumen12 halamanBug-Bounty Video Collection PDFimmaikkaa nodigalBelum ada peringkat