Assignment 3: Vivek Gupta
Diunggah oleh
vgvivekgupta2Deskripsi Asli:
Judul Asli
Hak Cipta
Format Tersedia
Bagikan dokumen Ini
Apakah menurut Anda dokumen ini bermanfaat?
Apakah konten ini tidak pantas?
Laporkan Dokumen IniHak Cipta:
Format Tersedia
Assignment 3: Vivek Gupta
Diunggah oleh
vgvivekgupta2Hak Cipta:
Format Tersedia
COMPUTER NETWORK
ASSIGNMENT 3
Vivek Gupta
CSE B 0922310108
[Type the abstract of the document here. The abstract is typically a short summary of the contents of the document. Type the abstract of the document here. The abstract is typically a short summary of the contents of the document.]
COMPUTER NETWORKS ASSINGMENT UNIT 3
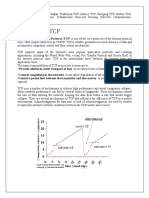
1. What is congestion? What are the methods to control congestion? Explain them. Ans) Congestion in a network may occur if the load on the network, the number of packets sent to the network, is greater than the capacity of the network , the numbers of a packet a network can handle. Or in simple words congestion can be understand as Higher rate of inputs to a router than outputs. And it occurs at the network layer. Congestion can cause: Excessive queueing delays Wasted network capacity on retransmissions Could have been used by other flows Situation gets worse with multi-hop paths Wasteful retransmit of prematurely timed out packets How bad does it get? 1000-fold reduction in bandwidth! Methods to control the congestion: Open loop congestion control: In this policies are applied to prevent congestion before it happens. In these mechanisms, congestion control is handled by either the source or the destination. Some of the policies are, Retransmission policy: A good retransmission policy can prevent congestion. The Retransmission policy and the retransmission timers must be designed to optimize Efficiency and at the same time prevent congestion. Acknowledgement policy: This policy imposed by the receiver may also effect congestion. If the receiver does not acknowledge every packet it receives, it may slow down the sender And help prevent congestion. Discard policy: A good discard policy possessed by the routers may prevent congestion and at the same time will not harm the integrity of the transmission.
For example:- in audio transmission, if the policy is to discard less sensitive packets when congestion is likely, the quality of sound is still preserved and congestion prevented. Closed loop congestion control: These mechanisms try to alleviate congestion after it happens. Several mechanisms have been used by different protocols. Some of them are, Back pressure: When a router is congested, it can inform the previous upstream router to reduce the rate of outgoing packets. The action can be recursive all the way to the router just prior to the source. This mechanisms is called as back pressure. Choke point: A choke point is a packet sent by a router to the source to inform it of congestion. This type of control is similar to ICMPs source quench packet. Implicit signaling: The source can detect an implicit signal warning of congestion and slow down its sending rate. For example:- the mere delay in receiving an acknowledgement can be a signal that the network is congested. Explicit signaling: The routers that experience congestion can send an explicit signal, the setting of a bit in a packet, for example, to inform the sender or the receiver of congestion.
Standard TCP Congestion Control Algorithms: The standard fare in TCP implementations today can be found in RFC 2581. This reference document specifies four standard congestion control algorithms that are now in common use. Each of the algorithms noted within that document was actually designed long before the standard was published .Their usefulness has passed the test of time. The four algorithms, Slow Start, Congestion Avoidance, Fast Retransmit and Fast Recovery are described below. i) Slow Start: Slow Start, a requirement for TCP software implementations is a mechanism used by the sender to control the transmission rate, otherwise known as sender-based flow control. This is accomplished through the return rate of acknowledgements from the receiver. In other words, the rate of acknowledgements returned by the receiver determines the rate at which the sender can transmit data. When a TCP connection first begins, the Slow Start algorithm initializes congestion window to one segment, which is the maximum segment size (MSS) initialized by the receiver during the connection establishment phase. When acknowledgements are returned by the receiver, the congestion window increases by one segment for each acknowledgement returned. Thus, the sender can transmit the minimum of the
congestion window and the advertised window of the receiver, which is simply called the transmission window. Slow Start is actually not very slow when the network is not congested and network response time is good. For example, the first successful transmission and acknowledgement of a TCP segment increases the window to two segments. After successful transmission of these two segments and acknowledgements completes, the window is increased to four segments. Then eight segments, then sixteen segments and so on, doubling from there on out up to the maximum window size advertised by the receiver or until congestion finally does occur. At some point the congestion window may become too large for the network or network conditions may change such that packets may be dropped. Packets lost will trigger a Time out at the sender. When this happens, the sender goes into congestion avoidance mode.
ii) Congestion Avoidance: During the initial data transfer phase of a TCP connection the Slow Start algorithm is used. However, there may be a point during Slow Start that the network is forced to drop one or more packets due to overload or congestion. If this happens, Congestion Avoidance is used to slow the transmission rate. However, Slow Start is used in conjunction with Congestion Avoidance as the means to get the data transfer going again so it doesnt slow down and stay slow. In the Congestion Avoidance algorithm a retransmission timer expiring or the reception of duplicate ACKs can implicitly signal the sender that a network congestion situation is Occurring . The sender immediately sets its transmission window to one half of the current window size (the minimum of the congestion window and the receivers advertised window size), but to at least two segments. If congestion was indicated by a timeout, the congestion window is reset to one segment, which automatically puts the sender into Slow Start mode. If congestion was indicated by duplicate ACKs, the Fast Retransmit and Fast Recovery algorithms are invoked (see below). As data is received during Congestion Avoidance, the congestion window is increased. However, Slow Start is only used up to the halfway point where congestion originally occurred. This halfway point was recorded earlier as the new transmission window. After this halfway point, the congestion window is increased by one segment for all segments in the transmission window that are acknowledged. This mechanism will force the sender to more slowly grow its transmission rate, as it will approach the point where congestion had previously been detected. iii) Fast Retransmit: When a duplicate ACK is received, the sender does not know if it is because a TCP segment was lost or simply that a segment was delayed and received out of order at the receiver. If the receiver can re-order segments, it should not be long before the receiver sends the latest expected acknowledgement. Typically no more than one or two
duplicate ACKs should be received when simple out of order conditions exist. If however more than two duplicate ACKs are received by the sender, it is a strong indication that at least one segment has been lost. The TCP sender will assume enough time has lapsed for all segments to be properly re-ordered by the fact that the receiver had enough time to send three duplicate ACKs. When three or more duplicate ACKs are received, the sender does not even wait for a retransmission timer to expire before retransmitting the segment (as indicated by the position of the duplicate ACK in the byte stream). This process is called the Fast Retransmit algorithm Immediately following Fast Retransmit is the Fast Recovery algorithm. iv) Fast Recovery Since the Fast Retransmit algorithm is used when duplicate ACKs are being received, the TCP sender has implicit knowledge that there is data still flowing to the receiver. Why? The reason is because duplicate ACKs can only be generated when a segment is received. This is a strong indication that serious network congestion may not exist and that the lost segment was a rare event. So instead of reducing the flow of data abruptly by going all the way into Slow Start, the sender only enters Congestion Avoidance mode. Rather than start at a window of one segment as in Slow Start mode, the sender resumes transmission with a larger window, incrementing as if in Congestion Avoidance mode. This allows for higher throughput under the condition of only moderate congestion.
Question 2) The network shown below uses distance vector routing. Assume that the given link costs apply to both directions and do not change over time. What are the contents of the routing tables (i.e. next hop and distances) at node C after the routing updates have stabilized. 1
A B
1
E
2 Answer )
To
New estimated
delay from c A B C D E 0 1 2 3 1 1 0 4 4 2 3 4 1 0 2
Question 3) A host sends to a network via a token bucket. The token bucket has a capacity of 15 MBITS and is filled with tokens at the rate of 5Mbps. Data is buffered if it arrives at the token bucket when there are no tokens. How long does it take for 30 Mb to enter the network assuming that the host sends at a peak rate of 20 Mbps and the token bucket is initially full.
Answer)
Question 4) State Optimality principle. Also explain count to infinity problem and justify the statement it reacts rapidly to good news but leisurely to bad news. This problem occurs in what type of routing algorithm. Answer) THE OPTIMALITY PRINCIPLE: This simply states that if router J is on the optimal path from router I to router K, then the optimal path from J to K also falls along this same path. This means we can form a sink tree as in the Figure.
Question 5) How is IPv6 different from IPv4.
IPv4 address
IPv6
32 bits long (4 bytes). Address 128 bits long (16 bytes). Basic is composed of a network and architecture is 64 bits for the a host portion, which depend network number and 64 bits for the on address class. Various host number. Often, the host address classes are defined: portion of an IPv6 address (or part A, B, C, D, or E depending on of it) will be a MAC address or initial few bits. The total other interface identifier. number of IPv4 addresses is 4 Depending on the subnet prefix, 294 967 296. IPv6 has a more complicated The text form of the IPv4 address is nnn.nnn.nnn.nnn, where 0<=nnn<=255, and each n is a decimal digit. Leading zeros may be omitted. Maximum number of print characters is 15, not counting a mask. architecture than IPv4. The number of IPv6 addresses is 10 28 (79 228 162 514 264 337 593 543 950 336) times larger than the number of IPv4 addresses. The text form of the IPv6 address is xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxx x:xxxx, where each x is a hexadecimal digit, representing 4 bits. Leading zeros may be omitted. The double colon (::) may be used once in the text form of an address, to designate any number of 0 bits. For example, ::ffff:10.120.78.40 is an IPv6 IPv4-mapped address. (See RFC 2373 for details. To view this RFC, see RFC Editor (http://www.rfceditor.org/rfcsearch.html). Allocation is in the earliest stages. The Internet Engineering Task Force (IETF) and Internet Architecture Board (IAB) have recommended that essentially every organization, home, or entity be allocated a /48 subnet prefix length. This would leave 16 bits for the organization to do subnetting. The address space is large enough to give every person in the world their own /48 subnet prefix length.
address allocation
Originally, addresses were allocated by network class. As address space is depleted, smaller allocations using Classless Inter-Domain Routing (CIDR) are made. Allocation has not been balanced among institutions and nations.
address lifetime
Generally, not an applicable IPv6 addresses have two lifetimes: concept, except for addresses preferred and valid, with the
assigned using DHCP.
preferred lifetime always <= valid. After the preferred lifetime expires, the address is not to be used as a source IP address. After the valid lifetime expires, the address is not used (recognized) as a valid destination IP address for incoming packets. Some IPv6 addresses have, by definition, infinite preferred and valid lifetimes; for example linklocal (see address scope).
address mask address prefix
Used to designate network from host portion.
Not used (see address prefix).
Sometimes used to designate Used to designate the subnet prefix network from host portion. of an address. Written as /nnn (up Sometimes written as /nn to 3 decimal digits, 0 <= nnn <= suffix on presentation form of 128) suffix after the print form. An address. example is fe80::982:2a5c/10, where the first 10 bits comprise the subnet prefix. Address Resolution Protocol is used by IPv4 to find a physical address, such as the MAC or link address, associated with an IPv4 address. IPv6 embeds these functions within IP itself as part of the algorithms for stateless autoconfiguration and neighbor discovery using Internet Control Message Protocol version 6 (ICMPv6). Hence, there is no such thing as ARP6.
Address Resolution Protocol (ARP)
address scope
For unicast addresses, the In IPv6, address scope is part of the concept does not apply. There architecture. Unicast addresses are designated private have 3 defined scopes, including address ranges and loopback. link-local, site-local and global; and Outside of that, addresses are multicast addresses have 14 scopes. assumed to be global. Default address selection for both source and destination takes scope into account. A scope zone is an instance of a scope in a particular network. As a consequence, IPv6 addresses sometimes have to be entered or associated with a zone ID. The syntax is %zid where zid is a number (usually small) or a name. The zone ID is written after the address and before the prefix. For example,
2ba::1:2:14e:9a9b:c%3/48. address types communications trace Unicast, multicast, and broadcast. Unicast, multicast, and anycast. See IPv6 address types for descriptions.
A tool to collect a detailed Same for IPv6, and IPv6 is trace of TCP/IP (and other) supported, including ICMPv6 and packets that enter and leave IPv6 packets tunneled in IPv4. an iSeries server. Configuration must be done on a newly installed system before it can communicate; that is, IP addresses and routes must be assigned. Configuration is optional, depending on functions required. An appropriate Ethernet or tunnel interface must be designated as an IPv6 interface, using iSeries Navigator. Once that is done, IPv6 interfaces are self-configuring. So, the system will be able to communicate with other IPv6 systems that are local and remote, depending on the type of network and whether an IPv6 router exists.
configuration
Domain Name System (DNS)
Applications accept host names and then use DNS to get an IP address, using socket API gethostbyname().
Same for IPv6. Support for IPv6 exists using AAAA (quad A) record type and reverse lookup (IP-toname). An application may elect to Applications also accept IP accept IPv6 addresses from DNS (or addresses and then use DNS not) and then use IPv6 to communicate (or not). to get host names using gethostbyaddr(). The socket API gethostbyname() is unchanged for IPv6 and the For IPv4, the domain for getaddrinfo() API can be used to reverse lookups is inobtain (at application choice) IPv6 addr.arpa. only, or IPv4 and IPv6 addresses. For IPv6, the domain used for reverse nibble lookups is ip6.arpa, and if not found then ip6.int (see API getnameinfo()).
Dynamic Host Used to dynamically obtain Configuration Protocol an IP address and other (DHCP) configuration information. File Transfer Protocol (FTP) fragments
Currently, DHCP does not support IPv6.
File Transfer Protocol allows Currently, FTP does not support you to send and receive files IPv6. across networks. When a packet is too big for For IPv6, fragmentation can only the next link over which it is occur at the source node, and to travel, it can be reassembly is only done at the
fragmented by the sender (host or router). host table
destination node. Currently, the fragmentation extension header is not supported.
On iSeries Navigator, a Currently, this table does not configurable table that support IPv6. Customers need to associates an Internet address configure a AAAA record in a DNS with a host name; for for IPv6 domain resolution. You example, 127.0.0.1, loopback. may run the DNS locally on the This table is used by the same system as the resolver, or you sockets name resolver, either may run it on a different system. before a DNS lookup or after a DNS lookup fails (determined by host name search priority). The conceptual or logical Same concept as IPv4. entity used by TCP/IP to send Can be started and stopped and receive packets and independently of each other and always closely associated with independently of TCP/IP using an IPv4 address, if not named iSeries Navigator only. with an IPv4 address. Sometimes referred to as a logical interface. Can be started and stopped independently of each other and independently of TCP/IP using STRTCPIFC and ENDTCPIFC commands and using iSeries Navigator.
interface
Internet Control Message Protocol (ICMP)
ICMP is used by IPv4 to communicate network information.
Used similarly for IPv6; however, Internet Control Message Protocol version 6 (ICMPv6) provides some new attributes. Basic error types remain, such as destination unreachable, echo request and reply. New types and codes are added to support neighbor discovery and related functions.
Internet Group Management Protocol (IGMP)
IGMP is used by IPv4 routers Replaced by MLD (multicast to find hosts that want traffic listener discovery) protocol for for a particular multicast IPv6. Does essentially what IGMP group, and used by IPv4 does for IPv4, but uses ICMPv6 by hosts to inform IPv4 routers adding a few MLD-specific ICMPv6 of existing multicast group type values. listeners (on the host).
IP header
Variable length of 20-60 bytes, depending on IP options present. Various options that may accompany an IP header (before any transport header).
Fixed length of 40 bytes. There are no IP header options. Generally, the IPv6 header is simpler than the IPv4 header. The IPv6 header has no options. Instead, IPv6 adds additional (optional) extension headers. The extension headers are AH and ESP (unchanged from IPv4), hop-byhop, routing, fragment, and destination. Currently, IPv6 does not support any extension headers.
IP header options
IP header protocol byte The protocol code of the The type of header immediately transport layer or packet following the IPv6 header. Uses the payload; for example, ICMP. same values as the IPv4 protocol field. But the architectural effect is to allow a currently defined range of next headers, and is easily extended. The next header will be a transport header, an extension header, or ICMPv6. IP header Type of Service (TOS) byte Used by QoS and differentiated services to designate a traffic class. Designates the IPv6 traffic class, similarly to IPv4. Uses different codes. Currently, IPv6 does not support TOS.
iSeries Navigator support
iSeries Navigator provides a The optional configuration for IPv6 full configuration function is provided in full by iSeries for TCP/IP. Navigator, including the IPv6 Configuration wizard. Used by an IP interface to get IPv6 has the same concept. to the physical network. Currently, only the 2838 and 2849 Many types exist; for Ethernet cards and tunnel lines are example, token ring, supported. Ethernet, and PPP. Sometimes referred to as the physical interface, link, or line. L2TP can be thought of as Currently, L2TP does not support virtual PPP, and works over IPv6. any supported line type. An interface with address of 127.*.*.* (typically 127.0.0.1) that can only be used by a node to send packets to itself. The concept is the same as in IPv4, and the single loopback address is 0000:0000:0000:0000:0000:0000:000 0:0001 or ::1 (shortened version).
LAN connection
Layer 2 Tunnel Protocol (L2TP) loopback address
The physical interface (line description) is named *LOOPBACK. Maximum Transmission Unit (MTU) Maximum transmission unit of a link is the maximum number of bytes that a particular link type, such as Ethernet or modem, supports. For IPv4, 576 is the typical minimum. A tool to look at status of TCP/IP connections, interfaces, or routes. Available using iSeries Navigator and 5250. Basic firewall functions integrated into TCP/IP, configured using iSeries Navigator.
The virtual physical interface is named *LOOPBACK6. IPv6 has an architected lower bound on MTU of 1280 bytes. That is, IPv6 will not fragment packets below this limit. To send IPv6 over a link with less than 1280 MTU, the link-layer must transparently fragment and defragment the IPv6 packets. Same for IPv6, and IPv6 is supported for both 5250 and iSeries Navigator.
netstat
Network Address Translation (NAT)
Currently, NAT does not support IPv6. More generally, IPv6 does not require NAT. The expanded address space of IPv6 eliminates the address shortage problem and enables easier renumbering. Currently, no changes are made to this table for IPv6.
network table
On iSeries Navigator, a configurable table that associates a network name with an IP address without mask. For example, host Network14 and IP address 1.2.3.4. Does not exist.
node info query
A simple and convenient network tool that should work like ping, except with content: an IPv6 node may query another IPv6 node for the target's DNS name, IPv6 unicast address, or IPv4 address. Currently, not supported. Currently, packet filtering does not support IPv6. However, IPv4 filtering can be applied to tunneled IPv6 traffic. Currently, IPv6 packets are not forwarded.
packet filtering
Basic firewall functions integrated into TCP/IP, configured using iSeries Navigator. The iSeries server can be configured to forward IP packets it receives for nonlocal IP addresses. Typically, the inbound
packet forwarding
interface and outbound interface are connected to different LANs. packet tunneling In IPv4, tunneling occurs in For IPv6, tunneling in IPv4 packets VPN for tunnel-mode VPN is expected to be a major part of its connections (IPv4 tunneled in evolution. Currently, at least 5 IPv4) and in L2TP. different types of 6-in-4 tunneling are defined by IETF, each with different attributes and advantages. A basic and flexible type of IPv6-inIPv4 tunneling is supported to allow IPv6 nodes to communicate across the existing IPv4 Internet. Called configured tunneling, it provides a virtual point-to-point link between two IPv6 nodes and uses a new type of tunnel line called *TNLCFG64. PING Basic TCP/IP tool to test Same for IPv6, and IPv6 is reachability. Available using supported, for both 5250 and iSeries iSeries Navigator and 5250. Navigator. Currently, PPP does not support IPv6.
Point-to-Point Protocol PPP supports dial-up (PPP) interfaces over various modem and line types. port restrictions
These iSeries panels allow a Not supported for IPv6. Configured customer to configure restrictions apply only to IPv4. selected port number or port number ranges for TCP or UDP so that they are only available for a specific profile. TCP and UDP have separate port spaces, each identified by port numbers in the range 1-65535. For IPv6, ports work the same as IPv4. Because these are in a new address family, there are now four separate port spaces. For example, there are two TCP port 80 spaces to which an application can bind, one in AF_INET and one in AF_INET6.
ports
private and public addresses
All IPv4 addresses are public, IPv6 has an analogous concept, but except for three address with important differences. ranges that have been Addresses are public or temporary, designated as private by previously termed anonymous. See IETF RFC 1918: 10.*.*.* RFC 3041. Unlike IPv4 private (10/8), 172.16.0.0 through addresses, temporary addresses can 172.31.255.255 (172.16/12) , be globally routed. The motivation and 192.168.*.* (192.168/16). is also different; IPv6 temporary
Private address domains are commonly used within organizations. Private addresses cannot be routed across the Internet.
addresses are meant to shield the identity of a client when it initiates communication (a privacy concern). Temporary addresses have a limited lifetime, and do not contain an interface identifier that is a link (MAC) address. They are generally indistinguishable from public addresses. IPv6 has the notion of limited address scope using its architected scope designations (see address scope).
protocol table
On iSeries Navigator, a configurable table that associates a protocol name with its assigned protocol number; for example, UDP, 17. The system is shipped with a small number of entries: IP, TCP, UDP, ICMP.
The table supports IPv6 without change.
Quality of service (QoS) Quality of service allows you Currently, QoS does not support to request packet priority and IPv6. However, when IPv6 is bandwidth for TCP/IP tunneled in IPv4, existing iSeries applications. QoS facilities can be applied to the IPv4 traffic, which will then transparently handle the IPv6 payloads. renumbering Done by manual reconfiguration, with the possible exception of DHCP. Generally, for a site or organization, a difficult and troublesome process to avoid if possible. Is an important architectural element of IPv6, and is supposed to be largely automatic especially within the /48 prefix.
route
Logically, a mapping of a set Conceptually, the same as IPv4. of IP addresses (may contain One important difference: IPv6 only 1) to a physical interface routes are associated (bound) to a and a single next hop IP physical interface (a link, such as address. IP packets whose *TNLCFG64 or ETH03) rather destination address is defined than an interface. There are various as part of the set are reasons for this. One reason is that forwarded to the next hop source address selection functions using the line. IPv4 routes are differently for IPv6 than for IPv4. associated with an IPv4 See source address selection.
interface, hence, an IPv4 address. The default route is *DFTROUTE. Routing Information Protocol (RIP) services table RIP is a routing protocol supported by the routed daemon.
Duplicate routes are allowed to improve robustness, but they are ignored during route lookup.
Currently, RIP does not support IPv6. IPv6 routing uses static routes.
On the iSeries server, a No changes are made to this table configurable table that for IPv6. associates a service name with a port and protocol; for example, service name FTPcontrol, port 21, TCP and UDP. A large number of wellknown services are listed in the services table. Many applications use this table to determine which port to use.
Simple Network Management Protocol (SNMP) sockets API
SNMP is a protocol for system management. These APIs are the way applications use TCP/IP. Applications that do not need IPv6 are not affected by sockets changes to support IPv6.
Currently, SNMP does not support IPv6. IPv6 routing uses static routes. IPv6 enhances sockets so that applications can now use IPv6, using a new address family: AF_INET6. The enhancements have been designed so that existing IPv4 applications are completely unaffected by IPv6 and API changes. Applications that want to support concurrent IPv4 and IPv6 traffic, or IPv6-only traffic, are easily accommodated using IPv4mapped IPv6 addresses of the form ::ffff:a.b.c.d, where a.b.c.d is the IPv4 address of the client. The new APIs also include support for converting IPv6 addresses from text to binary and from binary to text. See Use AF_INET6 address family for more information on sockets enhancements for IPv6.
source address selection An application may designate As with IPv4, an application may a source IP (typically, using designate a source IPv6 address sockets bind()) . If it binds to using bind(). Similarly to IPv4, it INADDR_ANY, a source IP can let the system choose an IPv6 is chosen based on the route. source address by using in6addr_any. But since IPv6 lines have many IPv6 addresses, the internal method of choosing a source IP is different. starting and stopping Use STRTCP and ENDTCP Same as IPv4. IPv4 and IPv6 are to start or end TCP/IP. not started or stopped independently of one another or independently of TCP/IP. That is, you start and stop all of TCP/IP, not just IPv4 or IPv6. Any IPv6 interfaces are automatically started if the AUTOSTART parameter = *YES (the default). IPv6 cannot be used or configured without IPv4, and IPv6 must have IPv6 loopback configured (::1). Telnet Telnet allows you to log on Currently, Telnet does not support and use a remote computer as IPv6. though you were connected to it directly. Basic TCP/IP tool to do path Same for IPv6, and IPv6 is determination. Available supported for both 5250 and iSeries using iSeries Navigator and Navigator. 5250. TCP, UDP, RAW. A new Same three transports exist and are transport, Stream Control functionally unchanged for IPv6. Transmission Protocol (SCTP), aims to offer the best features of TCP and UDP, that is, guaranteed connectionless communication. SCTP is in the earliest stage of use, and is not supported on iSeries. Apparently, not defined, as such. Socket programming uses 0.0.0.0 as INADDR_ANY. Defined as ::/128 (128 0 bits). It is used as the source IP in some neighbor discovery packets, and various other contexts, like sockets. Socket programming uses ::/128 as
trace route
transport layers
unspecified address
in6addr_any. virtual private networking (VPN) Virtual private networking (using IPsec) allows you to extend a secure, private network over an existing public network. Currently, VPN does not support IPv6. However, when IPv6 is tunneled in IPv4, existing iSeries VPN facilities can be applied to the IPv4 traffic, which then transparently handles the IPv6 payloads.
Question 6) A class B network on the internet has a subnet mask of 255.255.240.0. what is the maximum number of hosts per subnet. Answer) its of class b It is 255.255.240.0, here are 10 free bytes , So, the total number of hosts on a subnet is = 2^10=1024-2 =1022 ans Question 7) Convert IP address whose hexadecimal representation is C22F1582 to dotted decimal notation.
Answer) hexadecimal representation = C22F.1582 Decimal representation = 1100001000101111.0001010110000010
Anda mungkin juga menyukai
- CCNA Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesDari EverandCCNA Interview Questions You'll Most Likely Be Asked: Job Interview Questions SeriesBelum ada peringkat
- TCP Congestion ControlDokumen16 halamanTCP Congestion Controlpy thonBelum ada peringkat
- Signal Integrity: From High-Speed to Radiofrequency ApplicationsDari EverandSignal Integrity: From High-Speed to Radiofrequency ApplicationsBelum ada peringkat
- COngestion COntrol.pptDokumen32 halamanCOngestion COntrol.pptRANGAM NAGARAJUBelum ada peringkat
- NS simulation implementing Large Window over TCP SACKDokumen5 halamanNS simulation implementing Large Window over TCP SACKElizabeth FlowersBelum ada peringkat
- TCP Congestion Control - WikipediaDokumen12 halamanTCP Congestion Control - WikipediaJesmin MostafaBelum ada peringkat
- NW Lec 6Dokumen28 halamanNW Lec 6omarnader16Belum ada peringkat
- Unit 4 Lec5Dokumen26 halamanUnit 4 Lec5SangetaBelum ada peringkat
- Lecture 6Dokumen6 halamanLecture 6Rylan2911Belum ada peringkat
- Transport Layer Notes Module 3Dokumen10 halamanTransport Layer Notes Module 3amukhopadhyayBelum ada peringkat
- Transport Layer Challenges By: Talha Mudassar 015 Fahad Nabi 63 Rashid Mehmood 96Dokumen6 halamanTransport Layer Challenges By: Talha Mudassar 015 Fahad Nabi 63 Rashid Mehmood 96Noman AliBelum ada peringkat
- Congestion ControlDokumen4 halamanCongestion ControladdulahiBelum ada peringkat
- Throughput Analysis of TCP Newreno For Multiple BottlenecksDokumen10 halamanThroughput Analysis of TCP Newreno For Multiple BottlenecksTJPRC PublicationsBelum ada peringkat
- Note 1621Dokumen3 halamanNote 1621Satish MehtaBelum ada peringkat
- Ex No: Date: Simulation of TCP Using NS-2 AimDokumen11 halamanEx No: Date: Simulation of TCP Using NS-2 Aimapi-19782437Belum ada peringkat
- Effect of Maximum Congestion of TCP Reno in Decagon NoCDokumen5 halamanEffect of Maximum Congestion of TCP Reno in Decagon NoCJournal of ComputingBelum ada peringkat
- Priority TX in 802 - 11Dokumen19 halamanPriority TX in 802 - 11Manuel ChawBelum ada peringkat
- Transmission Control Protocol (TCP) : Comparison of TCP Congestion Control Algorithms Using Netsim™Dokumen20 halamanTransmission Control Protocol (TCP) : Comparison of TCP Congestion Control Algorithms Using Netsim™Thái NguyễnBelum ada peringkat
- Host-To-Host Congestion Control For TCPDokumen9 halamanHost-To-Host Congestion Control For TCPSantosh RaiBelum ada peringkat
- TCP - Congestion Control Algorithm For Enhancing High-Speed NetworksDokumen5 halamanTCP - Congestion Control Algorithm For Enhancing High-Speed NetworksJournal of Computer ApplicationsBelum ada peringkat
- Congestion ControlDokumen17 halamanCongestion Controlavantika bishtBelum ada peringkat
- TCP Congestion Control and Timer ManagementDokumen7 halamanTCP Congestion Control and Timer ManagementNishant BHARDWAJBelum ada peringkat
- Unit 6 IPQoS Part 1Dokumen9 halamanUnit 6 IPQoS Part 1nirjan ghimireBelum ada peringkat
- Congestion in Computer NetworkDokumen10 halamanCongestion in Computer Network1DA19CS111 PrajathBelum ada peringkat
- Congestion in Data NetworksDokumen11 halamanCongestion in Data NetworksMiM1990Belum ada peringkat
- CN 4Dokumen22 halamanCN 4S M AkashBelum ada peringkat
- TCP Tuning On Sender SideDokumen6 halamanTCP Tuning On Sender SideAbi AnnunBelum ada peringkat
- Congestion Control and Quality of ServiceDokumen45 halamanCongestion Control and Quality of ServiceSahilBelum ada peringkat
- TCP Model For Short Lived Flows: Marco Mellia, Member, IEEE, Ion Stoica, Member, IEEE, and Hui Zhang, Member, IEEEDokumen3 halamanTCP Model For Short Lived Flows: Marco Mellia, Member, IEEE, Ion Stoica, Member, IEEE, and Hui Zhang, Member, IEEEFernando MendozaBelum ada peringkat
- Lecture 6 Transport Layer IIDokumen10 halamanLecture 6 Transport Layer IITanvir ChowdhuryBelum ada peringkat
- CN Notes-Unit VDokumen5 halamanCN Notes-Unit Vapi-278882881Belum ada peringkat
- TCP Congestion Control Based On AQM Algorithm: AbstractDokumen9 halamanTCP Congestion Control Based On AQM Algorithm: AbstractRakeshconclaveBelum ada peringkat
- TCP Congestion Control Algorithm Estimation Using HMMDokumen5 halamanTCP Congestion Control Algorithm Estimation Using HMMyeahyeahyeahyeah69Belum ada peringkat
- Advanced Computer Networks: MS-2 SemesterDokumen21 halamanAdvanced Computer Networks: MS-2 SemesterAmir ButtBelum ada peringkat
- Ee534 Lab10 (Duong - Le)Dokumen6 halamanEe534 Lab10 (Duong - Le)Rock RáchBelum ada peringkat
- Indirect TCP, Snooping TCP, Mobile TCP - Mobile Transport LayerDokumen12 halamanIndirect TCP, Snooping TCP, Mobile TCP - Mobile Transport LayerMukesh91% (220)
- CN Ass 3 SolnDokumen10 halamanCN Ass 3 SolnNoobs RageBelum ada peringkat
- CN Unit-2 Congestion, SCTP, QosDokumen40 halamanCN Unit-2 Congestion, SCTP, QosKowsalya GBelum ada peringkat
- Unit 5 Final NotesDokumen20 halamanUnit 5 Final Notesappsectesting3Belum ada peringkat
- TCP Over AtmDokumen19 halamanTCP Over AtmAnonymous Ie0oEXP2eBelum ada peringkat
- Transmission Control Protocol (TCP) : Comparison of TCP Congestion Control Algorithms Using Netsim™Dokumen12 halamanTransmission Control Protocol (TCP) : Comparison of TCP Congestion Control Algorithms Using Netsim™AhmedElhajBelum ada peringkat
- Congestion Control and QoSDokumen8 halamanCongestion Control and QoSAnkit SinghBelum ada peringkat
- Congestion Control TechniquesDokumen22 halamanCongestion Control Techniquesamit mahajan100% (1)
- Mobile TCPDokumen7 halamanMobile TCPTUSHARBelum ada peringkat
- Network CongestionDokumen9 halamanNetwork Congestionpy thonBelum ada peringkat
- TCP Congestion Control NewReno, BIC, Hybrid Illinois, ACC Algorithm Simulation and Analysis Using The NS3Dokumen13 halamanTCP Congestion Control NewReno, BIC, Hybrid Illinois, ACC Algorithm Simulation and Analysis Using The NS3GirishPaliwalBelum ada peringkat
- Unit 5Dokumen26 halamanUnit 5ashwani tyagiBelum ada peringkat
- 13-CongestioninDataNetworks REALDokumen36 halaman13-CongestioninDataNetworks REALmemo1023Belum ada peringkat
- UnitII HSNDokumen68 halamanUnitII HSNAnitha Hassan KabeerBelum ada peringkat
- Congestion Control: CSE 123: Computer Networks Stefan SavageDokumen31 halamanCongestion Control: CSE 123: Computer Networks Stefan SavageMhackSahuBelum ada peringkat
- TCP TraficDokumen82 halamanTCP TraficAdv Antony JudeBelum ada peringkat
- Congestion Avoidance and Control: Van Jacobson Michael J. KarelsDokumen21 halamanCongestion Avoidance and Control: Van Jacobson Michael J. Karelsgramirez77Belum ada peringkat
- MC Unit 4Dokumen28 halamanMC Unit 4Naveenkumar TariBelum ada peringkat
- 4444.... Mobile Transport Layer Mobile Transport Layer Mobile Transport Layer Mobile Transport LayerDokumen16 halaman4444.... Mobile Transport Layer Mobile Transport Layer Mobile Transport Layer Mobile Transport LayerDr. Sashi Kanth Reddy ABelum ada peringkat
- Unit3 Congestion ControlDokumen37 halamanUnit3 Congestion ControlPratyaksha RatnapriyaBelum ada peringkat
- Congestion Control: A Dynamic ApproachDokumen3 halamanCongestion Control: A Dynamic ApproachInternational Organization of Scientific Research (IOSR)Belum ada peringkat
- 09 Data Link Layer-Flow ControlDokumen56 halaman09 Data Link Layer-Flow ControlSatyajeet GaurBelum ada peringkat
- Idresss Sir#9 OKDokumen14 halamanIdresss Sir#9 OKDil NawazBelum ada peringkat
- Welcome ToDokumen39 halamanWelcome Tovgvivekgupta2Belum ada peringkat
- HackersDokumen1 halamanHackersvishu_51787Belum ada peringkat
- VirtualDJ 7 - User GuideDokumen65 halamanVirtualDJ 7 - User GuideBastian Schweinsteiguer KolvemorBelum ada peringkat
- InfoDokumen1 halamanInfovgvivekgupta2Belum ada peringkat
- Ip 4 Vsip 6Dokumen2 halamanIp 4 Vsip 6vgvivekgupta2Belum ada peringkat
- Honda's Product Mix, Differentiation and Marketing ActivitiesDokumen21 halamanHonda's Product Mix, Differentiation and Marketing Activitiesvgvivekgupta2Belum ada peringkat
- Tele Gas AgenciesDokumen5 halamanTele Gas Agenciesvgvivekgupta2Belum ada peringkat
- LicenseDokumen1 halamanLicenseAndri WaeyojodowodowoBelum ada peringkat
- Honda City (Fit Sedan)Dokumen9 halamanHonda City (Fit Sedan)Celiano AntaoBelum ada peringkat
- Honda's Product Mix, Differentiation and Marketing ActivitiesDokumen21 halamanHonda's Product Mix, Differentiation and Marketing Activitiesvgvivekgupta2Belum ada peringkat
- Dual Powered Scooter Sanchit ModifiedDokumen10 halamanDual Powered Scooter Sanchit Modifiedvgvivekgupta2Belum ada peringkat
- Computer Networks Internal ExamDokumen3 halamanComputer Networks Internal ExamsakeebshaikhBelum ada peringkat
- Course PDFDokumen5 halamanCourse PDFRohit SakpalBelum ada peringkat
- UNV IPC2122LB-ADF28 (40) KM-G 2MP HD Fixed IR Bullet Network Camera V1.0-ENDokumen4 halamanUNV IPC2122LB-ADF28 (40) KM-G 2MP HD Fixed IR Bullet Network Camera V1.0-ENGurudattaBelum ada peringkat
- TroubleshootingDokumen8 halamanTroubleshootingdivakarBelum ada peringkat
- IT430 E-Commerce Solved MID Term Paper 02Dokumen6 halamanIT430 E-Commerce Solved MID Term Paper 02Rimsha Tariq0% (1)
- Viva Questions CNDokumen2 halamanViva Questions CNChandrikaGowdaBelum ada peringkat
- RTN 950 V100R003C03 Configuration Guide 04 (U2000)Dokumen2.188 halamanRTN 950 V100R003C03 Configuration Guide 04 (U2000)Alvaro Avila SanchezBelum ada peringkat
- Determine Best Fit TopologyDokumen41 halamanDetermine Best Fit Topologynuri mohammed100% (1)
- RAD's IP RAN SolutionsDokumen5 halamanRAD's IP RAN SolutionsblackchakaBelum ada peringkat
- Network Tools and Protocols Lab 2: Introduction To Iperf3Dokumen17 halamanNetwork Tools and Protocols Lab 2: Introduction To Iperf3Fabio MenesesBelum ada peringkat
- 323Dokumen267 halaman323Rishi ShuklaBelum ada peringkat
- Cisco 300-101: IP Routing EssentialsDokumen18 halamanCisco 300-101: IP Routing Essentialsfredf1Belum ada peringkat
- Packet TracerDokumen11 halamanPacket TracerFauzan FiqriansyahBelum ada peringkat
- Chapter1 - ArchitectureDokumen24 halamanChapter1 - Architectureposter RMBelum ada peringkat
- CN Lab Programs Record (2017-2018)Dokumen49 halamanCN Lab Programs Record (2017-2018)SANTHI G BBelum ada peringkat
- Index: No. Name NoDokumen277 halamanIndex: No. Name NovivekBelum ada peringkat
- Cisco - Configuring HSRPDokumen14 halamanCisco - Configuring HSRPKenn SokotBelum ada peringkat
- Configuration and Setup - EFI Fiery® Color Server For Xerox DocuColor 242/252/260Dokumen76 halamanConfiguration and Setup - EFI Fiery® Color Server For Xerox DocuColor 242/252/260Peter DuDeck100% (1)
- Intro LonWorks PDFDokumen67 halamanIntro LonWorks PDFasifaliabidBelum ada peringkat
- CBP 13 Using Windows Nps As Radius in Eduroam FinalDokumen78 halamanCBP 13 Using Windows Nps As Radius in Eduroam FinalMed TisBelum ada peringkat
- Chapter 9 - Ethernet: CCNA Exploration 4.0Dokumen90 halamanChapter 9 - Ethernet: CCNA Exploration 4.0kiennaBelum ada peringkat
- How To Calculate A Subnet MaskDokumen9 halamanHow To Calculate A Subnet MaskVivekananda GNBelum ada peringkat
- Department of Electronics & Communication Computer Networks (Cs1302)Dokumen127 halamanDepartment of Electronics & Communication Computer Networks (Cs1302)anon-767742Belum ada peringkat
- How To Block BitsadTorrent, Download-Manager Through ASA - Firewalling - Cisco Support Community - 5966 - 11566671Dokumen12 halamanHow To Block BitsadTorrent, Download-Manager Through ASA - Firewalling - Cisco Support Community - 5966 - 11566671Bee BazzBelum ada peringkat
- Cisco Intersight Mode With UCS X-Series v1 - Instant Demo: Americas HeadquartersDokumen54 halamanCisco Intersight Mode With UCS X-Series v1 - Instant Demo: Americas HeadquartersAndyBelum ada peringkat
- IP RAN TroubleshootingDokumen26 halamanIP RAN TroubleshootingSenthilathiban Thevarasa100% (1)
- Brocade, Mcdata and Cisco Cli CommandsDokumen10 halamanBrocade, Mcdata and Cisco Cli CommandsHarsh_24Belum ada peringkat
- Set up bandwidth sharing with Gargoyle routerDokumen6 halamanSet up bandwidth sharing with Gargoyle routerDarko MilovanovićBelum ada peringkat
- IPTube User GuideDokumen197 halamanIPTube User GuideHaitham Hasan TroyBelum ada peringkat
- MindCert Wireshark MindMapDokumen1 halamanMindCert Wireshark MindMapacehussainBelum ada peringkat
- Microsoft Azure Infrastructure Services for Architects: Designing Cloud SolutionsDari EverandMicrosoft Azure Infrastructure Services for Architects: Designing Cloud SolutionsBelum ada peringkat
- CCNA: 3 in 1- Beginner's Guide+ Tips on Taking the Exam+ Simple and Effective Strategies to Learn About CCNA (Cisco Certified Network Associate) Routing And Switching CertificationDari EverandCCNA: 3 in 1- Beginner's Guide+ Tips on Taking the Exam+ Simple and Effective Strategies to Learn About CCNA (Cisco Certified Network Associate) Routing And Switching CertificationBelum ada peringkat
- The Ultimate Kali Linux Book - Second Edition: Perform advanced penetration testing using Nmap, Metasploit, Aircrack-ng, and EmpireDari EverandThe Ultimate Kali Linux Book - Second Edition: Perform advanced penetration testing using Nmap, Metasploit, Aircrack-ng, and EmpireBelum ada peringkat
- Computer Networking: The Complete Guide to Understanding Wireless Technology, Network Security, Computer Architecture and Communications Systems (Including Cisco, CCNA and CCENT)Dari EverandComputer Networking: The Complete Guide to Understanding Wireless Technology, Network Security, Computer Architecture and Communications Systems (Including Cisco, CCNA and CCENT)Belum ada peringkat
- Computer Networking: The Complete Beginner's Guide to Learning the Basics of Network Security, Computer Architecture, Wireless Technology and Communications Systems (Including Cisco, CCENT, and CCNA)Dari EverandComputer Networking: The Complete Beginner's Guide to Learning the Basics of Network Security, Computer Architecture, Wireless Technology and Communications Systems (Including Cisco, CCENT, and CCNA)Penilaian: 4 dari 5 bintang4/5 (4)
- CEH Certified Ethical Hacker Practice Exams, Third EditionDari EverandCEH Certified Ethical Hacker Practice Exams, Third EditionBelum ada peringkat
- AWS Certified Cloud Practitioner Study Guide: CLF-C01 ExamDari EverandAWS Certified Cloud Practitioner Study Guide: CLF-C01 ExamPenilaian: 5 dari 5 bintang5/5 (1)
- The Compete Ccna 200-301 Study Guide: Network Engineering EditionDari EverandThe Compete Ccna 200-301 Study Guide: Network Engineering EditionPenilaian: 5 dari 5 bintang5/5 (4)
- Computer Systems and Networking Guide: A Complete Guide to the Basic Concepts in Computer Systems, Networking, IP Subnetting and Network SecurityDari EverandComputer Systems and Networking Guide: A Complete Guide to the Basic Concepts in Computer Systems, Networking, IP Subnetting and Network SecurityPenilaian: 4.5 dari 5 bintang4.5/5 (13)
- Evaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsDari EverandEvaluation of Some Websites that Offer Virtual Phone Numbers for SMS Reception and Websites to Obtain Virtual Debit/Credit Cards for Online Accounts VerificationsBelum ada peringkat
- Hacking: A Beginners Guide To Your First Computer Hack; Learn To Crack A Wireless Network, Basic Security Penetration Made Easy and Step By Step Kali LinuxDari EverandHacking: A Beginners Guide To Your First Computer Hack; Learn To Crack A Wireless Network, Basic Security Penetration Made Easy and Step By Step Kali LinuxPenilaian: 4.5 dari 5 bintang4.5/5 (67)
- Amazon Web Services (AWS) Interview Questions and AnswersDari EverandAmazon Web Services (AWS) Interview Questions and AnswersPenilaian: 4.5 dari 5 bintang4.5/5 (3)
- ITIL 4: Digital and IT strategy: Reference and study guideDari EverandITIL 4: Digital and IT strategy: Reference and study guidePenilaian: 5 dari 5 bintang5/5 (1)
- The CompTIA Network+ Computing Technology Industry Association Certification N10-008 Study Guide: Hi-Tech Edition: Proven Methods to Pass the Exam with Confidence - Practice Test with AnswersDari EverandThe CompTIA Network+ Computing Technology Industry Association Certification N10-008 Study Guide: Hi-Tech Edition: Proven Methods to Pass the Exam with Confidence - Practice Test with AnswersBelum ada peringkat
- ITIL 4: Create, Deliver and Support: Reference and study guideDari EverandITIL 4: Create, Deliver and Support: Reference and study guideBelum ada peringkat
- ITIL® 4 Create, Deliver and Support (CDS): Your companion to the ITIL 4 Managing Professional CDS certificationDari EverandITIL® 4 Create, Deliver and Support (CDS): Your companion to the ITIL 4 Managing Professional CDS certificationPenilaian: 5 dari 5 bintang5/5 (2)
- A Practical Guide Wireshark ForensicsDari EverandA Practical Guide Wireshark ForensicsPenilaian: 5 dari 5 bintang5/5 (4)
- AWS Certified Solutions Architect Study Guide: Associate SAA-C02 ExamDari EverandAWS Certified Solutions Architect Study Guide: Associate SAA-C02 ExamBelum ada peringkat
- ITIL® 4 Direct, Plan and Improve (DPI): Your companion to the ITIL 4 Managing Professional and Strategic Leader DPI certificationDari EverandITIL® 4 Direct, Plan and Improve (DPI): Your companion to the ITIL 4 Managing Professional and Strategic Leader DPI certificationBelum ada peringkat
- Introduction to Cyber-Warfare: A Multidisciplinary ApproachDari EverandIntroduction to Cyber-Warfare: A Multidisciplinary ApproachPenilaian: 4.5 dari 5 bintang4.5/5 (3)
- CCST Cisco Certified Support Technician Study Guide: Networking ExamDari EverandCCST Cisco Certified Support Technician Study Guide: Networking ExamBelum ada peringkat