Comparison of SDLC Methodologies
Diunggah oleh
Henk CraffordDeskripsi Asli:
Hak Cipta
Format Tersedia
Bagikan dokumen Ini
Apakah menurut Anda dokumen ini bermanfaat?
Apakah konten ini tidak pantas?
Laporkan Dokumen IniHak Cipta:
Format Tersedia
Comparison of SDLC Methodologies
Diunggah oleh
Henk CraffordHak Cipta:
Format Tersedia
Comparison of Software Development Lifecycle Methodologies
James E. Purcell, CISSP, GSEC, GCIH, PMP, MCSE
Comparison of Software Development Lifecycle Methodologies
Introduction
This purpose of this paper is to give the CISSP student an understanding of the Software Development Lifecycle (SDLC) models available to software developers. The student will also see examples of where each model is most appropriate for various types of software development projects. The models covered are the ones most likely to be included in CISSP exam questions. Note that the SDLC acronym is also used to represent System Development Life Cycle. In many cases, a decision is made to purchase or outsource the software and associated hardware and network systems needed to implement a new application. This is often referred to as the buy or build decision. This paper focuses on the Software Development Life Cycle models, but most of the phases, terms, and issues discussed apply to both the buy and build process.
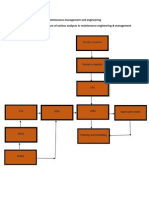
SDLC Models
To help understand and implement the SDLC phases (Project Initiation, Design Analysis, System Design Specification, Programming and Testing, Installation and Maintenance, and Destruction), various SDLC models have been created by software development experts, universities, and standards organizations. New SDLC models are introduced on a regular basis as new technology and new research (and sometimes new fads) requires new SDLC techniques. Recent new SDLC models include Extreme Programming and Agile Development. This paper looks at the most commonly known and used models and describes situations where the model is an appropriate choice.
Waterfall Model
The Waterfall Model is the oldest and most well-known SDLC model. The distinctive feature of the Waterfall model is its sequential step-by-step process from requirements analysis to maintenance. The major weakness of the Waterfall Model is that after project requirements are gathered in the first phase, there is no formal way to make changes to the project as requirements change or more information becomes available to the project team. Because requirements almost always change during long development cycles, often the product that is implemented at the end of the process is obsolete as it goes into production. The Waterfall Model is a poor choice for software development projects where requirements are not well-known or understood by the development team. It might not a good model for complex projects or projects that take more than a few months to complete. Think about doing a home improvement project (such as new hardwood floors) for the first time and only being allowed to go the hardware store one time. The risk the project will fail is high.
What are good candidate software development projects for the Waterfall Model? Systems that have well-defined and understood requirements are a good fit for the Waterfall Model. For instance, a military system aiming an artillery shell is a system with a single, simple requirement; put the shell on the target. This also assumes that the developers have worked on similar systems in the past and are experts in the application domain (artillery fire control systems). To follow the home improvement example, after a visit to a home to get specifications, an experience flooring contractor could install new hardwood floors with only one trip to the hardware store. In this case, the risk of project failure is low.
Spiral Model
In response to the weaknesses and failures of the Waterfall SDLC Model, many new models were developed that add some form of iteration to the software development process. In the Spiral SDLC Model, the development team starts with a small set of requirements and goes through each development phase (except Installation and Maintenance) for those set of requirements. Based on lesson learned from the initial iteration (via a risk analysis process), the development team adds functionality for additional requirements in ever-increasing spirals until the application is ready for the Installation and Maintenance phase (production). Each of the iterations prior to the production version is a prototype of the application. The advantage of the Spiral Model over the Waterfall Model is that the iterative approach allows development to begin even when all the system requirements are not known or understood by the development team. As each prototype is tested, user feedback is used to make sure the project is on track. The risk analysis step provides a formal method to ensure the project stays on track even if requirements do change. If new techniques or business requirements make the project unnecessary, it can be canceled before too many resources are wasted. In todays business environment, the Spiral Model (or its other iterative model cousins) is the most used SDLC model. An example application development project that would a good candidate for the Spiral Model is an online customer support system where it is not well-understood what services customers want or can accomplish online. Each iterative prototype helps answer the question, Can and will customers use this system? The Spiral Model also lets the development team build application domain experience with every iteration. In the home improvement project example, it would be like starting the hardwood flooring project in the upstairs hall to get experience with the flooring process in a low-risk area before moving to living areas where a mistake would be costly. The Spiral Model combines elements of the Top-down and Bottom-up SDLC models that are discussed in the next sections.
Top-Down Model
The Top-down SDLC model was popularized by IBM in the 1970s, and its concepts are used in other SDLC models such as the Waterfall and Spiral Models previously discussed. In a pure Top-down model, high-level requirements are documented, and programs are built to meet these requirements. Then, the next level is designed and built. A good way to picture the Top-down model is to think of a menu-driven application. The
top level menu items would be designed and coded, and then each sublevel would be added after the top level was finished. Each menu item represents a subsystem of the total application. The Top-down model is a good fit when the application is a new one and there is no existing functionality that can be incorporated into the new system. A major problem with the Top-down model is that real system functionality is not added and cannot be tested until late in the development process. If problems are not detected early in the project, they can be costly to remedy later.
Bottom-Up Model
In the Bottom-up SDLC model, the lowest level of functionality is designed and programmed first, and finally all the pieces are integrated together into the finished application. This means that, generally, the most complex components are developed and tested first. The idea is that any project show-stoppers will surface early in the project. The Bottom-up model also encourages the development and use of reusable software components that can be used multiple times across many software development projects. Again, think of a menu driven system where the development starts with the lowest level menu items. The disadvantage of the Bottom-up model is that an extreme amount of coordination is required to be sure that the individual software components work together correctly in the finished system. Few systems are developed purely from the Bottom-up model.
Hybrid Model
The Hybrid SDLC model combines the top-down and bottom-up models. Using the menu driven application example, the design team primarily works top down, but the development team identifies two types of lower level components to work on at the same time as the high-level components. The first type of low-level component would be existing software modules from other projects that can be reused in the new project. The other type of low-level component that would be developed early in the project would be software components with a high risk of failure. This approach allows the development team to make changes to the system early in the project if problems occur with the highrisk components. A new data access technique the team has not used before or a component that might require high amounts of CPU processing time is an example of a high-risk low-level component. In reality, many of the SDLC models are a variation of the Hybrid Model. The Spiral Model is an example discussed previously.
Rapid Prototyping
With the demand for faster software development, and because of many well-documented failures of traditional SDLC models, Rapid Application Development (RAD) was introduced as a better way to add functionality to an application. The main new tenant of RAD compared to older SDLC models is the use of prototypes. After a quick requirements gathering phase, a prototype application is built and presented to the application users. Feedback from the user provides a loop to improve or add functionality
to the application. Early RAD models did not involve the use of real data in the prototype, but new RAD implementations do use real data. The advantage of Rapid Prototyping Models is that time-to-market is greatly reduced. Rapid Prototyping skips many of the steps in traditional SDLC models in favor of fast and low-cost software development. The idea is that application software is a throwaway. If a new version of the software is needed, it is developed from scratch using the newest RAD techniques and tools. The big disadvantage of the Rapid Prototyping Model is that the process can be to fast, and, therefore, proper testing (especially security testing) may not be done. The Rapid Prototyping Model is used for graphical user interface (GUI) applications such as web-based applications. Extreme Programming (XP) is a modern incarnation of the Rapid Prototyping Model.
Object-Oriented Model
Object-oriented programming became popular 1990s with the increased use of Smalltalk, C++, and other new object-oriented programming languages. To take full advantage of object-oriented features (i.e. classes, inheritance, methods), the Object-oriented SDLC model was developed. An important feature of Object-oriented (OO) systems is that software objects represent real-world objects. Objects are derived from Classes, and a class hierarchy allows objects to inherit characteristics from parent classes. This allows software object reuse, less coding, encapsulation of functionality, and many other advantages. A major problem that arose with OO programming is that if the Class hierarchy is not properly designed, all the OO advantages disappear. The object-oriented model attempts to properly define and document the Class hierarchy from which all the system objects are created and object interactions are defined. For example, in an accounts payable system for GIAC Bikes, GIAC Bikes is an Object. Spacely Space Sprockets is another Object (of class Supplier). Supplier is a Relationship between GIAC Bikes and Spacely Space Sprockets. A Supplier Class has Attributes such as Name, Address, and so on. The Relationship itself may be considered as an Object, having Attributes like Prime Supplier, and so forth. A Supplier Method may be Pay, Drop, Request Refund, and such. Defining all the application Classes, Methods, Relationships, and Properties is very difficult. The object-oriented SDLC model provides the development team the tools to accomplish this task. The object-oriented SDLC model has these phases that roughly correspond to the traditional SDLC phases noted in brackets: 1. Object-Oriented Requirements Analysis (OORA) [Design Analysis]: This is where classes of objects and the interaction between them are defined. 2. Object-Oriented Analysis (OOA) [Design Analysis]: In terms of objectoriented concepts, understanding, and modeling a particular problem within a problem domain.
3. Object-Oriented Design (OOD) [System Design Specification]: The object is the basic unit of modularity; objects are instantiations of a class. 4. Object-Oriented Programming (OOP) [Programming and Testing]: Emphasizes the employment of objects and methods rather than types or transformations, as in other programming approaches. The Object-oriented SDLC model is characterized by its attempt to model real-world entities (such as company, account, employee) into abstract computer software objects and all the interactions that can take place between those objects.
Other Models
Other SDLC models include Model Driven Development, Chaos Model, Agile Programming Model, and many others. One significant trend in the development of new SDLC models is the integration of software design tools into the programming environment (such as Microsoft Visual Studio, IBM Rational Rose). The design team develops a graphical model of the system, and the tool automatically creates a running application.
Summary
SDLC models are tools that allow the development team to correctly follow the SDLC steps to create software that meets a business need. The SDLC models have evolved as new technology and new research have addressed weaknesses of older models. Ideas have been borrowed and adapted between the various models. The CISSP student should recognize the main SDLC model families of sequential (Waterfall), iterative (Spiral), rapid prototyping (RAD), and object-oriented. The student should recognize the characteristics of top-down and bottom-up development. It is the responsibility of the CISSP to make sure development teams follows an SDLC model so that proper confidentiality, integrity, and availability controls are designed and built into the software application throughout the software life cycle.
Comparing Software Development Life Cycles >> http://www.giac.org/resources/whitepaper/application/257.php Dening and Understanding Security in the Software Development Life Cycle >> http://www.giac.org/resources/whitepaper/application/342.php
SECURITY 519 Web Application Security Workshop From a mere 26 web servers operating in November 1992 growing to well over 100 million web sites today, we have come a long way in web technology over a short period of time. Today, almost every organization has its own web site for conducting business transactions or other critical functions. And for many companies, their online presence has become a major revenue generator. As everyone jumps on the bandwagon to do business on the web, many problems can arise which are directly related to the security aspects of web applications. The adage "where there is money, there is crime" has become true on a daily basis as we see credit cards and other nancial data compromised through web application vulnerabilities. And that is not even the full extent of the problem because web-based malware and worms are still spreading in the wild. Read More >> http://www.sans.org/info/10801
Anda mungkin juga menyukai
- System Development Life Cycle-123Dokumen10 halamanSystem Development Life Cycle-123Tanzir AhmmadBelum ada peringkat
- Software Engineering Lecture 1.1.4Dokumen10 halamanSoftware Engineering Lecture 1.1.4Ashutosh mishraBelum ada peringkat
- SDLC Models-In DetailDokumen27 halamanSDLC Models-In DetailSaumya JoshiBelum ada peringkat
- Software Development Life CycleDokumen5 halamanSoftware Development Life CycleVikash DubeyBelum ada peringkat
- SDLC ModelsDokumen5 halamanSDLC ModelsNobel Education Channel قناة نوبل التعليميةBelum ada peringkat
- Unit 2 SPMDokumen31 halamanUnit 2 SPMSakshi ChauhanBelum ada peringkat
- Chapter 3 Software Process Model-2Dokumen42 halamanChapter 3 Software Process Model-2prasath67Belum ada peringkat
- Software Development Life CycleDokumen5 halamanSoftware Development Life CyclePc HackerBelum ada peringkat
- Software Engineering: SubjectDokumen7 halamanSoftware Engineering: SubjectDibyam DeyBelum ada peringkat
- SDLC 1Dokumen24 halamanSDLC 1Kochappen Ipe KumarBelum ada peringkat
- Prototyping and Spiral: Life Cycle ModelsDokumen6 halamanPrototyping and Spiral: Life Cycle ModelsstudentBelum ada peringkat
- 202-18 SW Software Development ModelsDokumen20 halaman202-18 SW Software Development ModelsarashpreetBelum ada peringkat
- Software Development ModelsDokumen7 halamanSoftware Development ModelsatongashuBelum ada peringkat
- My Unit1Dokumen44 halamanMy Unit1Om MishraBelum ada peringkat
- Software Process ModelsDokumen37 halamanSoftware Process ModelsDalia JoseBelum ada peringkat
- Software EngineeringDokumen23 halamanSoftware EngineeringJaleed MasoodBelum ada peringkat
- UNIT-1 (ISAD) .Image - MarkedDokumen12 halamanUNIT-1 (ISAD) .Image - MarkedJhalakBelum ada peringkat
- Chapter 1 Introduction & Software Development Life Cycle 08.01.2018Dokumen24 halamanChapter 1 Introduction & Software Development Life Cycle 08.01.2018MK MillyBelum ada peringkat
- The Waterfall ModelDokumen9 halamanThe Waterfall Modellaraib sultanBelum ada peringkat
- Student's Undertaking: I Have Been Undertaking That This Is My Original Work and Have Never Been Submitted ElsewhereDokumen13 halamanStudent's Undertaking: I Have Been Undertaking That This Is My Original Work and Have Never Been Submitted ElsewhereMayank SharmaBelum ada peringkat
- AIM:-To Study About Software Development Life Cycle. Software Development Life CycleDokumen42 halamanAIM:-To Study About Software Development Life Cycle. Software Development Life CycleBhaskar NaiduBelum ada peringkat
- SDLCDokumen42 halamanSDLCHarsha VardhanBelum ada peringkat
- SDLC ModelsDokumen4 halamanSDLC ModelsElijah IbsaBelum ada peringkat
- Name: Dharshini S Course: Mba College: Sri Krishna College of Technology Topic: ItDokumen26 halamanName: Dharshini S Course: Mba College: Sri Krishna College of Technology Topic: ItDharshini SelvarajBelum ada peringkat
- Popular SDLC Models Followed in The Industry Lec 2Dokumen30 halamanPopular SDLC Models Followed in The Industry Lec 2UCIZAMBO ITBelum ada peringkat
- Software Development Life CycleDokumen8 halamanSoftware Development Life Cycleapi-320326008Belum ada peringkat
- What Is The Software Development Life Cycle?Dokumen12 halamanWhat Is The Software Development Life Cycle?Rahul JainBelum ada peringkat
- Maliha Rahim b-25781 Sir Asad Sajjad Software Engineering AssignmentDokumen2 halamanMaliha Rahim b-25781 Sir Asad Sajjad Software Engineering AssignmentMaliha RahimBelum ada peringkat
- Assignment Bia OldDokumen12 halamanAssignment Bia OldManmeet KaurBelum ada peringkat
- Waterfall ModelDokumen4 halamanWaterfall ModelAashish Kumar PrajapatiBelum ada peringkat
- Models of SDLC - PPT OriginalDokumen51 halamanModels of SDLC - PPT Originals_coolbugBelum ada peringkat
- SDLC Quick GuideDokumen7 halamanSDLC Quick GuideRajBelum ada peringkat
- SDLCDokumen81 halamanSDLCمحمد احمدBelum ada peringkat
- 4.3. SDLC Models: 4.3.1. Waterfall ModelDokumen5 halaman4.3. SDLC Models: 4.3.1. Waterfall ModelNavya DasariBelum ada peringkat
- Software Engeeinering ProjectDokumen54 halamanSoftware Engeeinering Projectruhi thakurBelum ada peringkat
- Lecture 4Dokumen47 halamanLecture 4Mehul MayankBelum ada peringkat
- Introduction To SE BSNLDokumen60 halamanIntroduction To SE BSNLSudhakar SelvamBelum ada peringkat
- Phases of Software Process ModelsDokumen10 halamanPhases of Software Process ModelsArooj ArifBelum ada peringkat
- SDLCDokumen18 halamanSDLCsadoBelum ada peringkat
- Testing NotesDokumen18 halamanTesting NotesKuldeep AroraBelum ada peringkat
- Requirements Engineering and Management Digital Assignment - 1Dokumen8 halamanRequirements Engineering and Management Digital Assignment - 1Abbas KhanBelum ada peringkat
- Chapter 3 Software Process ModelDokumen49 halamanChapter 3 Software Process Modelsanket0% (1)
- Mbarara University of Science and TechnologyDokumen6 halamanMbarara University of Science and TechnologysedricBelum ada peringkat
- Software Enginering BasicsDokumen8 halamanSoftware Enginering BasicsGhanshyam KumarBelum ada peringkat
- Selection of An Appropriate Project ApproachDokumen18 halamanSelection of An Appropriate Project ApproachomBelum ada peringkat
- SOFTWARE DEVELOPMENT Quiz 2Dokumen22 halamanSOFTWARE DEVELOPMENT Quiz 2Abdul QadeerBelum ada peringkat
- Software Development ModelsDokumen5 halamanSoftware Development ModelsVikasBelum ada peringkat
- SAD ModelsDokumen11 halamanSAD ModelsZhang XinYaBelum ada peringkat
- All Softwer Process ModelsDokumen52 halamanAll Softwer Process ModelsChirag VadhavanaBelum ada peringkat
- Unit 1 TCS 651 DEVOPSDokumen13 halamanUnit 1 TCS 651 DEVOPSAnushka RawatBelum ada peringkat
- Software Process ModelsDokumen47 halamanSoftware Process ModelsKahlea RajkumarBelum ada peringkat
- Software Development Life Cycle PDFDokumen5 halamanSoftware Development Life Cycle PDFAadil latiefBelum ada peringkat
- Describe What Is SDLC. SDLC (Software Development Life Cycle) - Refers To A Methodology With Clearly Defined Processes ForDokumen3 halamanDescribe What Is SDLC. SDLC (Software Development Life Cycle) - Refers To A Methodology With Clearly Defined Processes ForLyco BikoBelum ada peringkat
- SRS For Online Pizza StoreDokumen49 halamanSRS For Online Pizza StoreR_Arpan60% (10)
- SPM Unit-2Dokumen23 halamanSPM Unit-2Suryanarayana seshapuBelum ada peringkat
- IEEE Defines Software Engineering As:: The Term Software Engineering Is Composed of Two Words, Software and EngineeringDokumen8 halamanIEEE Defines Software Engineering As:: The Term Software Engineering Is Composed of Two Words, Software and EngineeringNaeem ShaikhBelum ada peringkat
- 3.1 The Evolutionary Process Models: Software Engineering Third ClassDokumen8 halaman3.1 The Evolutionary Process Models: Software Engineering Third ClassAmit ChauhanBelum ada peringkat
- Definition of Software ModelingDokumen11 halamanDefinition of Software ModelingGeorge Putra7648Belum ada peringkat
- SDLC ModelDokumen11 halamanSDLC ModelTan LopezBelum ada peringkat
- Hunger Games Mini Socratic Seminar2012Dokumen4 halamanHunger Games Mini Socratic Seminar2012Cary L. TylerBelum ada peringkat
- Design Calculation FOR Rigid Pavement/RoadDokumen5 halamanDesign Calculation FOR Rigid Pavement/RoadghansaBelum ada peringkat
- Overview of MEMDokumen5 halamanOverview of MEMTudor Costin100% (1)
- Formula Renault20 Mod00Dokumen68 halamanFormula Renault20 Mod00Scuderia MalatestaBelum ada peringkat
- Swanand 2009Dokumen3 halamanSwanand 2009maverick2929Belum ada peringkat
- Power-Miser 12 Water Heater ManualDokumen32 halamanPower-Miser 12 Water Heater ManualClaudeVanDammBelum ada peringkat
- DJF 41032 Manufacturing Workshop Practice 3 Plastic Lab: Mini Project (Transfer Moulding)Dokumen7 halamanDJF 41032 Manufacturing Workshop Practice 3 Plastic Lab: Mini Project (Transfer Moulding)Lokhman HakimBelum ada peringkat
- Effect of Heater Geometry On The High Temperature Distribution On A MEMS Micro-HotplateDokumen6 halamanEffect of Heater Geometry On The High Temperature Distribution On A MEMS Micro-HotplateJorge GuerreroBelum ada peringkat
- Num Sheet 1Dokumen1 halamanNum Sheet 1Abinash MohantyBelum ada peringkat
- Case Paul Foster Highlights of TarotDokumen76 halamanCase Paul Foster Highlights of TarotTraditionaltarot100% (6)
- Describe an English lesson you enjoyed.: 多叔逻辑口语,中国雅思口语第一品牌 公共微信: ddielts 新浪微博@雅思钱多多Dokumen7 halamanDescribe an English lesson you enjoyed.: 多叔逻辑口语,中国雅思口语第一品牌 公共微信: ddielts 新浪微博@雅思钱多多Siyeon YeungBelum ada peringkat
- STFC-2023 International E - conference-BITDokumen6 halamanSTFC-2023 International E - conference-BITRanilprabhu MBelum ada peringkat
- Warning: Shaded Answers Without Corresponding Solution Will Incur Deductive PointsDokumen1 halamanWarning: Shaded Answers Without Corresponding Solution Will Incur Deductive PointsKhiara Claudine EspinosaBelum ada peringkat
- DICKSON KT800/802/803/804/856: Getting StartedDokumen6 halamanDICKSON KT800/802/803/804/856: Getting StartedkmpoulosBelum ada peringkat
- SKF CMSS2200 PDFDokumen2 halamanSKF CMSS2200 PDFSANTIAGOBelum ada peringkat
- ZH210LC 5BDokumen24 halamanZH210LC 5BPHÁT NGUYỄN THẾ0% (1)
- Plane TrigonometryDokumen545 halamanPlane Trigonometrygnavya680Belum ada peringkat
- Case Study III - MichelinDokumen15 halamanCase Study III - MichelinfreitzBelum ada peringkat
- Sentence Diagramming:: Prepositional PhrasesDokumen2 halamanSentence Diagramming:: Prepositional PhrasesChristylle RomeaBelum ada peringkat
- The Genius of Marie Curie Shohini GhoseDokumen4 halamanThe Genius of Marie Curie Shohini GhoseMarta HrynyovskaBelum ada peringkat
- Workplace Risk Assessment PDFDokumen14 halamanWorkplace Risk Assessment PDFSyarul NizamzBelum ada peringkat
- GoodElearning TOGAF Poster 46 - Adapting The ADMDokumen1 halamanGoodElearning TOGAF Poster 46 - Adapting The ADMFabian HidalgoBelum ada peringkat
- EF3e Intplus Filetest 10aDokumen4 halamanEF3e Intplus Filetest 10aLin Shufen100% (1)
- Three Revolutionary Architects - Boullee, Ledoux, and Lequeu PDFDokumen135 halamanThree Revolutionary Architects - Boullee, Ledoux, and Lequeu PDFTran LeBelum ada peringkat
- PLASSON UK July 2022 Price Catalogue v1Dokumen74 halamanPLASSON UK July 2022 Price Catalogue v1Jonathan Ninapaytan SanchezBelum ada peringkat
- Class I Water Well: DescriptionDokumen10 halamanClass I Water Well: DescriptionJavier Andrés Acevedo GarcíaBelum ada peringkat
- A. Premise Vs Conclusion NotesDokumen8 halamanA. Premise Vs Conclusion NotesEmma PreciousBelum ada peringkat
- Gauss' Law: F A FADokumen14 halamanGauss' Law: F A FAValentina DuarteBelum ada peringkat
- GARCH (1,1) Models: Ruprecht-Karls-Universit at HeidelbergDokumen42 halamanGARCH (1,1) Models: Ruprecht-Karls-Universit at HeidelbergRanjan KumarBelum ada peringkat
- 01 IntroductionDokumen15 halaman01 IntroductionAli FarhatBelum ada peringkat
- $100M Leads: How to Get Strangers to Want to Buy Your StuffDari Everand$100M Leads: How to Get Strangers to Want to Buy Your StuffPenilaian: 5 dari 5 bintang5/5 (18)
- $100M Offers: How to Make Offers So Good People Feel Stupid Saying NoDari Everand$100M Offers: How to Make Offers So Good People Feel Stupid Saying NoPenilaian: 5 dari 5 bintang5/5 (22)
- The Millionaire Fastlane, 10th Anniversary Edition: Crack the Code to Wealth and Live Rich for a LifetimeDari EverandThe Millionaire Fastlane, 10th Anniversary Edition: Crack the Code to Wealth and Live Rich for a LifetimePenilaian: 4.5 dari 5 bintang4.5/5 (88)
- Summary of Noah Kagan's Million Dollar WeekendDari EverandSummary of Noah Kagan's Million Dollar WeekendPenilaian: 5 dari 5 bintang5/5 (1)
- Broken Money: Why Our Financial System Is Failing Us and How We Can Make It BetterDari EverandBroken Money: Why Our Financial System Is Failing Us and How We Can Make It BetterPenilaian: 5 dari 5 bintang5/5 (3)
- 12 Months to $1 Million: How to Pick a Winning Product, Build a Real Business, and Become a Seven-Figure EntrepreneurDari Everand12 Months to $1 Million: How to Pick a Winning Product, Build a Real Business, and Become a Seven-Figure EntrepreneurPenilaian: 4 dari 5 bintang4/5 (2)
- Speaking Effective English!: Your Guide to Acquiring New Confidence In Personal and Professional CommunicationDari EverandSpeaking Effective English!: Your Guide to Acquiring New Confidence In Personal and Professional CommunicationPenilaian: 4.5 dari 5 bintang4.5/5 (74)
- The Coaching Habit: Say Less, Ask More & Change the Way You Lead ForeverDari EverandThe Coaching Habit: Say Less, Ask More & Change the Way You Lead ForeverPenilaian: 4.5 dari 5 bintang4.5/5 (186)
- Summary of Thinking, Fast and Slow: by Daniel KahnemanDari EverandSummary of Thinking, Fast and Slow: by Daniel KahnemanPenilaian: 4 dari 5 bintang4/5 (117)
- The First Minute: How to start conversations that get resultsDari EverandThe First Minute: How to start conversations that get resultsPenilaian: 4.5 dari 5 bintang4.5/5 (57)