Moac 70-687 L18 RDC
Diunggah oleh
mparmer3Judul Asli
Hak Cipta
Format Tersedia
Bagikan dokumen Ini
Apakah menurut Anda dokumen ini bermanfaat?
Apakah konten ini tidak pantas?
Laporkan Dokumen IniHak Cipta:
Format Tersedia
Moac 70-687 L18 RDC
Diunggah oleh
mparmer3Hak Cipta:
Format Tersedia
Lesson 18: Configuring
Remote Connections
MOAC 70-687: Configuring Windows 8
Using BranchCache
Lesson 18: Configuring Remote Connections
2013 John Wiley & Sons, Inc. 2
BranchCache
BranchCache is a feature in Windows 8 and
Windows Server 2012 that enables networks
with computers at remote locations to
conserve bandwidth by storing frequently
accessed files on local drives.
2013 John Wiley & Sons, Inc.
3
Understanding Network
Infrastructure Requirements
To use BranchCache, you must have
o A server running Windows Server 2008 R2 or
Windows Server 2012 at the main office
o Computers running Windows Server 2008 R2,
Windows Server 2012, Windows 7, or Windows 8
at the branch office
2013 John Wiley & Sons, Inc.
4
Understanding BranchCache
Communications
This is the BranchCache communications
process:
1. Client request (BranchCache)
2. Server reply (metadata)
3. Client cache check
4. Caching computer reply
5. Client request (non-BranchCache)
6. Server reply (data)
7. Client data cache
2013 John Wiley & Sons, Inc.
5
Understanding Content
Information Versions
Any BranchCache implementation that
includes one or more computers running
Windows Server 2008 R2 or Windows 7 in any
role is said to use content information version
1, or V1.
If all the computers involved in the
BranchCache transactions are running
Windows Server 2012 or Windows 8, the
implementation can use content
information version 2, or V2.
2013 John Wiley & Sons, Inc.
6
Understanding Content
Information Versions
The Hash Version support for BranchCache
policy setting
2013 John Wiley & Sons, Inc. 7
Configuring BranchCache
Settings
To implement BranchCache on your
network, install the appropriate modules on
your server(s) and configure Group Policy
settings on both servers and clients.
BranchCache requires a minimum of one
content server and one or more branch
office workstations.
You can install additional content servers at
any location that serves files to branch
offices.
2013 John Wiley & Sons, Inc.
8
Configuring a Content
Server
Once you have installed the required
BranchCache modules, configure a Group
Policy setting called Hash Publication for
BranchCache.
This setting is located in the Computer
Configuration\Policies\Administrative
Templates\Network\Lanman Server node of a
Group Policy object (GPO) or in Local
Computer Policy.
The Hash Publication for BranchCache setting
enables the server to respond to file requests
from BranchCache clients with metadata
instead of the files themselves.
2013 John Wiley & Sons, Inc.
9
Configuring a Content Server
The Hash Publication for BranchCache setting
in Group Policy
2013 John Wiley & Sons, Inc. 10
Configuring a Content Server
A shares Properties sheet in Windows Server 2012
Server Manager
2013 John Wiley & Sons, Inc. 11
Configuring BranchCache
Clients
To configure BranchCache clients, configure
the appropriate Group Policy settings.
These are found in the Computer
Configuration\Policies\Administrative
Templates\Network\BranchCache node of
a GPO or in Local Computer Policy.
2013 John Wiley & Sons, Inc.
12
Configuring BranchCache Clients
The BranchCache settings in Group Policy
2013 John Wiley & Sons, Inc. 13
BranchCache Group
Policy Settings
These are the BranchCache Group Policy
settings:
o Turn on BranchCache
o Set BranchCache Distributed Cache mode
o Set BranchCache Hosted Cache mode
o Enable Automatic Hosted Cache Discovery by
Service Connection Point
o Configure Hosted Cache Servers
o Configure BranchCache for network files
o Set percentage of disk space used for client
computer cache
o Set age for segments in the data cache
o Configure Client BranchCache Version Support
2013 John Wiley & Sons, Inc.
14
Configuring a Hosted
Cache Mode Server
To use hosted cache mode on your branch
office network, you must have a server running
Windows Server 2012 or Windows Server 2008 R2
with the BranchCache feature installed.
You must also configure the Turn on
BranchCache and Set BranchCache Hosted
Cache mode Group Policy settings.
The hosted cache mode server must also have
a digital certificate issued by a certification
authority (CA) that the BranchCache clients
trust.
2013 John Wiley & Sons, Inc.
15
Using Remote Network
Connections
Lesson 18: Configuring Remote Connections
2013 John Wiley & Sons, Inc. 16
Understanding Virtual
Private Networking
A dial-up connection is a dedicated link
between the two modems that remains in
place during the entire session.
The client and the server establish a Point-to-
Point Protocol (PPP) connection, during which
the server authenticates the client and the
computers negotiate a set of communication
parameters they have in common.
In a virtual private network (VPN) connection,
the remote client and the remote access server
are both connected to the Internet, using local
service providers.
2013 John Wiley & Sons, Inc.
17
Understanding Virtual Private
Networking
A dial-up remote access connection
2013 John Wiley & Sons, Inc. 18
Understanding Virtual Private
Networking
A VPN remote access connection
2013 John Wiley & Sons, Inc. 19
Tunneling
In the tunneling process, the two computers
establish a PPP connection, just as they would in a
dial-up connection, but instead of transmitting the
PPP packets over the Internet as they are, they
encapsulate the packets again using one of the
VPN protocols supported by the Windows operating
systems.
The original PPP data packet generated by the
computer consists of an network layer IP datagram,
encapsulated within a data-link layer PPP frame.
The system then encapsulates the entire frame in
another IP datagram, which the VPN protocol
encrypts and encapsulates one more time, for
transmission over the network.
2013 John Wiley & Sons, Inc.
20
Tunneling
VPN protocol encapsulation
2013 John Wiley & Sons, Inc. 21
VPN Protocols
These are the VPN protocols that Windows 8
supports:
o Point-to-Point Tunneling Protocol (PPTP)
o Layer 2 Tunneling Protocol (L2TP)
o Secure Socket Tunneling Protocol (SSTP)
o Internet Key Exchange, Version 2 (IKEv2)
2013 John Wiley & Sons, Inc.
22
Point-to-Point Tunneling
Protocol (PPTP)
The oldest and least secure of the VPN protocols, PPTP
takes advantage of the authentication, compression,
and encryption mechanisms of PPP, tunneling the PPP
frame within a Generic Routing Encapsulation (GRE)
header and encrypting it with Microsoft Point-to-Point
Encryption (MPPE), using encryption keys generated
during the authentication process.
For authentication, PPTP supports only the Microsoft
Challenge Handshake Authentication Protocol version
1 (MS-CHAP v1), Microsoft Challenge Handshake
Authentication Protocol version 2 (MS-CHAP v2),
Extensible Authentication Protocol (EAP), or Protected
Extensible Authentication Protocol (PEAP).
2013 John Wiley & Sons, Inc.
23
Layer 2 Tunneling
Protocol (L2TP)
L2TP relies on the IP security extensions (IPsec) for
encryption and performs a double encapsulation.
The system adds an L2DP header to the PPP frame and
packages it with the User Datagram Protocol (UDP).
Then it encapsulates the UDP datagram with the IPsec
Encapsulating Security Payload (ESP) protocol,
encrypting the contents using the Data Encryption
Standard (DES) or Triple DES (3DES) algorithm, with
encryption keys generated during IPsecs Internet Key
Exchange (IKE) negotiation process.
L2TP/IPsec can use certificates or preshared keys for
authentication, although administrators typically use
the latter only for testing.
2013 John Wiley & Sons, Inc.
24
Secure Socket
Tunneling Protocol (SSTP)
Introduced in Windows Server 2008 and
supported only by clients running Windows
Vista SP1 or later, SSTP encapsulates PPP
traffic using the Secure Sockets Layer (SSL)
protocol supported by virtually all web
servers.
SSTP uses certificates for authentication, with
the EAP-TLS authentication protocol, and in
addition to data encryption, provides
integrity checking and enhanced key
negotiation services.
2013 John Wiley & Sons, Inc.
25
Internet Key Exchange,
Version 2 (IKEv2)
Internet Key Exchange Version 2 (IKEv2):
Was first introduced in Windows 7 and
Windows Server 2008 R2.
Uses TCP port 500.
Provides support for IPv6 and the new VPN
Reconnect feature, as well as
authentication by EAP, using PEAP, EAP-
MSCHAPv2, or smart cards.
Does not support the older authentication
mechanisms, such as PAP and CHAP.
2013 John Wiley & Sons, Inc.
26
Authenticating
Remote Users
In Windows 8, you configure the
authentication method a VPN connection
uses on the Security tab of the connections
Properties sheet.
These are the options:
o Use Extensible Authentication Protocol (EAP)
o Allow these protocols
2013 John Wiley & Sons, Inc.
27
Authenticating Remote Users
The Security tab of a connections Properties sheet
2013 John Wiley & Sons, Inc. 28
Creating a VPN
Connection
To connect a computer running Windows 8
to a remote access server, you must create
a new VPN or dial-up connection.
In Windows 8, the Network Connections
window contains a connection for every
network interface adapter installed in the
computer.
The Windows installation program creates
these connections automatically, but to
connect to a dial-up or VPN server, you must
create additional connections manually.
2013 John Wiley & Sons, Inc.
29
Create a VPN Connection
The Choose a connection option page
2013 John Wiley & Sons, Inc. 30
Create a VPN Connection
The How do you want to connect? page
2013 John Wiley & Sons, Inc. 31
Create a VPN Connection
The Type the Internet address to connect to page
2013 John Wiley & Sons, Inc. 32
Create a VPN Connection
The Networks pane
2013 John Wiley & Sons, Inc. 33
Create a VPN Connection
The Network Authentication pane
2013 John Wiley & Sons, Inc. 34
Using VPN Reconnect
Windows 8 includes a feature called VPN
Reconnect, based on the IKEv2 Mobility and
Multihoming (MOBIKE) protocol, which enables
a computer to reconnect to a VPN server
automatically, after an interruption as long as
eight hours.
To configure VPN Reconnect, you open the
Properties sheet for a VPN connection, click the
Security tab, and click Advanced settings.
In the Advanced Properties dialog box that
appears, click the IKEv2 tab and select the
Mobility check box.
2013 John Wiley & Sons, Inc.
35
Using VPN Reconnect
Enabling VPN Reconnect
2013 John Wiley & Sons, Inc. 36
Network Access
Protection (NAP)
NAP is a component of the Network Policy
and Access Services role in Windows Server
2012, Windows Server 2008 R2, and Windows
Server 2008
It is designed to prevent potentially
dangerous clientslocal or remotefrom
connecting to the network.
2013 John Wiley & Sons, Inc.
37
Creating a Broadband
Connection
While many Internet Service Providers (ISPs)
offer broadband services that provide
always on connections to the Internet,
some still offer metered connections that
require users to log on and log off.
Windows 8 provides wizard options that
enable you to create a broadband
connection that you can activate and
deactivate at will.
2013 John Wiley & Sons, Inc.
38
Create a Broadband Connection
The Type the information from your Internet Service
Provider (ISP) page
2013 John Wiley & Sons, Inc. 39
Create a Broadband Connection
The The connection to the Internet is ready to use page
2013 John Wiley & Sons, Inc. 40
Create a Broadband Connection
The Networks display
2013 John Wiley & Sons, Inc. 41
Using Remote Desktop
Windows Server 2012 includes a role called
Remote Desktop Services, which provides
clients with access to server resources in a
variety of ways.
The Remote Desktop Session Host role
service functions much like the Remote
Desktop Services service in Windows 8,
except that it can provide multiple
(licensed) users with access to the server
desktop.
2013 John Wiley & Sons, Inc.
42
DirectAccess
DirectAccess is a feature in Windows 8 and
Windows Server 2012 that enables remote
users to automatically connect to the
company network whenever they have
Internet access.
2013 John Wiley & Sons, Inc.
43
DirectAccess Benefits
Designed as a replacement for VPNs,
DirectAccess eliminates the need for client users
to manually establish wide area connections to
their networks.
DirectAccess provides many other benefits to
users and administrators, including:
o Bidirectional
o Encrypted
o Authenticated
o Authorized
o Verified
2013 John Wiley & Sons, Inc.
44
Understanding the
DirectAccess Infrastructure
The DirectAccess implementation in
Windows 8 and Windows Server 2012
includes a number of improvements over
the Windows 7/Windows Server 2008 R2
version, including the ability for DirectAccess
to coexist on the same server with the
Routing and Remote Access Service (RRAS)
that provides VPN server services.
2013 John Wiley & Sons, Inc.
45
Understanding the
DirectAccess Infrastructure
DirectAccess is heavily reliant on IPv6. IPv6 is not
yet deployed universally, however. Many
networks still rely on IPv4, most notably the
Internet. Therefore, DirectAccess also relies on a
variety of transition technologies that enable
IPv4 networks to carry IPv6 traffic:
o 6to4
o Teredo
o IP-HTTPS
o Intra-Site Automatic Tunnel Addressing Protocol
(ISATAP)
o Network Address TranslationProtocol Translation
(NAT-PT)
2013 John Wiley & Sons, Inc.
46
DirectAccess and IPsec
IPsec is a collection of IP extensions that
provide additional security for network
communications.
DirectAccess relies on IPsec for
authentication of users and computers and
for encryption of the data exchanged by
clients and servers.
2013 John Wiley & Sons, Inc.
47
DirectAccess and IPsec
DirectAccess: The end-to-end access model
2013 John Wiley & Sons, Inc. 48
DirectAccess and IPsec
DirectAccess: The end-to-edge access model
2013 John Wiley & Sons, Inc. 49
DirectAccess and IPsec
DirectAccess: The modified end-to-edge access model
2013 John Wiley & Sons, Inc. 50
DirectAccess Server
Requirements
The DirectAccess server must be running
Windows Server 2012 and must also have:
o Membership in an AD DS domain
o At least one network interface adapter installed
o A direct connection to the Internet (that does
not use NAT or a similar technology)
o A direct connection to the company intranet
o The Group Policy Management feature installed
2013 John Wiley & Sons, Inc.
51
DirectAccess Client
Requirements
DirectAccess clients must be running
Windows 8 Enterprise, Windows 7 Enterprise
or Ultimate, Windows Server 2012, or
Windows Server 2008 R2, and they must be
joined to the same domain as the
DirectAccess server.
You must deploy the client computers on
the company network first, so they can join
the domain and receive certificates and
Group Policy settings, before you send them
out into the field.
2013 John Wiley & Sons, Inc.
52
Establishing a
DirectAccess Connection
These are the individual steps of the connection process:
1. The client attempts to connect to a designated network detection
server on the intranet.
2. The client connects to the DirectAccess server on the host network
using IPv6.
3. The client and the DirectAccess server authenticate each other
using their computer certificates.
4. The client establishes a second connection through the
DirectAccess server to the domain controller and performs a
standard AD DS user authentication, using NTLMv2 credentials and
the Kerberos V5 authentication protocol.
5. The DirectAccess server uses AD DS group memberships to
authorize the client computer and user to access the intranet.
6. lf required, the client submits a health certificate to a Network
Policy Server (NPS) on the host network, to verify its compliance with
existing policies.
7. The client begins to access application servers and other resources
in the intranet, using the DirectAccess server as a gateway.
2013 John Wiley & Sons, Inc.
53
Configuring DirectAccess
The process of installing and configuring
DirectAccess is much simpler in Windows
Server 2012, requiring only that you install the
Remote Access role and run a simple
configuration wizard.
The wizard then configures the server and
creates the Group Policy settings needed to
configure the DirectAccess clients.
2013 John Wiley & Sons, Inc.
54
Configuring DirectAccess
The DirectAccess prerequisite check
2013 John Wiley & Sons, Inc. 55
Configuring DirectAccess
The Remote Access Management Console
2013 John Wiley & Sons, Inc. 56
Anda mungkin juga menyukai
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceDari EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RacePenilaian: 4 dari 5 bintang4/5 (895)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeDari EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifePenilaian: 4 dari 5 bintang4/5 (5794)
- Shoe Dog: A Memoir by the Creator of NikeDari EverandShoe Dog: A Memoir by the Creator of NikePenilaian: 4.5 dari 5 bintang4.5/5 (537)
- Grit: The Power of Passion and PerseveranceDari EverandGrit: The Power of Passion and PerseverancePenilaian: 4 dari 5 bintang4/5 (588)
- The Yellow House: A Memoir (2019 National Book Award Winner)Dari EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Penilaian: 4 dari 5 bintang4/5 (98)
- The Little Book of Hygge: Danish Secrets to Happy LivingDari EverandThe Little Book of Hygge: Danish Secrets to Happy LivingPenilaian: 3.5 dari 5 bintang3.5/5 (400)
- Never Split the Difference: Negotiating As If Your Life Depended On ItDari EverandNever Split the Difference: Negotiating As If Your Life Depended On ItPenilaian: 4.5 dari 5 bintang4.5/5 (838)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureDari EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FuturePenilaian: 4.5 dari 5 bintang4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryDari EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryPenilaian: 3.5 dari 5 bintang3.5/5 (231)
- Rise of ISIS: A Threat We Can't IgnoreDari EverandRise of ISIS: A Threat We Can't IgnorePenilaian: 3.5 dari 5 bintang3.5/5 (137)
- The Emperor of All Maladies: A Biography of CancerDari EverandThe Emperor of All Maladies: A Biography of CancerPenilaian: 4.5 dari 5 bintang4.5/5 (271)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaDari EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaPenilaian: 4.5 dari 5 bintang4.5/5 (266)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersDari EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersPenilaian: 4.5 dari 5 bintang4.5/5 (345)
- On Fire: The (Burning) Case for a Green New DealDari EverandOn Fire: The (Burning) Case for a Green New DealPenilaian: 4 dari 5 bintang4/5 (74)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyDari EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyPenilaian: 3.5 dari 5 bintang3.5/5 (2259)
- Team of Rivals: The Political Genius of Abraham LincolnDari EverandTeam of Rivals: The Political Genius of Abraham LincolnPenilaian: 4.5 dari 5 bintang4.5/5 (234)
- The Unwinding: An Inner History of the New AmericaDari EverandThe Unwinding: An Inner History of the New AmericaPenilaian: 4 dari 5 bintang4/5 (45)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreDari EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You ArePenilaian: 4 dari 5 bintang4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)Dari EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Penilaian: 4.5 dari 5 bintang4.5/5 (121)
- Her Body and Other Parties: StoriesDari EverandHer Body and Other Parties: StoriesPenilaian: 4 dari 5 bintang4/5 (821)
- Cisco IOS RouterDokumen7 halamanCisco IOS RouterKomaram PuliBelum ada peringkat
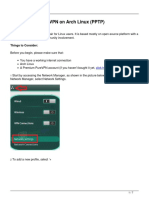
- Arch Linux PPTPDokumen7 halamanArch Linux PPTPdougBelum ada peringkat
- Configure A PPTP VPN Server On Mikrotik Routeros: Step 1: Create VPN PoolDokumen8 halamanConfigure A PPTP VPN Server On Mikrotik Routeros: Step 1: Create VPN PoolSazzad Hasan AkashBelum ada peringkat
- VPN Remote Access 2ndeditionDokumen246 halamanVPN Remote Access 2ndeditionMilton ReyesBelum ada peringkat
- Draytek ConfigDokumen4 halamanDraytek ConfigThu Hiền PhạmBelum ada peringkat
- Cisco IOS Firewall OverviewDokumen8 halamanCisco IOS Firewall Overviewomar ayissaBelum ada peringkat
- Virtual Lans (Vlan) and Virtual Private Networks (VPN)Dokumen16 halamanVirtual Lans (Vlan) and Virtual Private Networks (VPN)kass_ecsBelum ada peringkat
- IPsec - VPN - After EditDokumen71 halamanIPsec - VPN - After EditOSAMA SABRABelum ada peringkat
- VPN Term PaperDokumen11 halamanVPN Term PaperAditriBelum ada peringkat
- f8x34 Series Router User ManualDokumen100 halamanf8x34 Series Router User ManualCocofourfaithBelum ada peringkat
- CS 265 Virtual Private Networks (VPN) Submitted by Aparna ChilukuriDokumen7 halamanCS 265 Virtual Private Networks (VPN) Submitted by Aparna ChilukuriMartin ForthewinBelum ada peringkat
- Information Technology Solved Mcqs PDFDokumen9 halamanInformation Technology Solved Mcqs PDFaniketgunjalBelum ada peringkat
- Using Penetration Testing To Discover VP PDFDokumen6 halamanUsing Penetration Testing To Discover VP PDFDeeapk RajuBelum ada peringkat
- Modem Telefonica Watson SHDSL Router ManualDokumen47 halamanModem Telefonica Watson SHDSL Router Manualrangel.denisBelum ada peringkat
- Tl-r600vpn (Un) 4.0 DatasheetDokumen4 halamanTl-r600vpn (Un) 4.0 DatasheetGabriel Morales de PoolBelum ada peringkat
- Virtual Private Network: Project ReportDokumen80 halamanVirtual Private Network: Project ReportAnirudh KvBelum ada peringkat
- Lecture 5a - Virtual Private NetworksDokumen33 halamanLecture 5a - Virtual Private NetworksHenry ChipindaBelum ada peringkat
- CCIE Security Practice LabsDokumen552 halamanCCIE Security Practice Labsd33bo78Belum ada peringkat
- Schedule: Vahid Shahbazian Fard Jahromy WWW - Learnmikrotik.Ir ©learnmikrotik - Ir 2014Dokumen22 halamanSchedule: Vahid Shahbazian Fard Jahromy WWW - Learnmikrotik.Ir ©learnmikrotik - Ir 2014Giannis Orfanos100% (1)
- Nokia 99Dokumen167 halamanNokia 99Ali HumayunBelum ada peringkat
- Coursework 1 B00297486Dokumen12 halamanCoursework 1 B00297486John GibsonBelum ada peringkat
- PAIF On Raspberry PiDokumen29 halamanPAIF On Raspberry PiAiae Cadiz MadroneroBelum ada peringkat
- 1757 ReadingDokumen18 halaman1757 ReadingTarik ShiguteBelum ada peringkat
- FortiGate PPTP VPN User Guide Version 3.0 MR5Dokumen32 halamanFortiGate PPTP VPN User Guide Version 3.0 MR5Kim Chua LeeBelum ada peringkat
- Certified Network Security Specialist CNSS QuestionsDokumen14 halamanCertified Network Security Specialist CNSS QuestionsKaroBelum ada peringkat
- How To Configure A Firewall For Domains and Trusts (KB179442)Dokumen4 halamanHow To Configure A Firewall For Domains and Trusts (KB179442)AldineYapBelum ada peringkat
- Seminar Report On VIRTUAL PRIVATE NETWORKDokumen38 halamanSeminar Report On VIRTUAL PRIVATE NETWORKnjpatel943% (7)
- Explanation: Frequency Hopping Spread Spectrum (FHSS) Systems Use Frequency Diversity (ChangingDokumen28 halamanExplanation: Frequency Hopping Spread Spectrum (FHSS) Systems Use Frequency Diversity (Changingyerima1Belum ada peringkat
- Tutorial Mikrotik VPNDokumen10 halamanTutorial Mikrotik VPNOki100% (1)
- Step-by-Step Guide For Setting Up A PPTP-based Site-to-Site VPN Connection in A Test LabDokumen31 halamanStep-by-Step Guide For Setting Up A PPTP-based Site-to-Site VPN Connection in A Test LabMelvim Chang BartolomeBelum ada peringkat